 Table of Contents
Table of Contents

Introduction
Self-Assessment Questionnaires (SAQs) are an important part of any organization’s Information Security Risk Management (ISRM) program and security risk assessment process. But what exactly are they and why are they a valuable tool?
SAQs might sound self-explanatory, but their meaning isn’t always obvious due to their widespread applications. This guide from SaltyCloud aims to make information security SAQs easy to understand. We’ll define them, explain why they’re a valuable tool for your security risk assessments, and how your organization and security team can get started using them.
What is a Self-Assessment Questionnaire (SAQ)?
A Self-Assessment Questionnaire (SAQ), also referred to as a control self-assessment (CSA), security questionnaire, or security assessment questionnaire, is a risk assessment tool that private and public organizations and their security teams use to internally or externally assess the adherence of a given target to information security standards, controls, best practices, security policies, and regulatory requirements.
SAQs feature a series of targeted questions or statements designed to reveal how well an organization, team, project, asset, or third-party vendor complies with industry-standard security practices.
SAQs feature a series of targeted questions or statements designed to reveal how well an organization, team, project, asset, or third-party vendor complies with industry-standard security practices. This introspective process helps organizations identify potential vulnerabilities and areas for improvement quickly and efficiently.
While SAQs gained significant popularity in information security due to their role in PCI DSS compliance, their value extends beyond this specific regulatory use, making it a versatile tool for internal or third-party security risk assessments.
Anatomy of an SAQ
To effectively use an SAQ for a security risk assessment, it’s essential to understand its components and how they work together to provide reliable insights. Let’s break down the key elements of an SAQ:
Control Questions
The core of any SAQ is a set of carefully designed questions. These questions are typically derived directly from security frameworks, regulatory requirements, or industry best practices. For example, NIST CSF control ID.AM-01 (“Inventories of hardware managed by the organization are maintained”) might translate into the SAQ question, “Does your organization maintain a regularly updated inventory of physical devices and systems?”
Each question is phrased to be unambiguous and focused, aiming to elicit a clear “yes” or “no” answer, or a scaled response from participants that accurately reflects the maturity of a specific control. It may even be relevant to include additional context for in the question text to improve its effectiveness.
Categories of questions
Just as security frameworks are structured into domains (e.g., Access Control, Asset Management, Network Security, Incident Response, Vulnerability Management, etc.), SAQ questions are carefully categorized. By organizing questions in this way, you can specifically evaluate categorical strengths and weaknesses, helping provide insights into where you need to focus your budgets to minimize the likelihood of a security incident or data breach caused through that given domain.
Question weights
Some questions are more critical than others and might be assigned weights to prioritize critical areas. For instance, a question about encryption practices might carry more weight than one about password complexity. This weighting helps surface the most critical areas for improvement first.
Question answer choices
Answers usually come in two primary formats:
- Binary (Yes/No): This straightforward option measures whether the security control, requirement, or best practices is present or absent.
- Scale: This option uses a graded scale (e.g., 1-5) like the Capability Maturity Model (CMM) to evaluate the maturity or sophistication of a control. For example, the ID.AM-01 question above, “Does your organization maintain a regularly updated inventory of physical devices and systems?” might use the following answer choices to measure its maturity:
- CMM 0 – Not Implemented: There is no regular inventory process, and asset tracking is lacking.
- CMM 1 – Ad Hoc: Inventory is informal, inconsistent, and likely incomplete.
- CMM 2 – Requirements Driven: Inventory exists, but it’s decentralized, lacks standardization, and focuses primarily on high-value assets.
- CMM 3 – Standardized: Inventory processes are consistent, automated where possible, and asset ownership is tracked. Reviews are conducted quarterly.
- CMM 4 – Metrics-Driven: The inventory process is tightly integrated with your security posture. Metrics drive optimization, regular reviews occur, and change control is implemented for improvements.
- CMM 5 – Predictive: Your inventory system utilizes advanced analytics (AI, machine learning) for proactive management and continuous improvement.
Question answer choice multipliers
Just as questions carry different weights based on their criticality, answer choices also have varying impacts. Multipliers reflect these differences. For example, in a CMM-based SAQ, answers demonstrating mature security controls would receive higher scores than those indicating less robust practices. This scoring system helps you not only identify areas of compliance but also reveals where your security posture is strongest.Scoring formula
SAQs use a formula to calculate a risk score. This formula combines question weights with answer multipliers to assign a numerical value to each question. By summing those scores across the entire SAQ, you arrive at an overall risk assessment score. This scoring system highlights your risk areas, allowing for targeted remediation strategies within your information security risk management program.
Why use SAQs in your security risk assessment process?
While they may appear as simple checklists, security questionnaires are powerful risk assessment tools. They excel at systematically identifying potential vulnerabilities, security risks, and control gaps, making them indispensable for both internal assessments and third-party vendor evaluations. Here’s why security questionnaires are ideal:
- Structured Approach: SAQs provide a methodical framework for examining security controls across various domains, ensuring a comprehensive assessment.
- Industry Alignment: Well-designed SAQs align with recognized standards (such as the Cloud Security Alliance), allowing you to benchmark your practices and identify areas for enhancement.
- Scalability: SAQs can be easily distributed to relevant stakeholders or multiple vendors. This streamlines data collection and provides a holistic view of your security posture across internal operations and third party vendors (e.g., vendor risk management).
- Data-Driven Insights: SAQs, especially those with scoring mechanisms, quantify your responses. This highlights risks, strengths, and prioritizes risk management efforts for maximum impact.
By integrating questionnaires into your information security risk management strategy, you gain a clear, standardized, and scalable method to assess and optimize your security posture. SAQs can help you avoid cyber threats, safeguard sensitive data, ensure business continuity, and achieve regulatory compliance.
Why use SAQs over traditional audits?
SAQs provide a complementary, and often preferable, approach to traditional audits for security risk assessments. Here’s why:
- Cost-efficiency: SAQs leverage existing resources, reducing costs associated with external auditors and in-depth technical evaluations.
- Timeliness: SAQs enable more frequent assessments, ensuring you stay ahead of emerging threats.
- Employee Engagement: SAQs foster a security-aware culture by involving a wider range of employees, offering diverse perspectives on risks.
- Customization: SAQs can be tailored for specific security concerns or compliance needs, unlike audits with a fixed scope.
- Rapid Response: SAQ findings allow for swift remediation, improving your security posture with agility.
- Strategic Alignment: SAQs can support your organization’s specific security goals, compliance requirements, and risk appetite.
- Confidentiality: Internal SAQs offer greater control over sensitive security information and associated vulnerabilities.
- Empowerment: SAQs promote employee ownership of security risk management, leading to proactive improvement and a stronger overall security posture.
The role of self-assessment questionnaire software
While spreadsheets in Excel or basic survey tools (like SurveyMonkey) might get the job done initially, their limitations will become apparent as your ISRM program grows and matures. Advanced information security SAQ software provides a much-needed upgrade, offering purpose-built workflows to manage your security risk assessments.
While spreadsheets in Excel or basic survey tools (like SurveyMonkey) might get the job done initially, their limitations will become apparent as your ISRM program grows and matures.
Self-Assessment Questionnaire software like Isora, a collaborative GRC assessment platform, provides the tooling needed to streamline SAQ design, distribution, analysis, and reporting across different use cases including ISRM, Third-Party Security Risk Management (TPSRM), and Application Security Risk Management (ASRM).
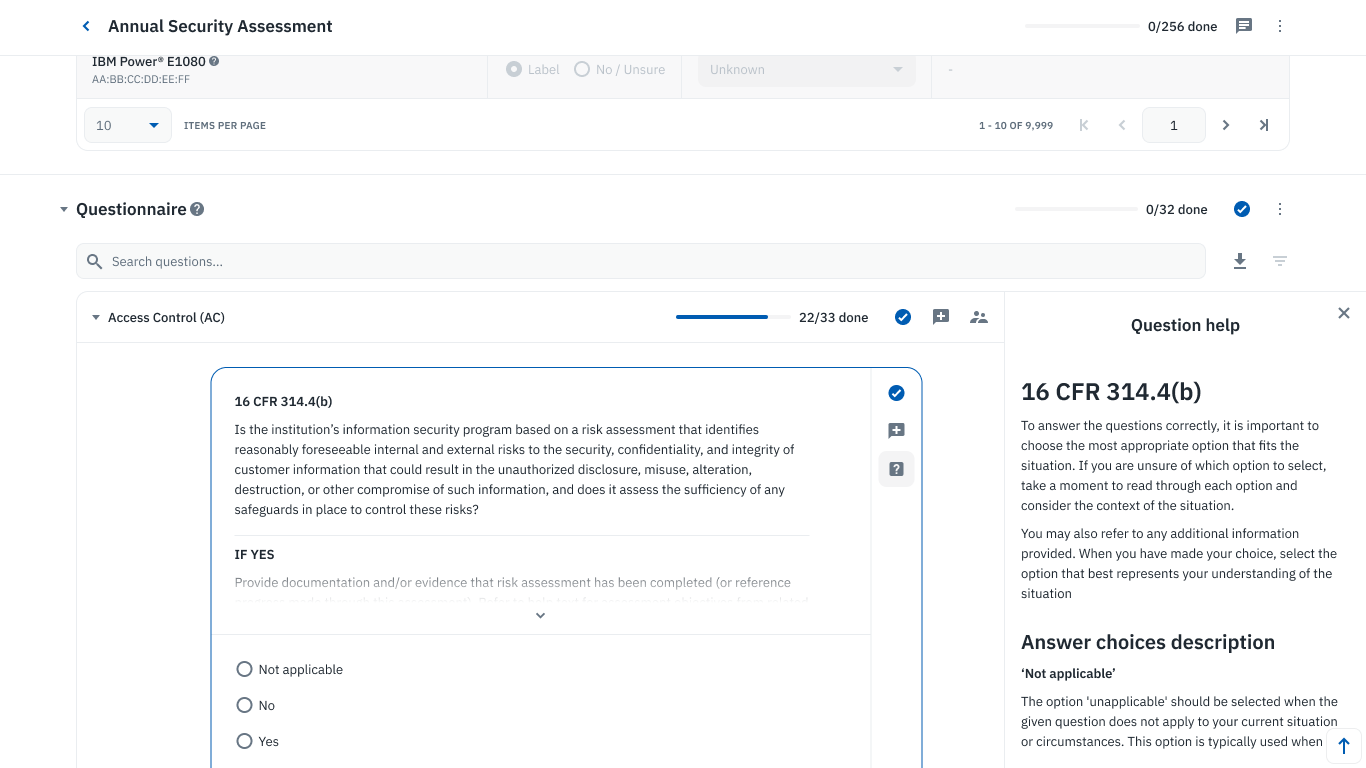
Collaborative questionnaire on Isora GRC.
Isora can help you meet regulatory compliance, improve your overall security posture, and facilitate collaboration with internal teams and external vendors to address security risks proactively.
Conclusion
SAQs are far more than compliance checklists. They are robust, scalable, cost-effective tools for proactively managing information security risk. By systematically assessing the existence or maturity of controls or standards, SAQs help you identify vulnerabilities, prioritize remediation, and make risk-driven decisions that keep your organization safe. Well-designed SAQs also ensure you meet industry and regulatory compliance standards.
Adopting SAQs within your security program is a critical step towards safeguarding sensitive customer data against cybersecurity risks, enhancing data security, and ensuring the continuity of business operations. By effectively understanding and utilizing SAQs, you position your organization to manage risk and thrive in today’s digital ecosystem, safeguarding your critical assets and sensitive customer data against potential security incidents.
Ultimately, the importance of SAQs in ISRM cannot be overstated. They are essential for a more in-depth assessment of security measures, offering a systematic approach to your security risk assessment.risk assessment.




















 Other Relevant Content
Other Relevant Content