 Table of Contents
Table of Contents
- What is a third-party security risk assessment?
- Why are third-party security risk assessments necessary?
- The role of third-party security risk management software
- Planning the assessment
- Conduct the assessment
- Beyond the assessment
- Isora GRC for Third-Party Security Risk Assessments
-
Third-Party Security Risk Assessments FAQs
- What is the purpose of a third-party security questionnaire?
- How does a third-party risk assessment differ from a traditional audit?
- What types of information should be included in a vendor risk assessment?
- When should we reassess our third-party vendors?
- Can we standardize our security questionnaires across vendors?
- How do vendor security questionnaires support a broader security program?
Third-party risk is no longer theoretical. It is the front door for modern cyberattacks. According to a 2025 global breach analysis, 35.5% of all data breaches last year originated from third-party compromises, a 6.5% increase over the previous year. In critical sectors like retail, technology, and infrastructure, most breaches now trace back to vendors, service providers, or contractors.
Ransomware is following the same pattern. Over 41% of ransomware attacks began through third-party access points. Just two exploited vulnerabilities in file transfer software accounted for 63.5% of all vulnerability-based breaches. A single vendor’s weakness can compromise an entire ecosystem.
A single vendor’s weakness can compromise an entire ecosystem.
Despite these risks, 54% of organizations still do not properly vet their third-party vendors. Without a formal third-party security risk assessment process, the odds are stacked against your security team.
This guide provides a step-by-step walkthrough for conducting effective third-party security risk assessments. You will learn how to plan, collect evidence, identify risks, and manage exceptions with clarity and consistency. Along the way, we will show how Isora GRC supports every phase of the process with structured workflows, centralized tracking, and purpose-built tools.
Let’s dive in!
One note up front: We use the terms “third party risk management,” “third party vendor risk management,” and “vendor risk management” interchangeably. If we’re feeling froggy, we might use “third party security risk management” to emphasize the security component to third party risk management.
The same goes for “third party risk assessment,” “third party vendor risk assessment,” “third party security risk assessment,” and “vendor risk assessment.” They’re all the same thing. Clear as mud? Perfect!
What is a third-party security risk assessment?
A third-party security risk assessment, also known as a vendor risk assessment or third-party risk assessment, is a structured evaluation of an external party’s ability to meet your organization’s information security standards. These assessments apply to any third party that interacts with your systems, processes, or data, including vendors, partners, contractors, consultants, and subsidiaries.
These assessments are one component of a broader Third-Party Security Risk Management (TPSRM) or Vendor Risk Management (VRM) program. The goal of that program is to continuously identify, evaluate, and manage the risks introduced by external entities across your organization’s supply chain.
In addition to identifying gaps, these assessments support transparency. Findings are shared with both internal stakeholders and vendor contacts to enable clear, informed decisions. Risk owners are then responsible for deciding whether to accept the risk, request remediation, or disqualify the vendor.
Why are third-party security risk assessments necessary?
Cyber threats continue to grow in volume and complexity. The question is not if a breach will happen, but when. Even with strong internal security practices, your organization remains exposed through external vendors.
In 2024, more than one in three breaches originated from third-party relationships, up significantly from the previous year. This trend confirms that third-party risk is not secondary. It is a primary concern for security teams.
In 2024, more than one in three breaches originated from third-party relationships, up significantly from the previous year.
Here are some of the key reasons these assessments are indispensable:
Supply chain attacks and security incidents
Attackers increasingly target vendors as a way into larger organizations. A single vulnerability in a third-party service can lead to widespread access across connected systems. This is not a theoretical risk.
In 2024, over 40 percent of ransomware attacks began through third-party access points. Vendors are now frequent entry points for scalable, high-impact breaches. A third-party security risk assessment gives your team a way to evaluate external threats before trust is established. By identifying gaps in a vendor’s controls, you can address vulnerabilities before they affect your environment.
Growing regulatory requirements
Regulatory compliance is another major factor driving the need for third-party security assessments. Laws and standards like GDPR, HIPAA, GLBA, CMMC, PCI-DSS, and others include specific clauses holding organizations accountable for protecting regulated data with third-party vendors.
Non-compliance can result in hefty fines, legal repercussions, and reputational damage. Conducting regular third-party security risk assessments helps not only maintain compliance but also demonstrate due diligence to auditors and stakeholders.
Business continuity and resilience
A vendor-related security incident can have a domino effect, disrupting your operations and affecting business continuity. In 2024, according to IBM’s Cost of a Data Breach Report, it took an average of 204 days to identify a breach and an additional 73 days to contain it, totaling 277 days on average.
Assessments help evaluate your vendors’ resilience against cyberattacks before they occur. This information is vital for your own business continuity planning and can be particularly useful in industries where uptime and data integrity are critical.
Vendor accountability and performance metrics
Third-party security risk assessments offer an empirical basis to hold your vendors accountable. By evaluating a vendor against predefined metrics and security controls, you can ensure they meet industry standards. This is especially crucial during onboarding new vendors and periodic review of existing partnerships.
Risk management and strategic decision-making
Understanding the security posture of third-party vendors helps assess the level of risk they pose to your organization. This enables more informed decision-making, whether you are contemplating entering into a new business relationship or considering the renewal of an existing one. Your findings may lead to constructive dialogues with vendors about possible remediation measures or cybersecurity improvements.
The role of third-party security risk management software
Third-party security risk management software, also known as vendor risk management software, supports the process of evaluating, tracking, and mitigating security risks across your external ecosystem.
These tools help security teams run structured assessments, monitor vendor compliance, and respond to emerging threats from suppliers, service providers, contractors, and other third parties.
As these ecosystems expand, managing risk manually becomes unsustainable. Many organizations still rely on spreadsheets, survey tools, or legacy GRC platforms that are disconnected from the needs of modern security teams. These approaches often lead to inconsistent data, poor visibility, and delays in critical decision-making.
Purpose-built vendor risk management tools address these challenges by enabling teams to:
- Maintain a consistent inventory of third-party vendors and their risk profiles
- Launch and manage questionnaire-based assessments
- Collect, store, and review security documentation and evidence
- Assign risk ownership and track remediation decisions
- Generate reports that support internal reviews and audits
While terminology may vary between platforms and organizations, the goal is the same: to operationalize third-party risk assessments as a repeatable, policy-driven part of your information security strategy.
In the next section, this guide walks through how the process works in practice, using Isora GRC to demonstrate each step.
Planning the assessment
Third-party risk assessments are not one-time activities. They require a consistent, structured approach that can be applied across departments, data types, and vendor categories. Without clear planning, teams often fall back on manual processes that lead to inconsistent results, delays, and visibility gaps.
Effective assessments begin with policy-driven preparation. Establishing formal guidelines ensures that each assessment is scoped, executed, and reviewed in a consistent way. This helps standardize how vendors are evaluated, what evidence is required, and how risk decisions are made.
As you prepare for an assessment, consider these key policy elements:
Roles and responsibilities
Effective third-party security risk assessments require clear accountability across internal and external stakeholders. Defining roles early ensures everyone understands their responsibilities, contributes the right inputs, and supports strategic alignment with broader organizational goals.
Use the table below to identify and assign key roles in your third-party risk assessment process:
| Role | Responsibility | Notes |
| Information Security Professional | Leads the assessment process, analyzes responses, and synthesizes findings | May be a single individual or a small team, depending on scope |
| Third-Party Contact | Represents the vendor during the assessment, completes questionnaires, and provides evidence | Could be technical (e.g. IT lead) or administrative (e.g. account manager) |
| Internal Risk Owner | Owns the business risk associated with the third-party relationship | Typically the department or individual requesting the vendor |
| Support Teams | Provides input on procurement, legal, compliance, risk, or privacy | May include compliance officers, procurement leads, or privacy counsel |
| Data Stewards | Ensures proper handling of regulated or sensitive data | Examples include HIPAA officers or data protection officers |
| Leadership | Offers strategic oversight, approves risk decisions, and allocates resources | Often includes CISOs, CIOs, or department heads |
Data classification levels
Every third-party security risk assessment should begin with a clear understanding of what types of data the vendor will access, process, or store. Applying your organization’s data classification framework ensures consistent and appropriate security controls across all third-party relationships.
A strong classification system organizes data into tiers based on sensitivity. These tiers guide the security requirements that vendors must meet and help identify where additional review or evidence is needed.
For example, a vendor handling public marketing content may require minimal controls, while one accessing protected health information (PHI) must meet strict encryption, access, and compliance standards.
Review your classification structure regularly to align with evolving regulatory requirements and organizational risk tolerance. A well-maintained classification framework supports informed, risk-based decisions and helps security teams tailor assessments efficiently.
Below is a table that maps common data classification levels to typical security requirements and regulatory considerations:
| Data Classification | Description | Typical Security Requirements | Relevant Regulations |
| Public | Intended for public release or unrestricted use | Minimal controls; no special handling required | None |
| Internal Use Only | Internal business use; not for public sharing | Basic access controls; staff-only access | May be covered by internal policies |
| Confidential | Sensitive business data or non-public IP | Encryption in transit, access logs, least privilege enforcement | GLBA, FERPA (depending on context) |
| Highly Confidential | Regulated or high-risk personal or system data | Strong encryption, MFA, strict access controls, audit trails | HIPAA, GDPR, PCI-DSS, SOX, CCPA |
This structure helps teams align security requirements with the type of data involved in the vendor relationship. It also supports clearer documentation, risk prioritization, and audit readiness throughout the third-party security risk management process.
Evidentiary requirements
The evidence you request during a third-party security risk assessment should reflect the sensitivity of the data involved, the nature of the service provided, and the risk profile of the relationship. Evidence collection should not follow a checklist mindset. It should be tailored, layered, and aligned to your organization’s expectations.
Security and risk teams should pull from multiple evidence types to form a complete picture of a vendor’s security posture. A multi-source approach improves assessment quality, reduces reliance on self-reported claims, and builds trust in the process.
Below is a table outlining key types of evidence, their purpose, and specific examples:
| Evidence Type | Purpose | Examples |
| Security questionnaires | Gather self-reported details on security practices, policies, and controls | Standardized Information Gathering (SIG), CAIQ by the Cloud Security Alliance, HECVAT used in higher education assessments |
| Certifications | Validate that the vendor complies with recognized security standards | SOC 2 Type II report, ISO/IEC 27001 certificate, FedRAMP authorization |
| Risk intelligence reports | Provide external assessments of the vendor’s threat exposure and vulnerabilities | BitSight security rating report, SecurityScorecard risk profile, custom threat intelligence briefings |
| Business continuity documentation | Evaluate how the vendor prepares for and responds to operational disruptions | Business Continuity Plan (BCP), Disaster Recovery Plan (DRP), test results from tabletop exercises |
| Penetration test results | Identify known and exploitable weaknesses in the vendor’s systems | Summary report from annual third-party penetration test, remediation tracking log |
| Contractual agreements | Confirm legal and regulatory obligations related to data handling and protection | Data Processing Agreement (DPA), GDPR Standard Contractual Clauses, HIPAA Business Associate Agreement (BAA) |
Whenever possible, request multiple forms of evidence to corroborate the third party’s claims. For example, a completed SIG questionnaire may provide context, while a SOC 2 report confirms control implementation and auditing.
To standardize expectations across assessments, create a scoring rubric that ties each data classification level to required evidence types and regulatory obligations. This ensures consistency, supports risk-based decision-making, and makes the review process easier to manage over time.
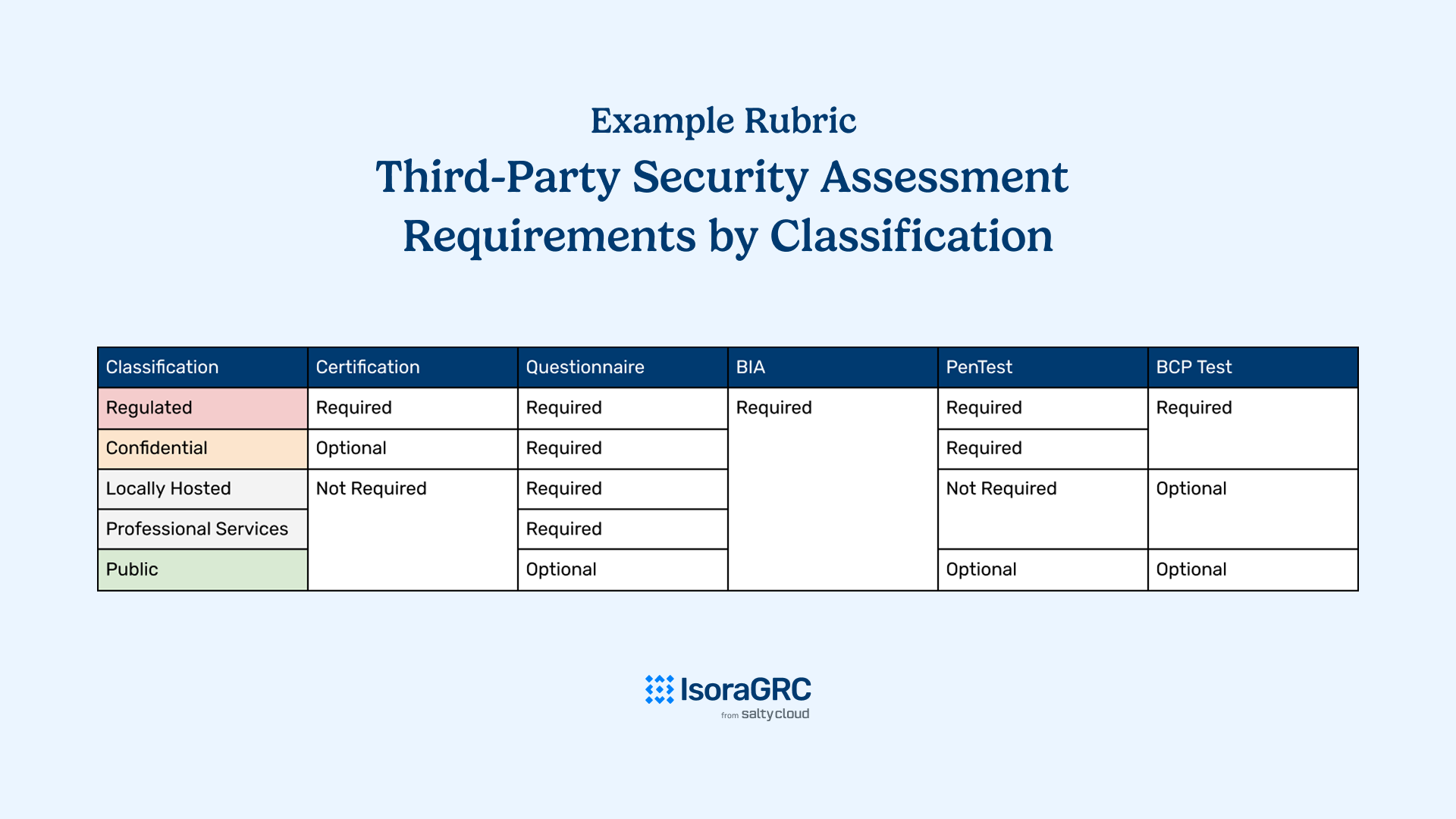
A simple visual example of a third-party security risk assessment requirement rubric where a series of data classifications are tied to a series of evidentiary requirements.
Conduct the assessment
Engaging in a third-party security risk assessment involves a series of interconnected steps that are integral to the risk management cycle. This process ensures that every phase—risk identification, risk analysis, and risk evaluation—is carried out cohesively and contributes to a comprehensive understanding of potential security risks.
By conducting an assessment, it means you are actively managing and executing a strategic sequence of events that begins with identifying risks and culminates in their thorough evaluation. Historically managed with spreadsheets, email threads, and shared drives, this process has evolved with a platform like Isora, which intuitively organizes and centralizes the process.
Step 1: Launch the assessment
Every assessment begins with setting clear objectives, identifying the vendor and scope, defining evidence requirements, and establishing due dates for completion. Traditionally, this step is handled manually, often using spreadsheets, email threads, and ad hoc instructions.
With Isora GRC, this step is initiated through a structured wizard that simplifies setup and enforces consistency across assessments.
| Task | Manual Process | With Isora GRC |
| Define vendor and product details | Tracked in separate documents or spreadsheets | Entered directly into the vendor assessment wizard |
| Assign business unit and risk owner | Communicated via email or offline coordination | Assigned in-platform with linked ownership metadata |
| Select or create questionnaire | Assembled manually from templates or prior emails | Chosen from preloaded framework-based templates or built using custom editor |
| Write instructions for vendor participants | Written manually into emails with no formatting consistency | Added in markdown with support for headers, links, and images |
| Establish due dates and reminders | Managed through calendar invites or email follow-ups | Set due dates trigger automated email reminders to participants |
| Group assessments by risk or data type | Requires separate tagging or spreadsheet sorting | Organize assessments into series by data classification or compliance goal |
| Track assessment status | Requires ongoing manual updates and coordination across teams | Monitored in real time from a centralized dashboard |
Explore how Isora’s Assessment Management capability supports each of these steps.
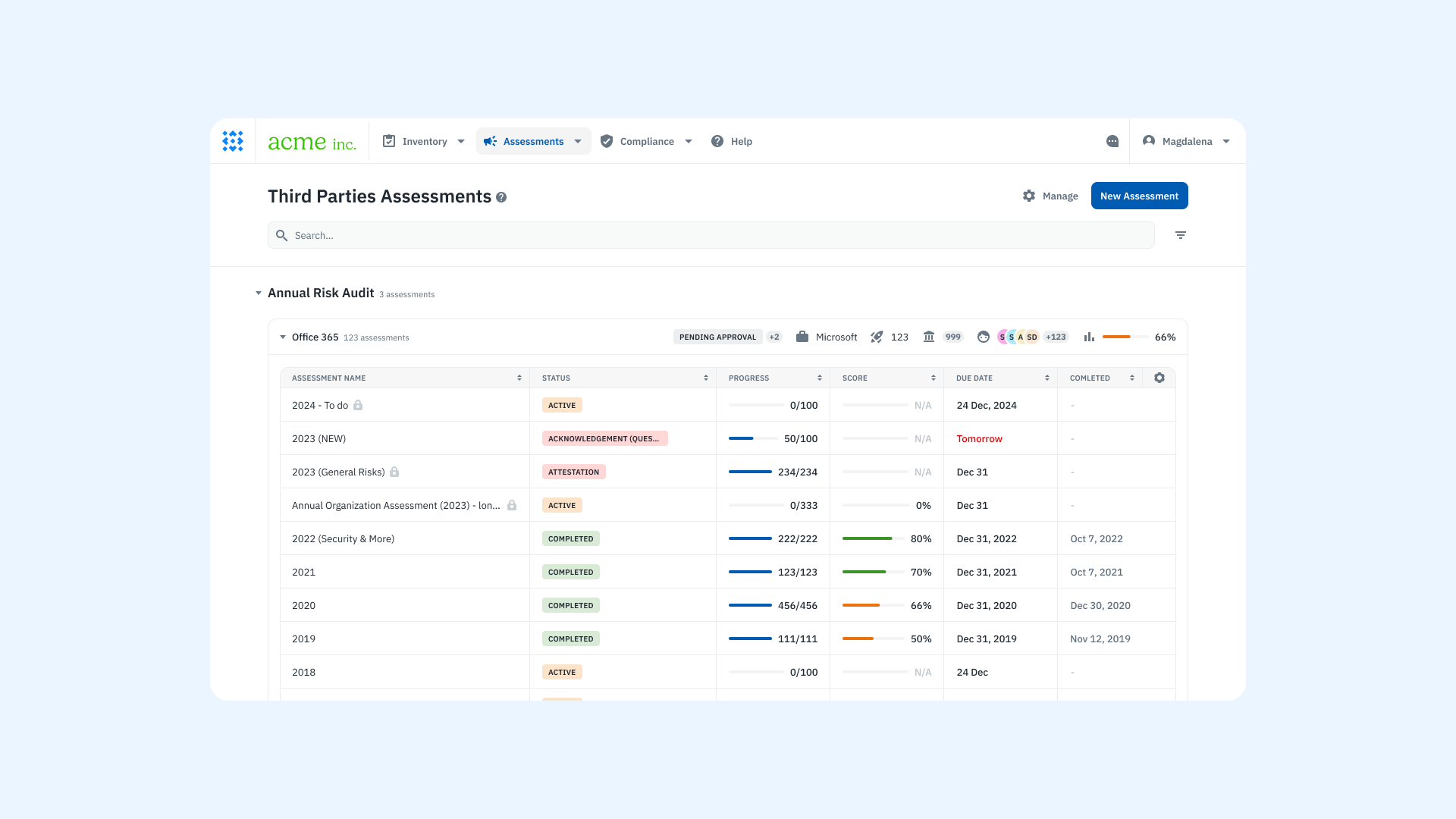
A product screenshot of the vendor assessment dashboard on Isora GRC.
Step 2: Collect details and evidence
The second phase of a third-party security risk assessment involves gathering detailed responses and supporting documentation from the vendor. This step provides the information your team needs to evaluate the vendor’s security controls against your internal standards and compliance obligations.
Most organizations use a structured questionnaire informed by frameworks such as SIG, CAIQ, or HECVAT. These frameworks offer a consistent baseline but often need to be customized with questions that reflect specific risks, data types, or contractual requirements.
When handled manually, this process is difficult to manage. Questionnaires are distributed as static spreadsheets. Vendors return responses and evidence through email or shared folders, often without clear guidance. The result is inconsistent answers, missing attachments, and time spent reconciling versions.
With Isora GRC, this entire step is managed through a centralized, guided survey experience.
| Task | Manual Process | With Isora GRC |
| Distribute questionnaires | Sent via email as spreadsheets or documents | Shared as secure, web-based surveys tailored to each vendor |
| Customize questions based on context | Requires manual editing for each vendor version | Built-in logic supports conditional flows and follow-up questions |
| Provide help text or instructions | Requires separate documents or long email explanations | Inline help text explains each question directly within the survey |
| Collect supporting documentation | Files submitted through email or unstructured cloud folders | Vendors upload documents directly to individual questions |
| Manage multiple vendor contributors | Requires version control and manual coordination | Shared link allows vendor teams to collaborate and complete responses together |
| Track completeness of responses | Difficult to verify without checking each response manually | Progress is tracked automatically within the platform |
Explore how Isora’s Questionnaires & Surveys capability supports each of these steps.
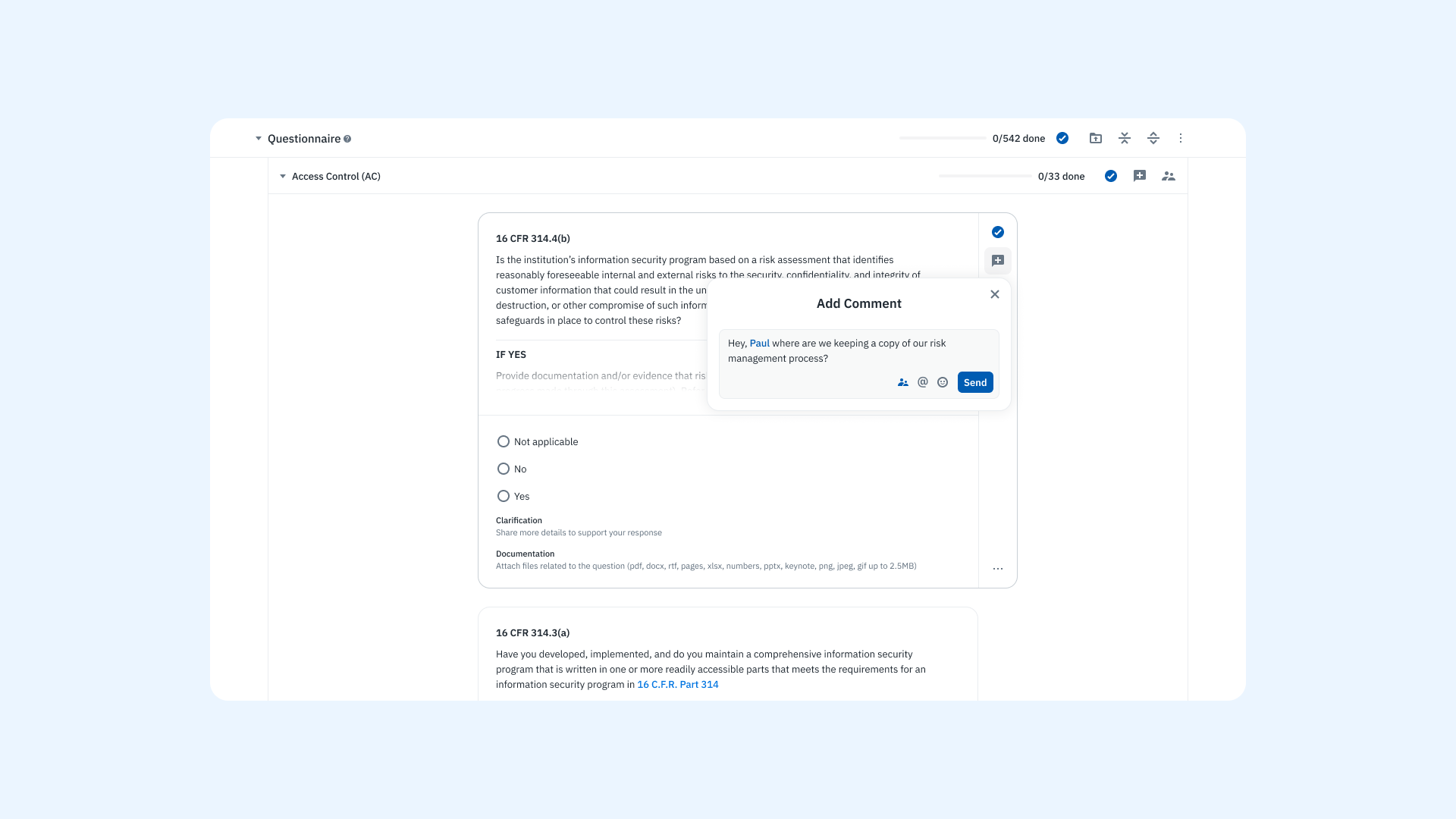
A product screenshot of the questionnaire experience on Isora GRC.
Step 3: Get a signed attestation
Once a vendor has completed the assessment, the next step is to formalize their responses through a signed attestation. This is where the vendor confirms that the information they provided is accurate, complete, and representative of their current security posture.
Attestation is more than a formality. It establishes accountability, creates an auditable record, and reinforces the integrity of the assessment process. For organizations handling regulated data or undergoing audits, this step is essential.
With Isora GRC, attestation is built into the survey workflow to ensure every assessment ends with a clear, verifiable record of vendor accountability.
| Task | Manual Process | With Isora GRC |
| Request attestation | Manually ask the vendor to sign a separate document or email confirmation | Attestation is integrated into the final step of the survey submission |
| Capture vendor contact details | Collected by email or through a separate form | Captured in-platform: name, email, job title, phone number |
| Confirm agreement to attestation terms | Requires custom language or additional attachments | Vendors agree to a pre-set attestation statement directly within the platform |
| Store attestation record | Saved manually or inconsistently across folders or drives | Stored securely alongside the completed assessment for future audits |
| Allow vendor access to responses | Requires manual export and delivery of responses | Vendors can download their full response set in CSV format |
Explore how Isora’s Questionnaires & Surveys capability supports each of these steps.
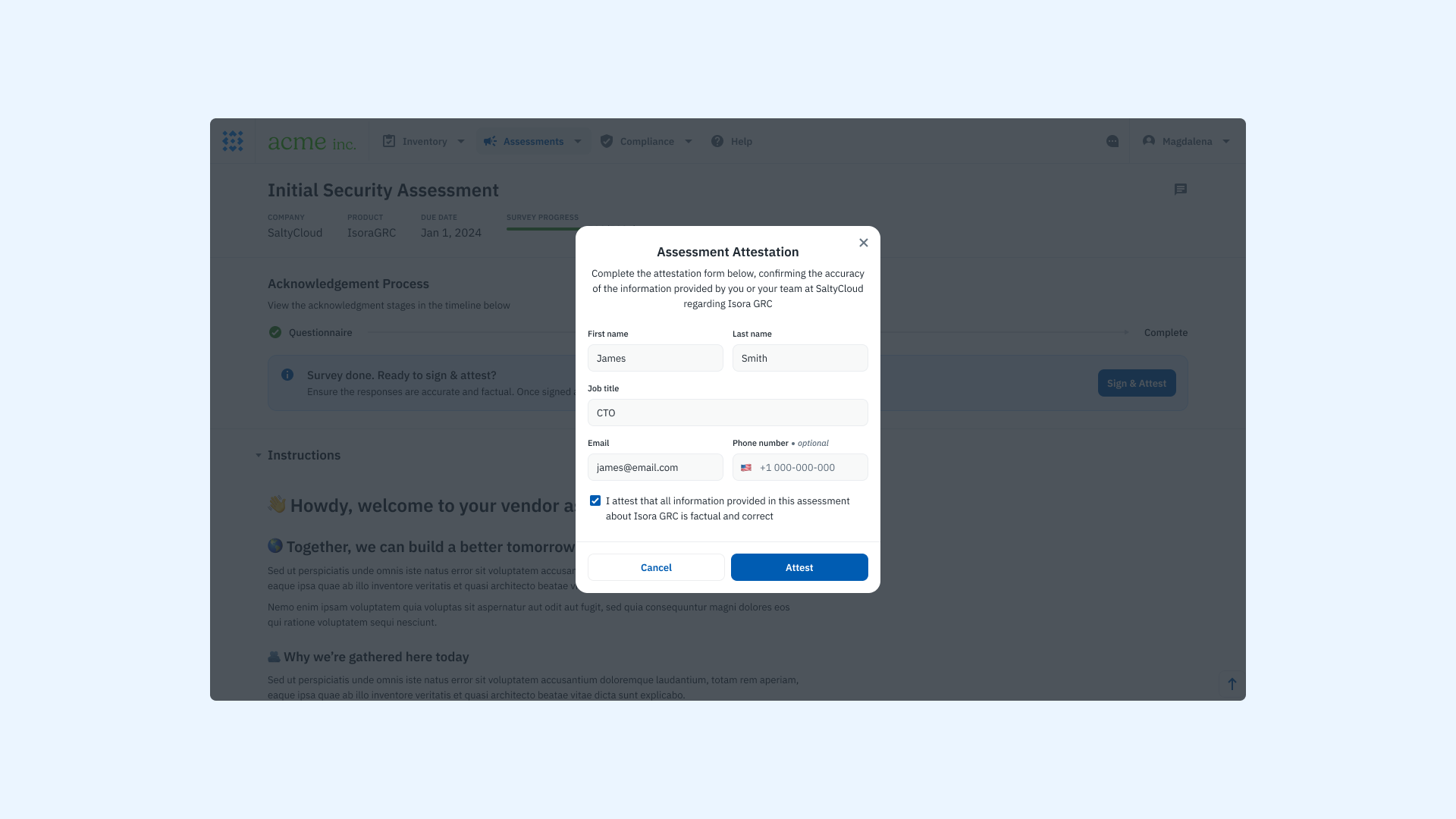
A product screenshot of the vendor attestation form on Isora GRC.
Step 4: Identify, analyze, and evaluate risks
The final step in the assessment process is to review the information collected, identify potential risks, and determine what action to take. This step is critical because it transforms raw responses into meaningful risk decisions that influence vendor approvals, mitigation plans, or contractual obligations.
Risk evaluation requires a close review of each response, evidence item, and area of concern. It is where your team must interpret findings in context, prioritize issues, and document the rationale behind any decisions made.
With Isora GRC, this process is visual, structured, and connected, making it easier to interpret results and act on them.
| Task | Manual Process | With Isora GRC |
| Review survey responses | Manually read through spreadsheet answers and comments | Responses displayed in a structured viewer with categorized insights |
| Organize and score responses | Requires custom scoring logic and formulas in spreadsheets | Scoring is applied automatically across questions and categories |
| Identify weak areas | Time-consuming manual comparisons across answers | Visual widgets highlight low-scoring sections for quick prioritization |
| Drill into supporting evidence | Requires cross-referencing documents in email or shared drives | Evidence is attached directly to the related question and easy to access |
| Flag risks and issues for review | Notes tracked separately or in comments | Risks can be flagged directly within the assessment and added to documentation |
| Compile final evaluation | Built manually from various files and feedback loops | Evaluation summary and scorecard generated in-platform |
Explore how Isora’s Reports & Scorecards capability supports each of these steps.
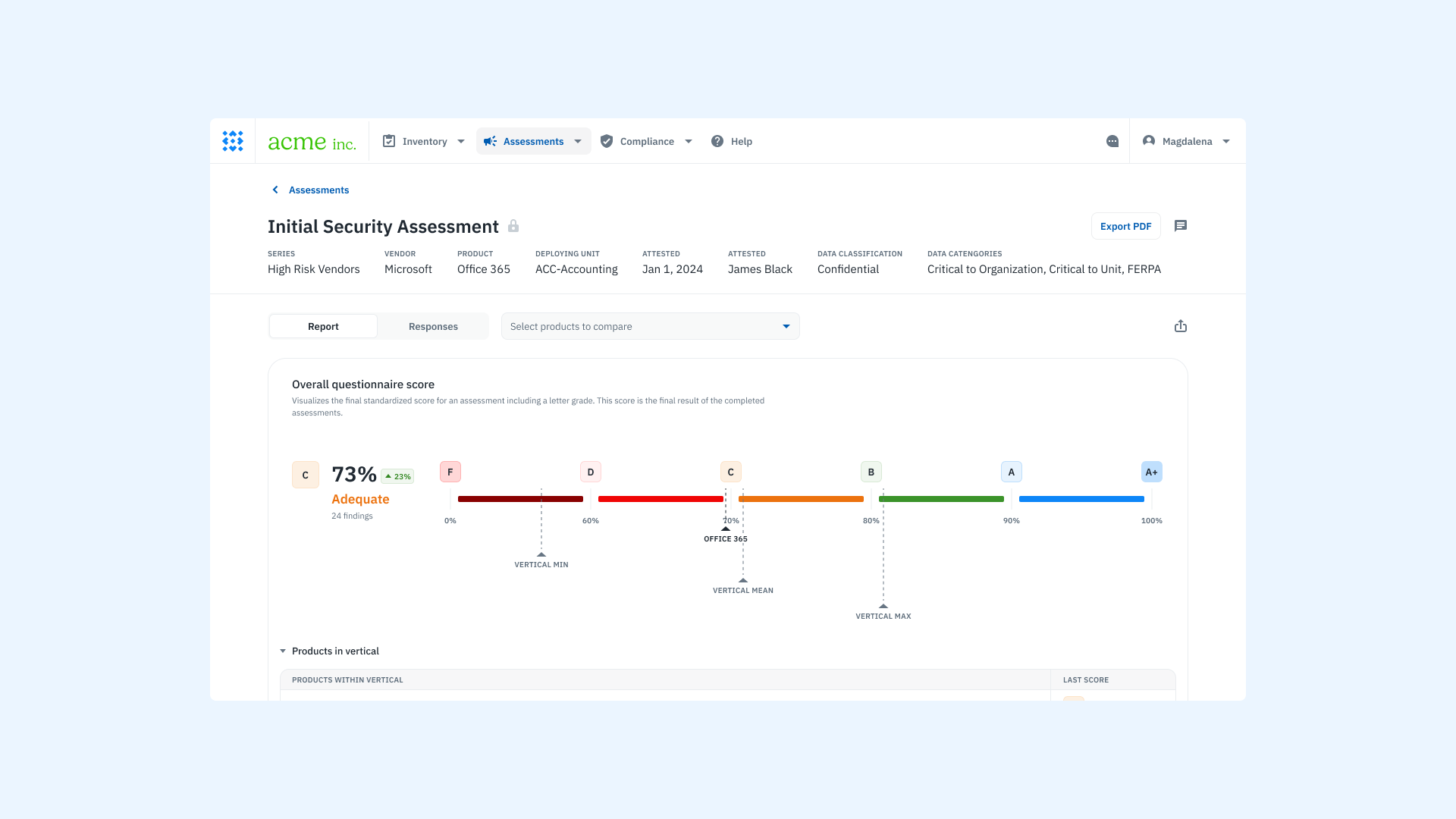
A product screenshot of the vendor scorecard on Isora GRC.
Beyond the assessment
Conducting an assessment is only one part of an effective third-party security risk management program. The next step is translating assessment results into clear decisions, action plans, and ongoing oversight.
Manage risks and exceptions
If a vendor falls short of your minimum security requirements but the business decides to move forward, those risks must be documented and actively managed. A centralized risk register ensures that these decisions are visible, traceable, and revisited over time.
This practice not only maintains accountability but also strengthens the organization’s security culture by treating third-party exceptions as formal risk decisions rather than informal compromises.
Isora makes this process actionable by allowing teams to publish risks directly from assessment findings, assign them to owners, and track them by priority, impact, and treatment plan.
Learn how Isora GRC supports Risk Management and Exception Management.
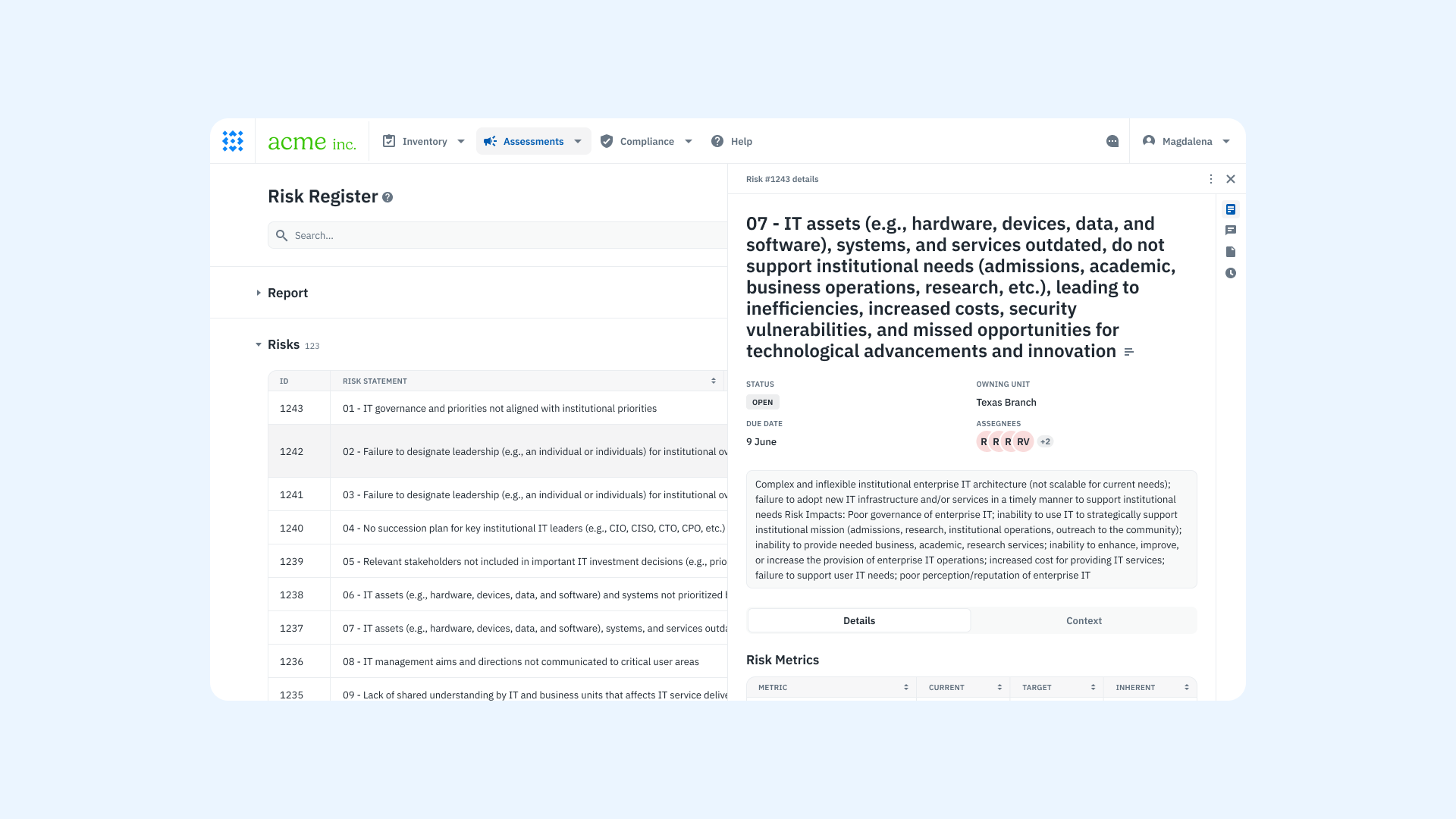
A product screenshot of the risk register on Isora GRC.
Empower stakeholders to make informed decisions
While the security team leads the assessment process, risk ownership often resides with business units and procurement teams. These stakeholders make the final call on whether to accept, mitigate, or avoid a third-party relationship.
The role of the security team is to act as an advisor—interpreting findings, explaining gaps, and outlining potential impacts. Clear communication is critical. When assessments reveal deficiencies, security teams should help stakeholders understand the risks and collaborate on a path forward. This may include recommending remediation steps, suggesting alternative vendors, or outlining compensating controls.
It’s also important to engage data stewards or regulatory leads when sensitive or regulated data is involved. Their input helps ensure any decisions align with legal and compliance obligations.
Learn how Isora GRC enables cross-functional decision-making through Reports & Scorecards.
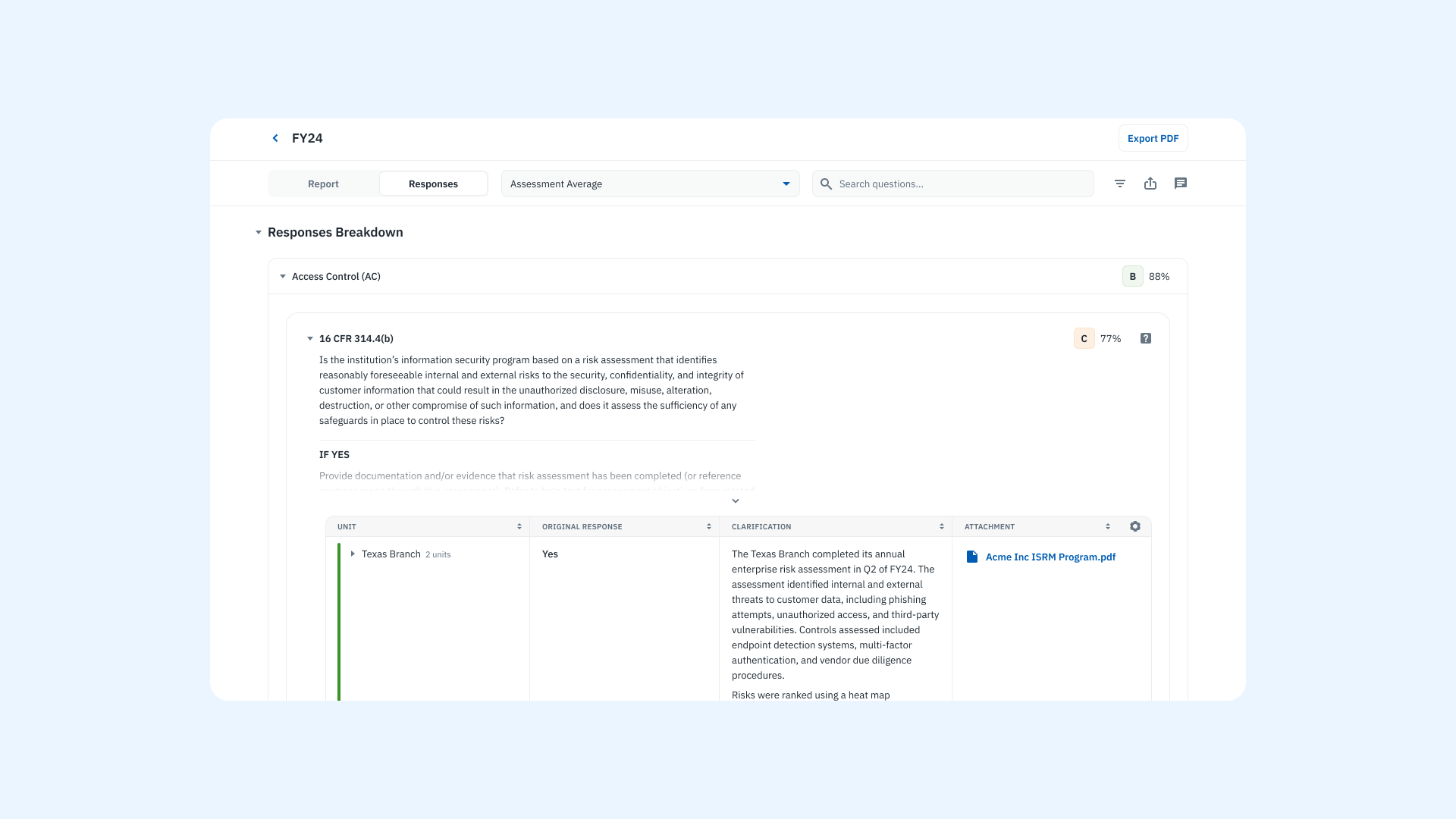
A product screenshot of the questionnaire responses report on Isora GRC.
Maintain a complete third-party inventory
A current inventory of third-party vendors is foundational to any TPSRM program. This inventory should include vendor contact details, ownership information, assessment history, risk status, deployment scope, and associated data classifications.
Beyond being a compliance requirement, this inventory becomes essential during incident response. In the event of a supply chain attack, knowing which vendors are involved, what systems they touch, and who owns the relationship allows for faster containment and recovery.
Isora’s inventory management tools give teams a unified view of vendor data, assessments, and associated risks—all in one place.
Learn how Isora GRC centralizes vendor data and visibility through Inventory Management.
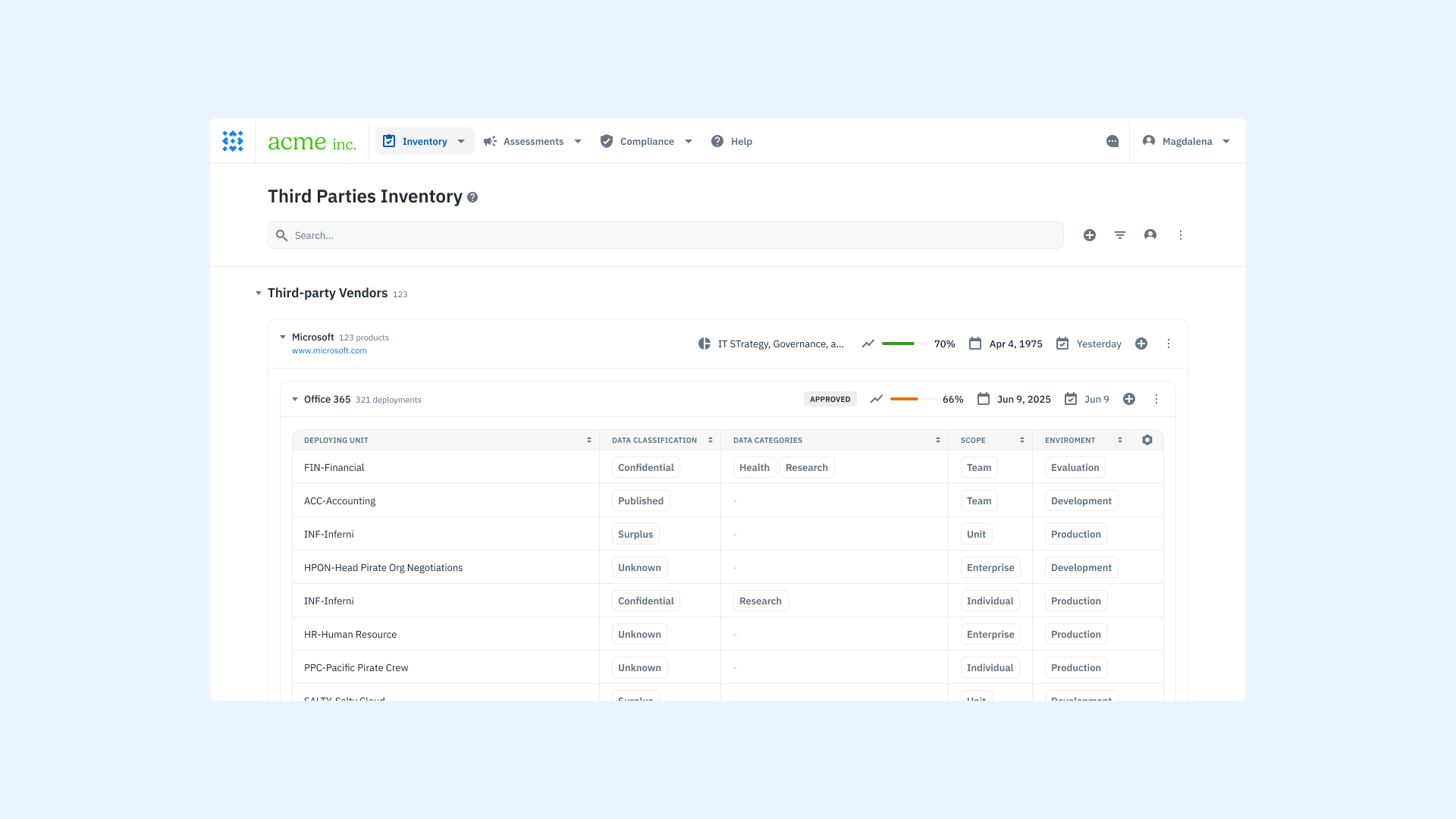
A product screenshot of the vendor inventory on Isora GRC.
Make it a continuous process
Third-party risk management is not a point-in-time effort. Continuous monitoring is essential to stay ahead of changing threats, evolving compliance requirements, and shifts in vendor operations.
Regular reassessments, updated risk intelligence, and automated tracking tools help your team maintain a proactive stance. By embedding these practices into your security operations, you reduce exposure and improve resilience across your extended ecosystem.
Learn how Isora GRC supports ongoing assessments and continuous monitoring through Assessment Management.
Isora GRC for Third-Party Security Risk Assessments
Isora GRC is the GRC Assessment Platform™ purpose-built for security teams managing third-party risk. It replaces fragmented workflows with a single, structured system that helps you run assessments, track vendor risk, and maintain visibility across your external ecosystem.
Instead of relying on spreadsheets, email threads, or generic GRC tools, Isora gives you a streamlined, policy-driven approach to evaluating third parties.
With Isora, you can:
- Launch structured assessments with guided workflows and customizable questionnaires
- Collect complete evidence in one place, with built-in logic and secure file uploads
- Score and analyze responses with real-time insights and visual risk breakdowns
- Assign and manage risks in a collaborative risk register that supports follow-up and accountability
- Maintain a complete vendor inventory with assessment history, ownership, and classification tracking
Whether you’re managing five vendors or five hundred, Isora helps teams move faster, maintain consistency, and support confident decisions across security, compliance, and procurement stakeholders.
Third-Party Security Risk Assessments FAQs
What is the purpose of a third-party security questionnaire?
A third-party security questionnaire is a structured tool used to assess a vendor’s cybersecurity risk posture. It helps your organization evaluate the security measures a third party has in place before granting access to systems, data, or networks. Security teams use these questionnaires to identify gaps, enforce minimum standards, and support informed decision-making in vendor risk management programs.
How does a third-party risk assessment differ from a traditional audit?
A third-party risk assessment focuses on evaluating external business relationships before or during engagement. It is typically narrower in scope than a full audit, targeting key areas such as access control, data protection, business continuity, and incident response. Unlike audits, assessments often rely on standardized questionnaires and evidence reviews to determine risk level in real time, helping security teams respond quickly and consistently.
What types of information should be included in a vendor risk assessment?
A vendor risk assessment should collect information about the third party’s security policies, infrastructure, and past security incidents. This typically includes completed security questionnaires, certifications (such as SOC 2 or ISO 27001), penetration test results, and documented procedures for continuous monitoring, access control, and business continuity. The specific information required will vary depending on the type of data the vendor handles and the level of risk involved.
When should we reassess our third-party vendors?
Vendors should be reassessed on a regular basis as part of a continuous monitoring strategy. High-risk or high-impact vendors may require annual assessments, while lower-risk relationships may be reviewed on a multi-year cycle. You should also trigger reassessments when there are material changes in the vendor’s service, ownership, compliance status, or when a security incident occurs.
Can we standardize our security questionnaires across vendors?
Yes. Many organizations use standardized questionnaires such as SIG, CAIQ, or the HECVAT to streamline vendor reviews. These templates cover common information security domains and are recognized across industries. Standardization helps reduce assessment fatigue for vendors and makes it easier for your team to compare risk levels across multiple relationships. However, it’s common to supplement standardized templates with custom questions to reflect internal policies or data classification requirements.
How do vendor security questionnaires support a broader security program?
Vendor security questionnaires are one of the most practical tools in a proactive cybersecurity risk strategy. They allow security teams to evaluate and document the state of vendor relationships, identify trends across assessments, and inform decisions about procurement, contract terms, and remediation. When tied to a vendor risk management program, they serve as the foundation for tracking third-party cyber risk and improving the maturity of your overall security program.



















 Other Relevant Content
Other Relevant Content