 Table of Contents
Table of Contents
- NIST 800-53 Control Families: All 20 Families Explained
- Overview of NIST 800-53 Control Families
- Complete Table of All 20 NIST 800-53 Control Families
-
Description of Each Control Family
- AC — Access Control (25 base controls)
- AT — Awareness and Training (6 base controls)
- AU — Audit and Accountability (16 base controls)
- CA — Assessment, Authorization and Monitoring (9 base controls)
- CM — Configuration Management (14 base controls)
- CP — Contingency Planning (13 base controls)
- IA — Identification and Authentication (12 base controls)
- IR — Incident Response (9 base controls)
- MA — Maintenance (7 base controls)
- MP — Media Protection (8 base controls)
- PE — Physical and Environmental Protection (23 base controls)
- PL — Planning (11 base controls)
- PM — Program Management (32 base controls)
- PS — Personnel Security (9 base controls)
- PT — PII Processing and Transparency (8 base controls, NEW in Rev 5)
- RA — Risk Assessment (10 base controls)
- SA — System and Services Acquisition (23 base controls)
- SC — System and Communications Protection (51 base controls)
- SI — System and Information Integrity (23 base controls)
- SR — Supply Chain Risk Management (12 base controls, NEW in Rev 5)
- Security vs Privacy: How the Control Families Map
- How Control Families Map to Baselines (Low, Moderate, High)
-
NIST 800-53 Control Families FAQs
- How many control families are in NIST 800-53?
- What are the 20 control families in NIST 800-53?
- What are the two new control families added in Rev. 5?
- What is the largest control family?
- Does every control family apply to every organization?
- How do control families relate to FedRAMP?
- How do control families relate to CMMC?
- Is asset management covered in NIST 800-53?
- Conclusion
NIST 800-53 Control Families: All 20 Families Explained
NIST SP 800-53 organizes its 1,189 security and privacy controls into 20 control families—logical groupings that cover everything from access control to supply chain risk management. Together, these families form the organizational backbone of the entire catalog. Without them, navigating the framework’s 323 base controls and control enhancements would be nearly impossible.
But understanding the 20 control families that comprise 800-53 can also be challenging. This article offers practical guidance with a complete reference table, detailed descriptions of every control family, security-versus-privacy mappings, and baseline distributions across Low, Moderate, and High impact levels.
From compliance analysts mapping controls for the first time to IT security professionals preparing for a FISMA audit or teams evaluating FedRAMP requirements, this guide is the single, bookmarkable reference for all 20 NIST 800-53 controls.
New to NIST Special Publication 800-53? Start with our complete guide to NIST 800-53 for the full introduction.
Overview of NIST 800-53 Control Families
A control family in NIST 800-53 is a grouping of related security or privacy controls that address a common area of protection, like access control, incident response, or system integrity. To make the catalog more navigable, the National Institute of Standards and Technology groups controls that share a security or privacy domain into “families.” That way, organizations can assess and implement them in logical batches rather than one control at a time.
NIST 800-53 control families are the 20 top-level categories used to organize the catalog’s 1,189 security and privacy controls. Each family groups together related controls that address a common domain and is identified by a two-letter abbreviation (e.g., AC for Access Control, AU for Audit and Accountability).
NIST SP 800-53 Rev 5 contains exactly 20 control families—a significant increase from the 18 control families in NIST 800-53 Rev 4. With federal cybersecurity priorities evolving, the addition of two new control families—PT (PII Processing and Transparency) and SR (Supply Chain Risk Management)—reflect an increasingly strict regulatory landscape.
Each family uses a consistent two-letter prefix for its controls. Access Control controls, for example, are labeled AC-1, AC-2, AC-3, and so on. Audit and Accountability controls, on the other hand, begin with AU. Ultimately, this naming convention makes it easier to identify which family any given control belongs to at a glance.
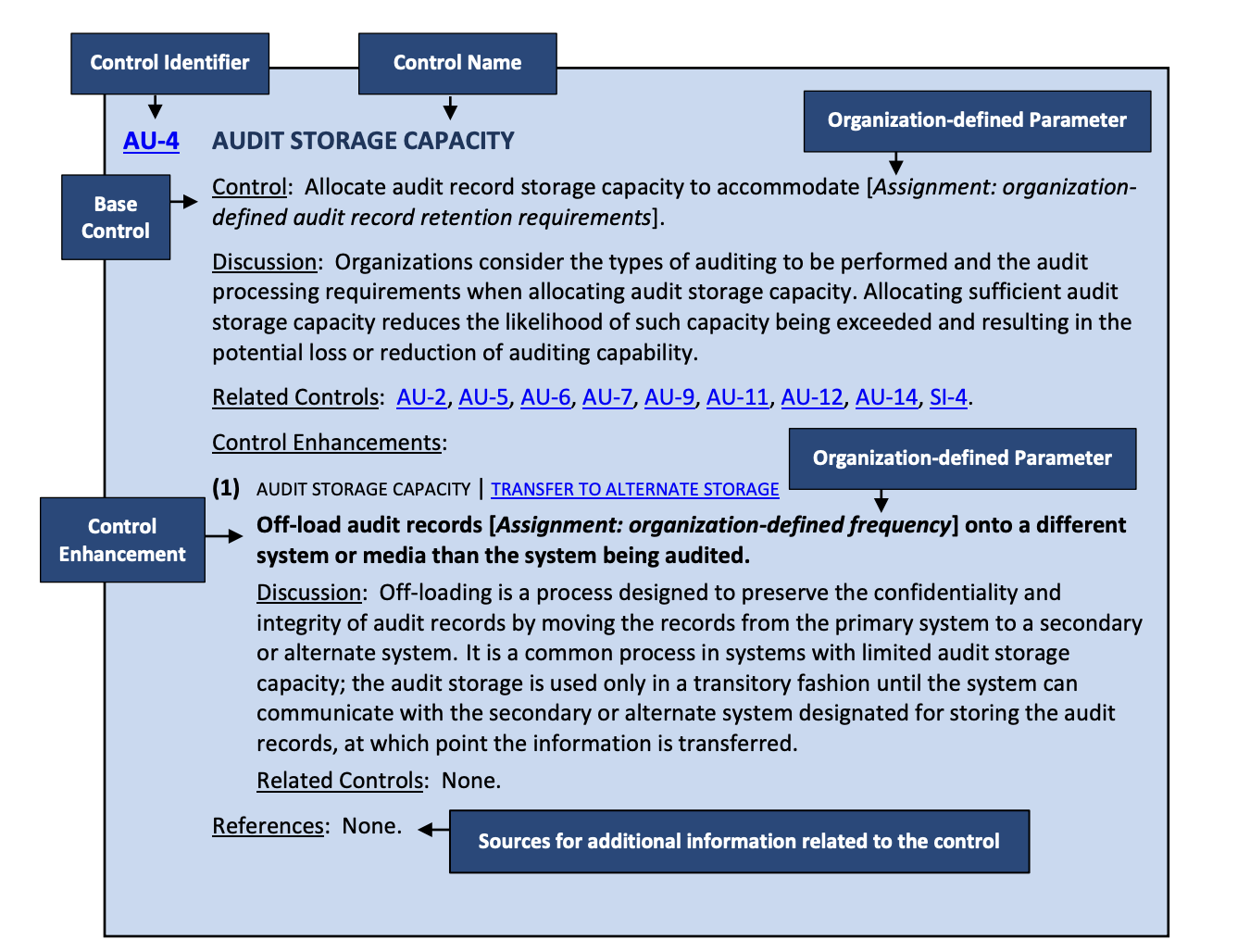
Source: NIST 800-53 Rev 5 (Section 2.2 Figure 1)
The 20 families also range widely in size. The smallest, Awareness and Training (AT), contains just 6 base controls. The largest, System and Communications Protection (SC), contains 51 base controls. No family is ranked above another in importance. Which families matter most depends entirely on an organization’s risk profile, mission requirements, and regulatory obligations.
While the families themselves are defined in SP 800-53, the baseline allocations that determine which controls apply at each impact level are published separately in NIST SP 800-53B.
Complete Table of All 20 NIST 800-53 Control Families
The following table lists all 20 NIST 800-53 Rev 5 control families in official order, with identifier, family name and base control count. This is the definitive reference for the NIST 800-53 control families list.
| # | ID | Family Name | Base Controls | Purpose |
|---|---|---|---|---|
| 1 | AC | Access Control | 22 | System and data access policies |
| 2 | AT | Awareness and Training | 5 | Security and privacy training |
| 3 | AU | Audit and Accountability | 15 | Logging, monitoring, audit trails |
| 4 | CA | Assessment, Authorization, and Monitoring | 8 | Assessments, ATOs, continuous monitoring |
| 5 | CM | Configuration Management | 14 | Baseline configs, change control, inventories |
| 6 | CP | Contingency Planning | 12 | Backup, recovery, continuity |
| 7 | IA | Identification and Authentication | 12 | Identity verification, authentication |
| 8 | IR | Incident Response | 9 | Incident handling, reporting, response |
| 9 | MA | Maintenance | 7 | System maintenance |
| 10 | MP | Media Protection | 8 | Media handling, sanitization |
| 11 | PE | Physical and Environmental Protection | 22 | Facility access, environmental controls |
| 12 | PL | Planning | 8 | Security and privacy planning documents |
| 13 | PM | Program Management | 32 | Organization-wide security program |
| 14 | PS | Personnel Security | 9 | Screening, termination, transfers |
| 15 | PT | PII Processing and Transparency | 8 | PII privacy protections (NEW in Rev 5) |
| 16 | RA | Risk Assessment | 9 | Risk identification, vulnerability scanning |
| 17 | SA | System and Services Acquisition | 16 | Secure development, acquisition |
| 18 | SC | System and Communications Protection | 47 | Encryption, boundary protection |
| 19 | SI | System and Information Integrity | 22 | Flaw remediation, malicious code protection |
| 20 | SR | Supply Chain Risk Management | 12 | Supply chain controls (NEW in Rev 5) |
Note: The counts above are base controls only. When you include control enhancements, NIST 800-53 Rev 5 totals 1,189 controls. How many control families are in NIST 800-53? Exactly 20 — the complete list above.
Now with the full taxonomy established, it’s time to break down what each of these 20 NIST 800-53 control families actually covers.
Description of Each Control Family
Each of the 20 NIST 800-53 control families addresses a distinct security or privacy domain. Here’s what each family covers, including its scope, key controls and practical relevance.
AC — Access Control (25 base controls)
The Access Control family governs who can access systems and data, under what conditions, and with what restrictions. Key controls address account management (AC-2), access enforcement (AC-3), separation of duties (AC-5), least privilege (AC-6), remote access (AC-17), and session management (AC-12). Nearly every organization implementing NIST 800-53 spends significant time on this family as it is one of the broadest in scope.
AT — Awareness and Training (6 base controls)
The Awareness and Training family requires organizations to provide role-based security and privacy training. Its controls cover training content, frequency, and documentation requirements. Although the smallest family by count, it’s also foundational. No amount of technical controls will work if the people using the system aren’t properly trained to follow security policies.
AU — Audit and Accountability (16 base controls)
The Audit and Accountability control family addresses logging, monitoring, and audit trail requirements. It covers event logging (AU-2), content of audit records (AU-3), review and analysis of logs (AU-6), audit storage and retention (AU-11), and non-repudiation (AU-10)—all essential for incident investigation and continuous monitoring.
CA — Assessment, Authorization and Monitoring (9 base controls)
The Assessment, Authorization and Monitoring family covers control assessments, system authorization (also called Authority to Operate or ATO), and continuous monitoring programs. Closely connected to the Risk Management Framework (RMF) outlined in NIST SP 800-37, the CA controls are intended to help organizations evaluate whether their security controls are implemented correctly and operating as intended.
CM — Configuration Management (14 base controls)
The Configuration Management family addresses baseline configurations, change control processes, and system inventories. CM-8 (System Component Inventory) is particularly important because it requires organizations to maintain a comprehensive inventory of all hardware, software, and firmware components. The CM family effectively makes IT asset inventory management a NIST 800-53 compliance requirement as a result.
CP — Contingency Planning (13 base controls)
Contingency Planning covers business continuity and disaster recovery for continuous operations during and after disruptions. The controls in this family address plan development (CP-2), training (CP-3), testing (CP-4), backup and restoration (CP-9), and alternate processing and storage sites (CP-6, CP-7).
IA — Identification and Authentication (12 base controls)
The IA family governs how users and devices prove their identities. It covers password management, multi-factor authentication (MFA), cryptographic authentication, and identity proofing. IA controls have become increasingly central to federal cybersecurity strategies with the rise of zero-trust architectures over the last few years.
IR — Incident Response (9 base controls)
Incident Response controls require organizations to detect, report, and respond to security incidents effectively. The family covers response plan development (IR-1), training (IR-2), testing (IR-3), incident handling procedures (IR-4), and coordination with external organizations (IR-6). In fact, having a documented, tested incident response plan is a baseline requirement at all impact levels.
MA — Maintenance (7 base controls)
The Maintenance control family addresses system maintenance activities, including maintenance tools, nonlocal (remote) maintenance, and maintenance over personnel. While smaller in scope, MA controls ensure that routine maintenance activities do not introduce security vulnerabilities.
MP — Media Protection (8 base controls)
Media Protection governs how organizations handle, sanitize, and dispose of physical and digital media. With controls covering media access, marking, storage, transport, and destruction, this family is often most relevant for organizations that handle classified or sensitive information.
PE — Physical and Environmental Protection (23 base controls)
This large family addresses physical facility security with controls that cover physical access control, visitor management, monitoring, emergency shutoff, power equipment, temperature and humidity controls, and fire protection. Any organization operating its own data center or server rooms must implement PE controls.
PL — Planning (11 base controls)
The Planning family requires organizations to develop and maintain security and privacy plans for each system. Notable PL controls address plan development (PL-2), rules of behavior (PL-4), and security architecture documentation (PL-8).
PM — Program Management (32 base controls)
Program Management is the second-largest family by base control count. It addresses organization-wide security program requirements, including the information security program plan (PM-1), assignment of senior officials (PM-2), risk strategy (PM-9), and enterprise architecture (PM-7). Importantly, PM controls operate at the organizational level rather than the system level.
PS — Personnel Security (9 base controls)
Personnel Security covers the entire employee lifecycle as it relates to security, including screening before hiring, access agreements, termination procedures, and personnel transfers. These controls ensure that people with access to systems are trustworthy and that privileges are revoked promptly whenever roles change.
PT — PII Processing and Transparency (8 base controls, NEW in Rev 5)
Introduced in NIST 800-53 Rev 5, the PT control family establishes requirements for handling personally identifiable information (PII) in a manner that supports privacy protections. It covers authority to process PII, purpose specification, consent, privacy notices and data minimization. Previously addressed in Appendix J of Rev 4, these controls were recently incorporated into the main catalog of NIST 800-53 in Rev 5.
RA — Risk Assessment (10 base controls)
The Risk Assessment family requires organizations to identify risks, perform vulnerability scanning, and determine risk responses. Here, RA-2 (Security Categorization) is especially significant. It mandates that organizations categorize their systems using FIPS 199, which directly determines the applicable control baseline.
SA — System and Services Acquisition (23 base controls)
The SA family addresses security throughout the system development lifecycle and in third-party acquisitions. Controls cover developer testing, security engineering principles, outsourced information system services, and supply chain considerations (complementing the new SR family).
SC — System and Communications Protection (51 base controls)
SC is the largest control family in NIST 800-53 by base control count. It covers encryption, network boundary protection, network segmentation, cryptographic key management, and secure communication channels. Given the breadth of modern network architectures, this family addresses a wide range of technical safeguards.
SI — System and Information Integrity (23 base controls)
The SI family focuses on maintaining the integrity of information and systems. Here, controls address flaw remediation (patching), malicious code protection (antivirus/antimalware), security monitoring, software and firmware integrity verification, and spam protection.
SR — Supply Chain Risk Management (12 base controls, NEW in Rev 5)
Also introduced in NIST 800-53 Rev 5, the SR family addresses supply chain risk assessment, acquisition strategies, component provenance, and authenticity verification. It responds to growing threats targeting hardware and software supply chains and provides a structured approach to managing third-party risk.
Security vs Privacy: How the Control Families Map
NIST 800-53 Rev 5 integrates privacy controls directly into the catalog alongside security controls, rather than isolating them in Appendix J as Rev 4 did. One of the most significant structural changes in the NIST 800-53 Rev 5 update, this shift reflects the reality that security and privacy are deeply interconnected. Most families now contain both types of controls as a result.
Understanding which families lean toward security, privacy or both can help organizations assign the right reviewers and stakeholders during implementation. For instance, a Chief Information Security Officer (CISO) and a Chief Privacy Officer (CPO) might focus on different control families during a compliance assessment. That said, a universal map of NIST 800-53 security and privacy controls might not be particularly useful for many organizations. Instead, a custom approach—where controls are identified, mapped, and configured for a specific environment—tends to add more value in the long term.
How Control Families Map to Baselines (Low, Moderate, High)
NIST SP 800-53B defines three control baselines based on system impact level: Low, Medium, and High. However, not every control in every family applies to every system. Determined by FIPS 199 categorization, these baselines tell organizations exactly which controls from each family they must implement.
The three baselines also differ significantly in control counts:
- Low baseline (149 controls): For systems where a breach would have a limited adverse effect.
- Moderate baseline (287 controls): For systems where a compromise could have a serious adverse effect, such as significant operational disruption, financial loss or harm to individuals. Moderate is the most commonly applied baseline across federal agencies and higher education institutions.
- High baseline (370 controls): For systems where a compromise could result in severe or catastrophic consequences, including mission failure or widespread harm.
Most of the 20 control families contribute security controls to all three baselines. The difference is how many controls from each family are required at each impact level. As impact levels rise, higher baselines do not introduce new control families. Instead, they require additional controls and control enhancements within the same families to address increased risk exposure.
The Program Management (PM) and PII Processing and Transparency (PT) families, however, are not assigned directly to the Low, Moderate or High baselines in SP 800-53B. Instead, these controls are selected based on organization-wide governance needs or system specific privacy requirements.
| Family | Low | Moderate | High |
|---|---|---|---|
| AC (Access Control) | 10 | 17 | 21 |
| AU (Audit and Accountability) | 6 | 12 | 14 |
| CM (Configuration Management) | 6 | 11 | 13 |
| IA (Identification and Authentication) | 7 | 10 | 11 |
| SC (System and Communications Protection) | 10 | 22 | 32 |
| All 20 families (total) | 149 | 287 | 370 |
Notably, the jump in required controls from Low to Moderate is substantial—nearly double. The jump from Moderate to High might seem smaller, but it still adds 95 controls total. While organizations subject to the Federal Information Security Modernization Act (FISMA) or pursuing FedRAMP authorization must match their baseline to their FIPS 199 categorization, voluntary adopters—such as private-sector organizations using NIST 800-53 as a best-practice framework—can tailor baselines to their specific risk environment.
NIST 800-53 Control Families FAQs
How many control families are in NIST 800-53?
NIST 800-53 Rev 5 contains 20 control families, up from 18 in Rev 4. The two new families added in Rev 5 are PT (PII Processing and Transparency) and SR (Supply Chain Risk Management). Together, these 20 families organize the catalog’s 1,189 security and privacy controls.
What are the 20 control families in NIST 800-53?
The 20 families are: AC (Access Control), AT (Awareness and Training), AU (Audit and Accountability), CA (Assessment, Authorization, and Monitoring), CM (Configuration Management), CP (Contingency Planning), IA (Identification and Authentication), IR (Incident Response), MA (Maintenance), MP (Media Protection), PE (Physical and Environmental Protection), PL (Planning), PM (Program Management), PS (Personnel Security), PT (PII Processing and Transparency), RA (Risk Assessment), SA (System and Services Acquisition), SC (System and Communications Protection), SI (System and Information Integrity) and SR (Supply Chain Risk Management). Each two-letter abbreviation represents a distinct security or privacy domain.
What are the two new control families added in Rev. 5?
PT (Personally Identifiable Information Processing and Transparency) contains 8 base controls addressing PII handling, consent and data minimization. SR (Supply Chain Risk Management) contains 12 base controls addressing supply chain risk assessment, component provenance and authenticity. PT formalized privacy requirements that previously lived in Rev 4’s Appendix J, while SR responded to escalating supply chain threats.
What is the largest control family?
SC (System and Communications Protection) is the largest family with 51 base controls. It covers encryption, network boundary protection, segmentation, and cryptographic key management. AC (Access Control) is the broadest in scope with 25 base controls plus numerous enhancements, making it one of the most implementation-intensive families.
Does every control family apply to every organization?
No. Which controls within each family apply depends on the system’s impact level (Low, Moderate, or High) as defined by FIPS 199 and the corresponding baselines in SP 800-53B. Organizations can further tailor their control selections based on risk assessment results and regulatory requirements such as FISMA or FedRAMP.
How do control families relate to FedRAMP?
FedRAMP uses NIST 800-53 control families as its foundation with added parameters and requirements on top of the standard baselines. Cloud Service Providers (CSPs) pursuing FedRAMP authorization must implement controls from all 20 families at their designated authorization level (Low, Moderate, or High).
How do control families relate to CMMC?
The Cybersecurity Maturity Model Certification (CMMC) framework is also derived from NIST 800-53 via NIST SP 800-171. Organizations pursuing CMMC certification often find that many required practices map directly to NIST 800-53 control families, particularly in areas such as access control incident response and system integrity.
Is asset management covered in NIST 800-53?
Yes. The CM (Configuration Management) family addresses asset management through CM-8 (System Component Inventory), which requires organizations to maintain a comprehensive inventory of hardware, software, and firmware components, and CM-9 (Configuration Management Plan). The RA (Risk Assessment) family also requires asset identification as part of the risk identification process.
Conclusion
The 20 NIST 800-53 control families organize 1,189 security and privacy controls into a navigable structure that scales from small agencies to large federal departments. Whether implementing at the Low baseline (149 controls) or the High baseline (370 controls), the family structure is the best roadmap for understanding what the framework requires and where compliance gaps lie.
For a comprehensive introduction to the framework beyond control families, check out our complete guide to NIST 800-53.
Managing controls across all 20 families is simpler with purpose-built NIST 800-53 compliance software solutions like Isora GRC.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.
Dive into our research-backed resources–from product one pagers and whitepapers, to webinars and more–and unlock the transformative potential of powerfully simple GRC.
Learn More


















 Other Relevant Content
Other Relevant Content