 Table of Contents
Table of Contents
- What is the GLBA?
- About the GLBA
- Who Should Comply with the GLBA?
- What Are the GLBA Rules?
- How to Comply with the GLBA
-
GLBA Frequently Asked Questions
- What does GLBA stand for?
- What is the purpose of the GLBA?
- What are the main sections of the GLBA?
- What are some GLBA examples?
- Who does the GLBA protect?
- What does the GLBA protect?
- How do you comply with the GLBA?
- Who enforces GLBA compliance?
- Who should comply with the GLBA?
- How does the FAST Act affect GLBA?
- How is the FCRA related to GLBA?
What is the GLBA?
The Gramm-Leach-Bliley Act (GLBA) is a U.S. federal law requiring financial institutions to protect the privacy, confidentiality, and security of consumer financial information. Originally published in 1999 and enforced since 2001, the GLBA is still mandatory for most financial institutions today.
But, for many, GLBA compliance can also be complex. Simply figuring out what financial data it covers can be challenging—let alone securing that information across multiple systems and monitoring third-party vendors, all while keeping pace with ongoing risk management activities.
To help all financial institutions comply with GLBA in a manageable way, the GLBA organizes requirements for financial institutions under three main sections or “rules.”
The GLBA’s rules are:
- The Privacy Rule: Institutions must inform customers how they collect, use, and share financial information and offer options to limit sharing.
- The Safeguards Rule: Institutions must create and follow a plan to protect customer information from breaches and unauthorized access.
- The Pretexting Rule: Individuals and institutions must not use false or dishonest methods to trick people into giving out their financial information.
Which GLBA rules and requirements your institution needs to meet will ultimately depend on its size, complexity, and role in handling consumer financial data. But one thing is certain: if your organization handles consumer financial data, it probably needs to be at least partially GLBA-compliant.
Fortunately, we’re here to help you get started. This guide is a useful resource for all financial institutions covered under the GLBA. So whether you’re new to the GLBA, looking to freshen up your compliance software, or need a total information security program overhaul—you’re in the right place.
Still with us? Get ready to become a GLBA compliance expert in 3… 2… 1…🚀
About the GLBA
The GLBA, also known as the Financial Services Modernization Act, was signed into law by President Clinton in 1999 with three simple goals: supporting modernization, stimulating competition, and protecting consumers. More than 25 years later, in 2025, it’s still an important information security and data privacy regulation for financial institutions in the U.S.
History of the GLBA
But the story of the GLBA began decades before its creation with the Glass-Steagall Act of 1933. Also called the Banking Act, this law effectively separated commercial and investment financial services. Ultimately, it was intended to reduce the risky financial practices leading up to the Great Depression and to rebuild trust in the American financial system.
Yet, as the financial industry grew and consumer needs changed, many of its restrictions were relaxed to avoid becoming outdated. By the 1990s, some financial institutions even started offering combined services despite the law in anticipation of inevitable change. The Citigroup merger in 1998, for example, violated the Bank Holding Company Act (BHCA) but was given a two-year exception, assuming the law would change.
Although its purpose has evolved over time, the GLBA’s long-lasting impact on the American financial system is perhaps most obvious in two critical areas: data privacy and security.
Just one year later, in 1999, the GLBA was signed into effect. Although its purpose has evolved over time, the GLBA’s long-lasting impact on the American financial system is perhaps most obvious in two critical areas: data privacy and security. More specifically, GLBA’s Title V: Privacy reimagined data privacy requirements in the American financial industry.
GLBA timeline
Here’s a timeline summarizing important GLBA developments:
- 1999: The GLBA is signed into law, repealing parts of the Glass-Steagall Act and introducing key privacy and security provisions for financial institutions.
- 2001: The Safeguards Rule is issued by the FTC, requiring financial institutions to develop, implement, and maintain an information security program.
- 2003: The Safeguards Rule becomes enforceable.
- 2011: The Dodd-Frank Act transfers most GLBA rule-making authority to the CFPB.
- 2021: The FTC updates the Safeguards Rule (the Final Rule) in response to evolving cybersecurity threats.
- 2023: The Final Rule becomes effective, and the FTC issues the Breach Notification Rule.
- 2024: The Breach Notification Rule takes effect, requiring financial institutions to report data breaches impacting 500+ customers within 30 days.
Who Should Comply with the GLBA?
Today, all covered financial institutions (as defined by the Bank Holding Company Act) must comply with the GLBA—including traditional financial institutions like banks, credit unions, investment firms, mortgage lenders, insurance companies, and certain non-traditional financial service providers like higher education organizations—so long as they are “significantly engaged” in financial activities and handle consumers’ nonpublic personal information (NPI).
NPI, or personal information not available in public records, includes any personally identifiable financial data provided by consumers or collected by institutions, like account numbers, transaction histories, loan records, or social security numbers, to name a few.
Financial institutions that must comply with the GLBA include:
- Banks and credit unions
- Mortgage lenders and brokers
- Insurance companies
- Investment firms and advisors
- Title IV higher education institutions
- Tax preparation services
- Money transfer services
- Real estate settlement providers
Non-traditional financial institutions may be especially likely to find GLBA compliance challenging. Most of the time, that’s because they lack the security infrastructure required of traditional financial institutions under regulations like the Bank Secrecy Act (BSA), the Fair Credit Reporting Act (FCRA), and the Sarbanes-Oxley Act (SOX). Like the GLBA, these regulations impose strict requirements for data security, transaction monitoring, and consumer privacy—areas where non-traditional institutions have not historically been held to the same standards as their traditional counterparts.
Who enforces GLBA compliance?
Enforcing GLBA compliance are multiple federal and state regulatory agencies, including the Consumer Financial Protection Bureau (CFPB), the Federal Trade Commission (FTC), the Office of the Comptroller of the Currency (OCC), the Securities and Exchange Commission (SEC), and the Commodity Futures Trading Commission (CFTC).
Enforcing GLBA compliance are multiple federal and state regulatory agencies.
Although GLBA enforcement responsibilities were once shared among other agencies, too—including the Board of Governors of the Federal Reserve System, the Federal Deposit Insurance Corporation, the Office of Thrift Supervision, and the National Credit Union Administration—rule-making power for most of the GLBA was transferred to the CFTC when the Dodd-Frank Wall Street Reform and Consumer Protection Act (Dodd-Frank Act) was enacted in 2011.
What are the consequences of GLBA non-compliance?
The consequences of GLBA non-compliance are not always straightforward. Although many online sources claim specific penalties and fines for general GLBA non-compliance, there is no direct evidence to support this aside from the FTC’s published court documents.
The consequences of GLBA non-compliance are not always straightforward.
Under the GLBA’s Privacy Rule, for instance, which does impose criminal penalties for violations of obtaining or disclosing NPI under false pretenses, fines can reach $100,000 per violation for financial institutions and $10,000 per violation and/or imprisonment for up to five years for individuals.
The Safeguards Rule, on the other hand, does not explicitly specify fines for non-compliance. Instead, compliance with the Safeguards Rule is examined on a case-by-case basis. For the most accurate projection of non-compliance consequences, we recommend reviewing actual complaints or legal cases brought against institutions like yours.
Note: GLBA compliance does not supersede often stricter state data privacy laws, which could remove exemptions for data covered by the GLBA in the near future.
What are some examples of GLBA non-compliance enforcement?
Examples of GLBA non-compliance enforcement action can be challenging to unearth due to the sensitivity of their nature. With some digging, however, you can find some recent examples of GLBA non-compliance. Fortunately, we’ve done the dirty work for you.
Examples of non-compliance enforcement for GLBA include:
- Greystar (2025): The FTC issued a complaint against this rental property manager after it violated the FTC Act, the GLBA, and the Colorado Consumer Protection Act by advertising deceptive costs in multiple venues and using those ads to obtain consumer financial information via inquiry forms.
- Jonathan Braun (2023): A federal court entered a $20.3 million judgment against the merchant cash advance operator in the first jury trial ever conducted by the FTC after he knowingly deceived small businesses about how much funding his small business funding company would provide and collect.
- Ascension Data & Analytics (2021): The FTC ordered this Texas-based mortgage industry data analytics firm to strengthen its security safeguards and conduct biennial assessments of its data security program in line with GLBA after a vendor, OpticsML, stored encrypted documents containing sensitive consumer financial information on a cloud-based server without access controls.
Beyond compliance, GLBA sends a clear message to consumers: We care about the security and privacy of our consumers’ financial data. Because GLBA compliance isn’t just about checking boxes to meet legal requirements or avoiding fines and criminal penalties—it’s about doing everything you can to protect those who have entrusted your business with their most sensitive information.
GLBA compliance is about doing everything you can to protect those who have entrusted your business with their most sensitive information.
Note: Most regulatory agencies—including the CFPB, FTC, OCC, SEC, and CFTC—publish legal documentation for enforcement actions online.
What Are the GLBA Rules?
The GLBA is organized into three “rules,” or primary obligations financial institutions must meet for GLBA compliance: the Privacy Rule, the Safeguards Rule, and the Pretexting Rule. Attempting to understand these rules and identifying the right requirements for your institution are some of the very first proactive steps you can take to prepare for GLBA compliance (hint: you’re in the right place).
Next, let’s take a closer look at the three GLBA rules so you can figure out which might apply to you.

What is the GLBA Privacy Rule?
The Privacy Rule, or Title V of the GLBA, requires financial institutions to clearly explain how they collect, use, and share sensitive financial information so customers and consumers can make informed decisions about their data. Here, transparency and consent are key—institutions must disclose their data-sharing practices and give customers explicit control over how their information is shared.
Here, transparency and consent are key—institutions must disclose their data-sharing practices and give customers explicit control over how their information is shared.
Key requirements for the Privacy Rule include:
- Privacy Notices: Institutions must provide clear, easy-to-understand notices when a customer relationship begins and annually thereafter. These notices must explain what data is collected, how it’s used, and whether it’s shared with third parties.
- Opt-Out Notices: Institutions must let customers and consumers opt out of sharing their financial data with nonaffiliated third parties, like marketing companies.
Note: Financial institutions can use the FTC’s final model privacy notice form to comply with some of these requirements.
The Privacy Rule also limits how nonaffiliated third parties receiving NPI from financial institutions can reuse and re-disclose that information, depending on how it was disclosed. And it prohibits financial institutions from sharing account numbers, access numbers, or codes for marketing purposes.
There are some exceptions to the GLBA privacy notice requirements, too. Specifically, financial institutions can share NPI without permission in certain cases—if it’s the financial institution’s third-party service provider, for instance—but must disclose these information-sharing practices to consumers. Additionally, some financial institutions can use an alternative method for annual privacy notices if they meet certain requirements.
Note: Check out the FTC’s How to Comply with the Privacy Rule guide for an even deeper dive.
What is the GLBA Safeguards Rule?
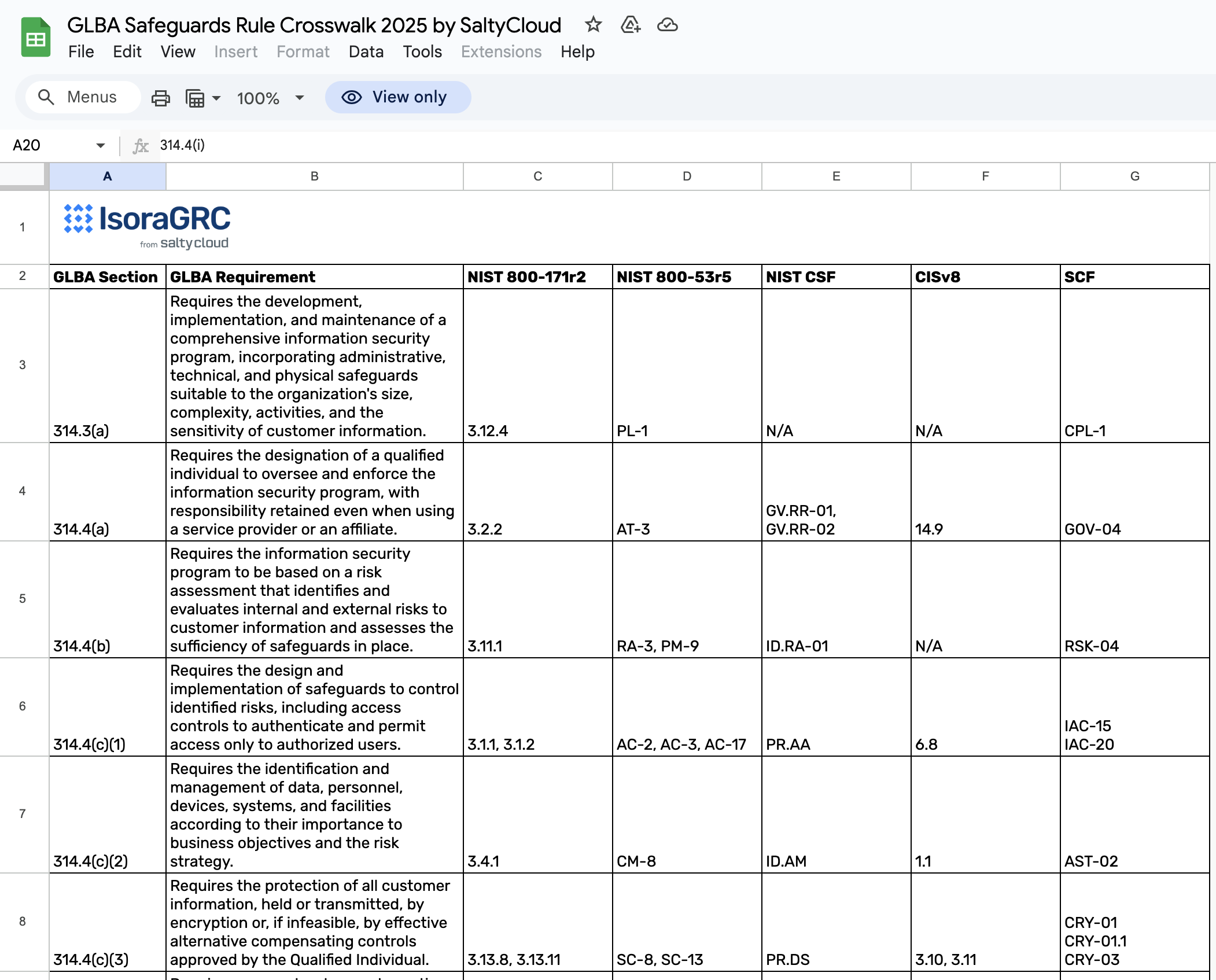
The Safeguards Rule requires financial institutions to develop and implement a written security plan to protect the confidentiality of sensitive financial information from data breaches, unauthorized access, and cyber threats. Here, the focus is security—financial institutions must implement a combination of administrative, technical, and physical safeguards to protect their customers’ information. Under the GLBA Safeguards Rule, information security programs must include the following 10 elements to be compliant.
Here, the focus is security—financial institutions must implement a combination of administrative, technical, and physical safeguards to protect their customers’ information.
Key elements of an information security program under the Safeguards Rule:
- Qualified Individual: Institutions must designate a qualified individual to implement and supervise the information security program.
- Risk Assessments: Institutions must conduct periodic, written risk assessments to identify and evaluate risks.
- Safeguards: Institutions must design and implement safeguards to mitigate the risks identified in the risk assessment.
- Testing and Monitoring: Institutions must regularly test and monitor the effectiveness of safeguards.
- Employee Training: Institutions must provide security awareness training, regular refreshers, and specialized sessions for stakeholders with hands-on responsibilities.
- Policies and Procedures: Institutions must regularly test and monitor security measures for effectiveness, updating them to address emerging threats.
- Vendor Management: Institutions must assess and continuously monitor service providers to make sure they maintain the appropriate safeguards.
- Ongoing Improvements: Institutions must regularly update information security programs to accommodate changes with material impacts.
- Incident Response: Institutions must create a written incident response and recovery plan for security events.
- Reporting: Institutions must have the Qualified Individual report in writing regularly (at least annually) to the Board of Directors or another governing body.
Note: The FTC’s How to Comply with the Safeguards Rule guide has much more to say about these elements and their requirements.
Although it took effect in 2003, the Safeguards Rule was updated in 2021 to provide more detailed guidance for businesses navigating new technologies. Perhaps most importantly, this amendment introduced eight specific safeguards—or cybersecurity requirements—for GLBA compliance. At a high level, they include implementing access controls, an asset inventory, encryption, application security, MFA, secure data disposal, change management, and user activity monitoring.
Among other things, the revision also introduced mandatory risk assessments and reporting requirements for financial institutions with over 5,000 customer records and clarified requirements for vendor oversight, making financial institutions directly responsible for third-party compliance. It also made GLBA compliance enforceable for Title IV higher education institutions processing Federal Student Aid applicant information.
Most recently, the GLBA changed again in 2023 when the FTC introduced its breach notification requirement—which just took effect in May 2024. Now, if a financial institution suffers a security breach involving unauthorized access to the unencrypted information of at least 500 consumers, it must submit a completed Safeguards Rule Security Event Reporting Form to the FTC as soon as possible and no later than 30 days after the event.
What is the GLBA Pretexting Rule?
The Pretexting Rule protects sensitive financial information by prohibiting the use of deceptive practices to obtain or disclose customer financial information. Introduced in 1998 as part of the original GLBA, the Pretexting Rule was created to combat rising fraud and identity theft via pretexting, or the practice of obtaining personal information under false pretenses.
Today, pretexting is more commonly known as social engineering and includes wildly successful tactics like phishing. And while the specific methods attackers use may have changed since 1999, the Pretexting Rule is still highly relevant today.
Key prohibitions of the Pretexting Rule include:
- False Pretenses: Individuals must not obtain or disclose customer information under false pretenses.
- Solicitation: Individuals must not ask another person to obtain customer information if they know they will do so under false pretenses.
- Law Enforcement: Individuals must not misconstrue the pretexting provisions to prevent law enforcement agencies from obtaining customer information for official duties.
The Pretexting Rule also includes exceptions for obtaining customer information in certain cases, including for testing security systems, investigating allegations, recovering customer financial information, investigating insurance fraud, or collecting child support judgments.
Although it might seem a little out of left field, the Pretexting Rule does have some significant implications for financial institutions. For example, preventing individuals from obtaining your customers’ financial information will likely involve putting some identity and access management processes in place. You’ll also need to train your employees to recognize pretexting (aka phishing attempts) and educate your customers on the importance of good cyber hygiene.
How to Comply with the GLBA
Complying with the GLBA means protecting sensitive financial data and meeting certain requirements in the Privacy, Safeguards, and Pretexting Rules. Which requirements your financial institution must meet will depend on its nature, size, and complexity. As a result, the road to GLBA compliance will likely look different for everyone.
Which requirements your financial institution must meet will depend on its nature, size, and complexity. As a result, the road to GLBA compliance will likely look different for everyone.
Fortunately, the following step-by-step instructions are just general enough to be of use at the earliest stages of almost any financial institution’s GLBA journey.
Here’s a step-by-step overview of the GLBA compliance process:
- Understand the Rules: Start by familiarizing yourself with the Privacy, Safeguards, and Pretexting Rules and how they apply to your institution.
- Deliver Privacy Notices: Create clear, accessible privacy notices to inform customers or students about how you collect, use, and share their data. Provide opt-out options for data sharing with nonaffiliated third parties.
- Develop a Security Plan: Conduct information security risk assessments and draft a written information security plan that addresses the Safeguard Rule’s elements, including the eight requirements for cybersecurity safeguards.
- Vet and Manage Vendors: Conduct risk assessments for all third-party vendors that access sensitive financial data to evaluate their security practices. Implement vendor agreements that align with GLBA requirements and monitor vendor compliance regularly.
- Prevent Pretexting: Put identity verification processes in place to make sure sensitive information is only shared with authorized individuals. Train staff to recognize social engineering schemes and encourage customers to protect their own information by sharing tips on common scams.
For most institutions, the Safeguards Rule—which requires ongoing efforts to design, implement, and maintain cybersecurity measures—will likely require the biggest compliance lift. Fortunately, GLBA compliance software can make the entire process much more manageable.
The Role of GLBA Compliance Software
Let’s be real—GLBA compliance can be a headache, and spreadsheets aren’t doing you any favors. Scattered data, version control nightmares, and endless copy-pasting can make risk management way harder than it needs to be. But manual workflows aren’t just annoying; they’re leaving your organization exposed.
Fortunately, it’s 2025—and there’s a better way.
Now, with GLBA compliance software like Isora GRC, financial institutions can finally ditch the spreadsheets and step into the future. In Isora, teams can collect, organize, store, analyze, collaborate, and take action on all the data they need for information security risk and compliance management—all in one place. The result? Simpler, superior security GRC processes for more manageable GLBA compliance.
In Isora, teams can collect, organize, store, analyze, collaborate, and take action on all the data they need for information security risk and compliance management—all in one place.
Use Isora’s central inventory, for instance, to access, manage, and track assets, third-party vendors, products, and applications all in one place in real-time. With instant, accurate, and actionable insights into your entire information security ecosystem, identifying GLBA compliance gaps is easy. Just use the assessment management dashboard to distribute, organize, and monitor GLBA risk assessments, questionnaires and surveys across units, assets, and third parties—without chasing down emails or waiting for status updates.
Then, track, prioritize, and manage risks as a team in Isora’s collaborative risk register, where you can link risks to assessments for context, conduct detailed risk analyses, visualize high-risk areas, and share risk data with ease. Plus, Isora can even generate and export detailed risk reports and scorecards so you can measure progress, celebrate wins, and demonstrate value every step of the way.
Discover how Isora can help your organization implement the security posture needed to protect every flavor of consumer financial information, from student loan information to credit scores, account history, transactions, and more.
GLBA Frequently Asked Questions
More burning questions about GLBA compliance? Find the answers here in our GLBA FAQ.
What does GLBA stand for?
GLBA stands for the Gramm-Leach-Bliley Act, a U.S. federal law that requires financial institutions to protect customer financial data and disclose how they collect, store, and share it.
What is the purpose of the GLBA?
The purpose of the GLBA is to protect sensitive consumer financial information by making financial institutions legally responsible for securing it, being transparent about how they share it, and giving consumers more control over how they use it.
What are the main sections of the GLBA?
The GLBA consists of three main sections or rules: the Privacy Rule, the Security Rule, and the Pretexting Rule. Each rule outlines specific requirements for protecting consumer financial information.
- The Privacy Rule: Requires institutions to inform customers about how they collect, use, and share financial information and offer options to limit sharing.
- The Safeguards Rule: Requires institutions to create and follow a written plan to secure customer information against threats, breaches, and unauthorized access.
- The Pretexting Rule: Prohibits individuals from using false or dishonest methods to obtain or disclose customer financial information.
What are some GLBA examples?
Recent examples of GLBA non-compliance include:
- In 2025, the FTC issued a complaint against Greystar after the company advertised deceptive costs to obtain consumer financial information.
- In 2023, a federal court entered into a $20.3 million judgment against Jonathan Braun after he knowingly issued deceptive small-business loans.
- In 2021, the FTC ordered Ascension Data & Analytics to strengthen its security safeguards and conduct regular assessments in line with GLBA.
Who does the GLBA protect?
The GLBA protects consumers and customers who engage in financial transactions, including account holders, borrowers, or individuals who provide financial data to a covered institution. Whether the individual is an active customer or a one-time consumer of a financial product or service determines which GLBA requirements the financial institution must meet in protecting that information.
What does the GLBA protect?
The GLBA protects NPI (Nonpublic Personal Information), which includes personally identifiable financial data (like credit card numbers or loan history), transactional data (like purchase records or banking activity), and customer information provided for financial services (like mortgage applications or investment profiles).
How do you comply with the GLBA?
To comply with the GLBA, familiarize yourself with its components—the Financial Privacy Rule, the Safeguards Rule, and the Pretexting Provisions—and identify the components that impact your organization. From there, you can find compliance checklists, such as the GLBA Safeguards Rule Compliance Checklist, to evaluate how well your organization complies with the GLBA.
Who enforces GLBA compliance?
Enforcing GLBA compliance are regulatory agencies, including the CFPB, the FTC, the SEC, and the CFTC. Consequences for GLBA violations are not always straightforward, with fines and penalties often issued on a case-by-case basis. GLBA compliance does not supersede state statutes, and in some states, laws may be stricter than the GLBA.
Who should comply with the GLBA?
The GLBA applies to traditional and non-traditional financial institutions, certain third-party providers, and any other businesses significantly involved in financial activities and handling NPI.
How does the FAST Act affect GLBA?
The Fixing America’s Surface Transportation (FAST) Act of 2015 introduced an “Eliminate Privacy Notice Confusion” section, allowing financial institutions to skip annual privacy notices (required by the GLBA) in certain circumstances. More specifically, financial institutions do not need to distribute annual privacy notices if they share NPI under limited circumstances and if it has not changed their privacy policy or practices since their most recent privacy notices.
How is the FCRA related to GLBA?
The Fair Credit Reporting Act (FCRA) is a U.S. privacy law requiring consumer reporting agencies to give consumers an opt-out right for information shared with affiliated and nonaffiliated third parties. The GLBA, on the other hand, gives consumers an opt-out right for information shared with nonaffiliated third parties only.
If your financial institution is a consumer reporting agency, it must comply with privacy requirements for both GLBA and FCRA.



















 Other Relevant Content
Other Relevant Content