 Table of Contents
Table of Contents
NIST 800-53 Rev 5: What Changed From Rev 4 and How to Transition
NIST SP 800-53 Rev 5, published in September 2020, is the most significant update to the federal security and privacy control catalog in over a decade. Key changes from Rev 4 include introducing two new control families—PT (Personally Identifiable Information Processing and Transparency) and SR (Supply Chain Risk Management)—integrating privacy controls throughout the catalog, moving baselines to a separate document (NIST SP 800-53B), and broadening the scope beyond federal IT.
This article explains what changed in Rev 5, how it differs from NIST 800-53 Rev 4, the complete NIST 800-53 revision timeline from its initial 2005 release through Rev 5, and the latest incremental updates (Releases 5.1.1 and 5.2.0). It also includes a step-by-step guide to help federal agencies, contractors, and cloud service providers migrate from Rev 4 to Rev 5.
What’s in NIST 800-53 Rev 5
NIST Special Publication 800-53 Revision 5 was published by the National Institute of Standards and Technology(NIST) on September 23, 2020, making it the official current version of the catalog. Titled “Security and Privacy Controls for Information Systems and Organizations,” the initial public draft had been circulating since December 2017, giving agencies and organizations nearly three years to prepare for the final release.
NIST 800-53 Rev 5 is the current version of the federal security and privacy controls catalog, published September 23, 2020. It contains 1,189 controls across 20 families including two new families added in Rev 5 (PT and SR). It replaced Rev 4 and integrates privacy controls directly into the catalog for the first time.
Rev 5 is organized around four key themes:
- Privacy integration. Privacy controls are woven directly into the control catalog alongside security controls, rather than being sequestered in a separate appendix.
- Supply chain risk management. A dedicated control family (SR) addresses supply chain threats that were only partially covered in earlier revisions.
- Outcome-based control language. Controls describe desired outcomes rather than prescribing specific technologies or system configurations.
- Technology neutrality. By removing system-specific language, Rev 5 controls apply equally to cloud environments, on-premises systems, IoT devices, and operational technology.
Most recently, NIST released NIST SP 800-53 Rev 5.2.0 on August 27, 2025, in response to Executive Order 14306 on strengthening the nation’s cybersecurity. According to the Summary of Changes, the revision addresses multiple aspects of the software development and deployment process.
In total, NIST 800-53 Rev 5 now contains 1,189 controls spread across 20 control families. Control baselines—the Low, Moderate, and High starting points for control selection—have been relocated from the main publication to a companion document, NIST SP 800-53B.
For organizations that must comply with Federal Information Security Modernization Act (FISMA), pursue authorization under the Federal Risk and Authorization Management Program (FedRAMP), or voluntarily align with the NIST Cybersecurity Framework (CSF), aligning with the current version of NIST 800-53 Rev 5 is considered best practice in 2026. The official publication is available for free download from the NIST Computer Security Resource Center (CSRC).
Key Changes from Rev 4 to Rev 5
The transition from NIST 800-53 Rev 4 to Rev 5 introduces several changes that affect how organizations select, implement, and assess security and privacy controls. For organizations updating an SSP, mapping controls across frameworks, or preparing for an audit or authorization, these differences tend to show up quickly.
Two New Control Families
Rev 5 added two entirely new control families to the catalog:
- PT (Personally Identifiable Information Processing and Transparency) – 17 controls addressing how organizations collect, use, store, and share personally identifiable information (PII). These controls enforce transparency requirements and offer a structured approach to managing privacy obligations.
- SR (Supply Chain Risk Management) – 13 controls dedicated to identifying, assessing, and mitigating risks in the supply chain. Prior to Rev 5, supply chain concerns were addressed through scattered controls in the SA (System and Services Acquisition) family.
Notably, these additions brought the total from 18 to 20 NIST 800-53 control families.
Control Numbering
While NIST 800-53 Rev 4 includes approximately 965 controls across 18 families, Rev 5 has 1,189 across 20 families, a substantial increase. Despite the sweeping changes, however, NIST also elected to preserve the existing control numbering scheme for continuity. Organizations migrating from Rev 4 will find most control identifiers familiar, with new controls added rather than existing ones renumbered.
Privacy Controls Integrated Throughout
In Rev 4, privacy controls lived in Appendix J—a separate section which implicitly framed it as optional or secondary. Instead, Rev 5 eliminates Appendix J entirely and distributes privacy controls throughout the main catalog alongside their security counterparts. Privacy is now embedded into every control family where it is relevant.
For organizations transitioning to the integrated control catalog in Rev 5, NIST offers a mapping of Appendix J Privacy Controls (Rev. 4) to Rev. 5.
Control Baselines Separated
Rev 5 moves the Low, Moderate, and High control baselines out of the main publication and into NIST SP 800-53B. From here, organizations select their baselines based on their system categorization under Federal Information Processing Standards Publication (FIPS 199).
This separation makes the core 800-53 catalog a pure control reference that is agnostic to any specific framework, baseline, or implementation context. It also enables NIST to update each publication separately, simplifying maintenance and version control.
Broader Scope
The removal of “Federal” from the title of NIST 800-53 is perhaps one of the most significant changes in Rev 5. The publication is now referred to as “Security and Privacy Controls for Information Systems and Organizations” rather than “for Federal Information Systems and Organizations.” Today, Rev 5 explicitly acknowledges that its controls apply to organizations, systems, and individual components, not just federal government IT systems.
Outcome-Based Control Language
Where Rev 4 uses prescriptive, system-centric language such as “the information system shall…,” Rev 5 shifts to outcome-based phrasing like “ensure that…” This change makes controls applicable to any technology stack, whether cloud-native, on-premises, hybrid, or emerging technologies like IoT. It also aligns NIST 800-53 more closely with international standards and frameworks like NIST CSF.
Rev 4 vs Rev 5 Comparison Table
| Dimension | Rev 4 (2013) | Rev 5 (2020) |
|---|---|---|
| Control families | 18 | 20 (added PT, SR) |
| Total controls | ~965 | 1,189 |
| Privacy controls | Appendix J (separate) | Integrated throughout catalog |
| Baselines location | Main publication | Separate document (SP 800-53B) |
| Control language | System-specific (“the information system shall…”) | Outcome-based (“ensure that…”) |
| Supply chain controls | Limited (SA family) | Dedicated SR family (13 controls) |
| Scope | Federal information systems | All organizations and systems |
| Title | “…for Federal Information Systems and Organizations” | “…for Information Systems and Organizations” |
Understanding these changes is easier with historical context. Here’s how the 800-53 catalog has evolved over nearly two decades.
Timeline of All NIST 800-53 Revisions
NIST has updated the 800-53 catalog five times since its original publication in 2005, with each revision expanding scope and adapting to new threat landscapes. Here’s a brief history of every revision:
- Rev 1 (2005): The original publication established the first formal catalog of security controls for federal information systems under FISMA. It organized approximately 300 controls across 17 families and gave agencies a common vocabulary for security requirements.
- Rev 2 (2007): A minor update that refined control descriptions, added supplemental guidance, and corrected errata. The overall structure and family count remained unchanged.
- Rev 3 (2009): A major structural overhaul. Rev 3 introduced the control family organization that persists today, added application-level controls, and aligned more closely with Committee on National Security Systems (CNSS) standards. The control count grew to approximately 650 across 18 families.
- Rev 4 (2013): A significant expansion that added privacy controls in Appendix J, introduced control overlays for tailoring to specific communities, and broadened assurance and trustworthiness concepts. Rev 4 served as the standard for seven years, with 18 families and approximately 965 controls.
- Rev 5 (2020): The current and required version. Added two new families (PT and SR), integrated privacy controls throughout the catalog, moved baselines to SP 800-53B, and shifted to outcome-based language. It contains 20 families and 1,189 controls.
| Version | Year | Key Change | Families | Controls (approx.) |
|---|---|---|---|---|
| Rev 1 | 2005 | Original publication under FISMA | 17 | ~300 |
| Rev 2 | 2007 | Refinements and guidance updates | 17 | ~350 |
| Rev 3 | 2009 | Current family structure established | 18 | ~650 |
| Rev 4 | 2013 | Privacy appendix, overlays, expanded scope | 18 | ~965 |
| Rev 5 | 2020 | Privacy integration, 2 new families, outcome-based | 20 | ~1,189 |
While Rev 5 was the last major revision, NIST has continued to refine the catalog through incremental releases.
Rev 5.1.1 and 5.2.0 Updates
Since the initial Rev 5 publication in September 2020, NIST has released incremental updates that evolve the catalog without changing its fundamental structure. Most notably are Release 5.1.1 and Release 5.2.0.
Release 5.1.1 (November 2023) was a maintenance release. It corrected errata in control descriptions, clarified supplemental guidance language, and updated references to companion publications.
The update also introduced one new control (IA-13) and three supporting control enhancements related to identity providers, authorization servers, the protection of cryptographic keys, the verification of identity assertions and access tokens, and access management.
For organizations implementing identity and access management (IAM) architectures, IA-13 requires the use of identity providers and authorization servers to manage user, device, and non-person entity (NPE) identities, attributes, and access rights that support authentication and authorization decisions.
This new control was not included in any predefined baselines and remains optional for implementation. Organizations already compliant with Rev 5 were therefore not required to make implementation changes, though reviewing the updated control descriptions for clarity improvements is still recommended.
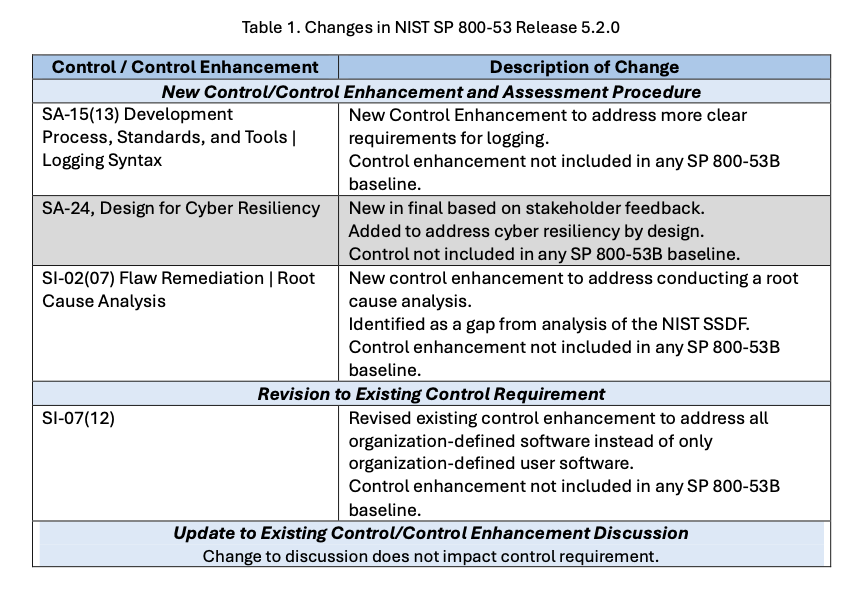
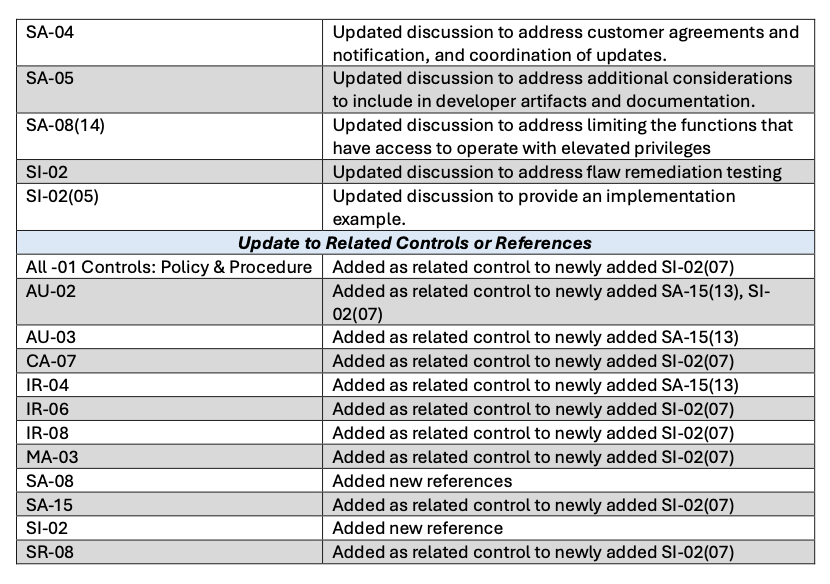
Release 5.2.0 (August 2025) was a minor release issued in response to EO 14306, with a focus on strengthening software development practices and cybersecurity.
The changes in Rev 5.2.0 address multiple aspects of the software development and deployment process, including software and system resiliency by design, developer testing, the deployment and management of updates, and software integrity and validation. As part of this update, three new controls were introduced:
- Logging Syntax (SA-15) defines a standardized electronic format for recording security-related events to support incident response. Standardized data formats enable automation and help teams reconstruct incidents more quickly.
- Root Cause Analysis (SI-02(07)) requires organizations to review the cause of a software update issue or failure, develop an action plan, and implement corrective measures.
- Design for Cyber Resiliency (SA-24) focuses on system survivability, or the ability to anticipate, withstand, respond to, and recover from attacks while maintaining critical functions.
For organizations already operating under Rev 5, the practical impact of these incremental updates is typically editorial or clarifying rather than structural. However, it is good practice to review each release for changes to control descriptions that may affect your implementation documentation.
How to Transition from Rev 4 to Rev 5
Transitioning from NIST 800-53 Rev 4 to Rev 5 requires a structured approach that starts with mapping existing controls to the updated catalog, addressing the two new families, and updating documentation. The following eight steps offer organizations a clear path forward.
Step 1: Inventory your current Rev 4 controls.
Document every control currently implemented, including enhancements and any tailoring decisions your organization has made. Then, map them against your system security plan (SSP). This inventory becomes your baseline for comparison.
Step 2: Obtain the Rev 5 catalog and SP 800-53B
Download the current Rev 5 publication and the corresponding baselines document (NIST SP 800-53B). Remember that these are now separate documents and you will need both. Importantly, there are no changes in SP 800-53B Release 5.2.0.
For an official analysis of updates between 800-53 Rev 5 and Rev 4, The MITRE Corporation has authored and shared a comparison.
Step 3: Map Rev 4 controls to Rev 5 equivalents
Use the NIST-provided mapping table to identify how your existing Rev 4 controls translate to Rev 5. Most control numbers are preserved, which simplifies this step considerably.
Mappings and crosswalks between 800-53 Rev 5 and other frameworks and standards (including NIST CSF and ISO/IEC 27001:2022) are also available to help. Other resources include a Security and Privacy Control Collaboration Index Template and a OSCAL version of 800-53 Rev. 5 controls using the Open Security Controls Assessment Language.
Step 4: Assess the two new control families
Review the PT (PII Processing and Transparency) and SR (Supply Chain Risk Management) families. Determine which controls apply to your system based on your baseline selection in SP 800-53B. Even if your organization did not previously address these areas formally, Rev 5 may now require it. Treat this as a scoping step first, then an implementation step.
Step 5: Update control baselines
Since baselines moved to SP 800-53B, review the Low, Moderate, and High baseline assignments for changes. Some controls were reassigned across baselines between Rev 4 and Rev 5.
Step 6: Revise system security plans and documentation
Update your SSP, policies, and procedures to reference Rev 5 control language. Replace prescriptive language with outcome-based descriptions matching Rev 5’s approach.
Step 7: Conduct a gap assessment
Compare your updated control set against Rev 5 requirements to identify implementation gaps. And make sure to prioritize gaps in the new PT and SR families, which represent entirely new compliance obligations for most organizations. For a detailed assessment methodology, see our NIST 800-53 risk assessment guide.
Step 8: Update your authorization package
If operating under an Authority to Operate (ATO), update your authorization documentation to reflect Rev 5 and submit for re-evaluation as required by your authorizing official.
NIST 800-53 Rev 5 FAQs
When was NIST 800-53 Rev 5 released?
NIST 800-53 Rev 5 was published on September 23, 2020. The initial public draft was released in December 2017. Rev 5 replaced Rev 4 (published in 2013) as the current version of the security and privacy controls catalog. The most recent update is NIST SP 800-53 Rev 5.2.0, published on August 27, 2025.
What is the difference between NIST 800-53 Rev 4 and Rev 5?
Rev 5 added two new control families (PT for privacy and SR for supply chain), integrated privacy controls throughout the catalog instead of a separate appendix, moved baselines to SP 800-53B, and shifted from prescriptive to outcome-based control language. The total control count increased from approximately 965 to 1,189.
Is NIST 800-53 Rev 4 still valid?
No. NIST 800-53 Rev 4 was officially withdrawn on September 23, 2021 and is superseded by Rev 5. All organizations subject to FISMA, FedRAMP, or DoD requirements must use Rev 5. Programs still referencing Rev 4 should plan a controlled transition, especially if they operate in audit, authorization, or contractual environments that expect Rev 5 alignment.
How many controls are in NIST 800-53 Rev 5?
NIST 800-53 Rev 5 contains 1,189 security and privacy controls organized across 20 control families. This includes base controls and control enhancements.
Where can I download the NIST 800-53 Rev 5 PDF?
The official NIST 800-53 Rev 5 publication is available for free download from the NIST Computer Security Resource Center (CSRC). You can also explore the controls interactively through the NIST CPRT catalog.
What are the two new control families in Rev 5?
Rev 5 added PT (Personally Identifiable Information Processing and Transparency) with 17 controls and SR (Supply Chain Risk Management) with 13 controls. These families address privacy and supply chain risks that were only partially covered in Rev 4.
Conclusion
NIST 800-53 Rev 5 is the current and mandatory version of the security and privacy controls catalog. Key changes from Rev 4 include two new control families (PT and SR), privacy controls integrated throughout the catalog, baselines separated into SP 800-53B, and outcome-based control language, representing a significant evolution in how organizations approach security and privacy compliance.
For a comprehensive introduction to the entire NIST 800-53 framework, explore our complete guide to NIST 800-53.
Learn more about NIST 800-53 compliance software.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.
Dive into our research-backed resources–from product one pagers and whitepapers, to webinars and more–and unlock the transformative potential of powerfully simple GRC.
Learn More


















 Other Relevant Content
Other Relevant Content