 Table of Contents
Table of Contents
- Glossary of Key IT Risk Register Terms
- What is an IT Risk Register and Why is it Used?
- What Should be in an IT Risk Register?
- Why NIST IR 8286 Is the Leading Framework for IT Risk Registers
-
10 Steps to Manage Your Risk Register (NIST-Aligned)
- 1. Establish Risk Context and Strategy
- 2. Identify and Describe Risks
- 3. Record Risks in the Register
- 4. Assess Likelihood and Impact
- 5. Calculate Exposure and Prioritize
- 6. Assign Risk Owners
- 7. Determine and Document Responses
- 8. Track Risk Status and Mitigation Progress
- 9. Aggregate and Report Risks to Leadership
- 10. Continuously Monitor and Refresh the Register
- How Isora GRC Streamlines IT Risk Register Management
- Final Tips on Managing Your IT Risk Register Successfully
-
IT Security Risk Register FAQs
- What is the IT security risk management process?
- What is a risk register in information security?
- How do I create an IT risk register template?
- Who is responsible for managing risks in the register?
- How does a risk register support cybersecurity risk management?
- What is the difference between a risk register and a risk assessment?
- How often should an IT risk register be updated?
- How does a risk register support compliance?
- Can I use the same register for third-party and internal risks?

Managing cybersecurity risk requires more than just awareness. It requires structure, accountability, and alignment across teams.
Without the right tooling, process, or organizational support, even well-intentioned security programs struggle to track and mitigate threats effectively.
That’s where an IT security risk register comes in. Also known as a cybersecurity risk register, it serves as a central system of record for documenting, prioritizing, and managing identified risks across your systems, business units, and vendors.
In this guide, we’ll explain what a risk register is, why it matters, and how to structure and maintain one using authoritative guidance from NIST IR 8286. Whether you’re starting from scratch or improving an existing register, this guide will help you build a practical, scalable foundation for managing cybersecurity risk.
Let’s dive in!
Glossary of Key IT Risk Register Terms
Clear terminology is essential when managing cybersecurity risks across systems, departments, and third parties. This glossary defines the most important terms related to IT security risk registers, drawing from authoritative sources including NIST IR 8286, NIST SP 800-30, and the OCEG GRC Glossary.
Use this reference to align your team’s understanding of risk concepts, support consistent documentation, and ensure your register remains a useful decision-support tool—not just a list of issues.
| Term | Definition | Source |
| Risk Register | A structured tool for capturing cybersecurity risks, their metadata, and their current treatment state. | NIST |
| Risk Identification | The process of discovering risks that could affect information systems or business operations. | NIST |
| Risk Description | A clear, structured statement of the risk, including threat, vulnerability, asset affected, and consequence. | NIST |
| Likelihood | The estimated probability that a threat event will occur. | NIST |
| Impact | The expected severity of harm resulting from the realization of a risk. | NIST |
| Residual Risk | The risk that remains after controls or mitigation actions are applied. | NIST / OCEG |
| Risk Owner | The individual or role responsible for managing a specific risk, including mitigation and reporting. | NIST |
| Risk Response | The chosen action to address a risk: accept, avoid, mitigate, or transfer. | NIST |
| Control Deficiency | A weakness in a control that allows unacceptable risk to persist. | Common Use / NIST |
| Risk Categorization | Grouping risks into types (e.g., operational, strategic, compliance) to support prioritization and reporting. | NIST |
| Risk Exposure | A calculated combination of likelihood and impact; used to assess severity and prioritize risks. | NIST |
| Risk Aggregation | The process of combining individual risks from across systems or units to create an enterprise view. | NIST |
| Risk Appetite | The level and types of risk an organization is willing to accept in pursuit of its goals. | NIST / OCEG |
| Accept (Design Option) | A decision to intentionally tolerate a known risk without further treatment. | OCEG |
| Avoid (Design Option) | A response in which the activity giving rise to the risk is discontinued. | OCEG |
| Transfer (Design Option) | Shifting risk to a third party, such as through contracts or insurance. | OCEG |
| Control (Design Option) | Applying controls or safeguards to reduce risk likelihood, impact, or both. | OCEG |
| Assurance | Structured confidence that risk controls are adequate and working as intended. | OCEG |
| Review Frequency | How often a risk entry or control is reviewed for status and effectiveness. | Operational Practice |
| Control Risk | The risk that a control fails to detect or prevent a risk event. | OCEG |
| Exposure Rating | A score derived from combining likelihood and impact; may include qualitative or quantitative factors. | NIST |
| Continuous Monitoring | Ongoing tracking of risk status, control effectiveness, or threat conditions over time. | NIST |
| Security Risk Documentation | Written evidence supporting how risks were assessed, managed, and monitored. | Common Use |
What is an IT Risk Register and Why is it Used?
An IT risk register is a structure tool used to list, track, and manage information security risks in one place. It’s a part of any strong information security risk management (ISRM) program and holds key details like risk descriptions, likelihood, impact, affected assets, response strategies, and current status. Each entry provides a clear snapshot of what could go wrong, who owns the risk, and what’s being done to address it.
When used effectively, a risk register keeps teams aligned across security, IT, leadership, and business units. It supports better decision-making by helping teams prioritize risks, take proactive action, and avoid last-minute surprises. Instead of reacting to incidents, organizations can stay focused on the highest-risk areas with the greatest potential impact.
In addition to keeping teams aligned and improving planning, it plays a key role in demonstrating compliance with security controls frameworks (e.g., NIST CSF, NIST 800-53, CIS, etc.), protecting sensitive data, and tying security work to business risk. It is a source of record that helps security teams show they’re identifying, monitoring, and mitigating IT risks in a structured and auditable way.

What Should be in an IT Risk Register?
Think of your IT risk register as a project management system for cybersecurity risks. Each risk functions like a task or unit of work, complete with context, ownership, status, and action plans. A well-structured register doesn’t just log risks. It enables teams to track how each risk is evaluated, prioritized, assigned, and resolved over time.
After conducting a risk assessment (such as through a structured questionnaire), the next step is to record each risk in a centralized register using a consistent format. This turns raw assessment findings into actionable records.
Based on NIST IR 8286, each risk entry should follow a structured schema that captures not just what the risk is, but also what it affects, how likely it is, how severe the impact could be, and how the organization plans to respond.
| Element | What It Captures | Example |
| Risk ID | Unique identifier for tracking and reference | 0043 |
| Risk Description | A clear, concise summary of the risk | If the HR system lacks MFA, unauthorized access may expose sensitive employee data |
| Category | Risk type or domain (based on internal taxonomy or control framework) | Access Control |
| Likelihood | Probability of the risk occurring (can be qualitative or quantitative) | Likely |
| Impact | Expected severity of the risk’s effect on the organization | High |
| Exposure | Current level of risk before treatment (inherent risk) | High |
| Risk Owner | Individual or role responsible for managing the risk | IT Security Manager |
| Response Type | Chosen strategy: Mitigate, Accept, Avoid, or Transfer | Mitigate |
| Response Description | Planned treatment action and timeline | Implement MFA via SSO provider by Q3 |
| Response Cost | Estimated cost of implementing the risk treatment | $12,000 |
| Status | Current stage in the risk lifecycle | In Progress |
Tailoring Your Register to Your Risk Strategy
While the risk register elements defined in NIST IR 8286 provide a strong foundation, organizations should tailor their register to reflect their specific risk management approach. Some may operate with a tight focus on IT operations, while others integrate cybersecurity risks into broader enterprise risk management (ERM) frameworks like COSO.
| Field | Purpose | Example |
| Linked Business Objective | Connects risk to a strategic goal or KPI | “Protect employee data to meet privacy compliance objectives” |
| Residual Risk | Captures remaining risk after mitigation | Moderate |
| Control Reference / Gap | Identifies relevant control or missing safeguard | NIST SP 800-53 AC-7: Unsuccessful Login Attempts |
| Review Frequency | Ensures regular governance and review cycles | Quarterly |
| Affected Asset or System | Links the risk to the impacted system, data, or vendor | HR Management System |
Your register should reflect how your organization thinks about risk, whether operational, strategic, or both. The more your structure mirrors how decisions are made, the more valuable the register becomes as a tool for leadership alignment, resource prioritization, and audit readiness.
Why NIST IR 8286 Is the Leading Framework for IT Risk Registers
When it comes to building and maintaining an IT security risk register, NIST IR 8286 provides the most practical and prescriptive guidance available. While many organizations rely on high-level frameworks like NIST RMF, ISO 31000, or COSO ERM to define how risk is governed, those frameworks don’t explain how to actually document, manage, and use cybersecurity risks in a way that supports real operational decision-making. That’s where IR 8286 comes in.
NIST IR 8286 defines the structure and lifecycle of a risk register specifically for cybersecurity. It outlines how to capture individual risks using standardized fields—such as risk description, likelihood, impact, affected asset, control gaps, risk owner, and response strategy—so that information can be aggregated, updated, and acted on.
What sets it apart is its focus on traceability (linking risks to assets and controls), cross-enterprise integration (supporting distributed ownership across departments), and lifecycle management (ensuring risks are continuously reviewed and updated).
To understand where IR 8286 fits, it’s helpful to view it alongside the broader framework ecosystem:
| Framework Type | Purpose | Example Frameworks |
| Risk Governance | Define how risk is managed across the organization (policy, ownership, oversight) | NIST RMF, ISO 31000, COSO ERM |
| Risk Assessment | Provide methods for evaluating risk likelihood and impact | NIST SP 800-30 |
| Security Controls | Define technical and administrative safeguards for reducing risk | NIST SP 800-53, ISO/IEC 27001, CIS Controls |
| Risk Register Management | Define how to document, track, and operationalize risks across assets and units | NIST IR 8286 |
10 Steps to Manage Your Risk Register (NIST-Aligned)
A well-maintained IT risk register is essential for managing cybersecurity risks efficiently. The following steps, rooted in guidance from NIST IR 8286A, offer a practical framework for building and maintaining a dynamic, actionable risk register.
1. Establish Risk Context and Strategy
Begin by defining your risk appetite and risk tolerance, aligning them with organizational goals. This step ensures that your risk management activities fit within the larger enterprise risk management (ERM) strategy.
“Leaders at Levels 1 and 2 define specific and measurable risk appetite and risk tolerance statements that reinforce enterprise mission objectives and organization goals.” (NISTIR 8286A, Sec. 2.1.3)
2. Identify and Describe Risks
Gather data from multiple sources—assessments, audits, incidents—and articulate risk descriptions. Clear, structured risk statements should identify potential risks and vulnerabilities, their likelihood, and their possible impacts.
“NISTIR 8286A details methods for completing and maintaining that risk register by identifying threats and analyzing the likelihood of successful exploitation of certain conditions that result in threat events, the estimated impact on enterprise objectives, and whether estimates are within established risk tolerance parameters.” (NISTIR 8286A, p. 11)
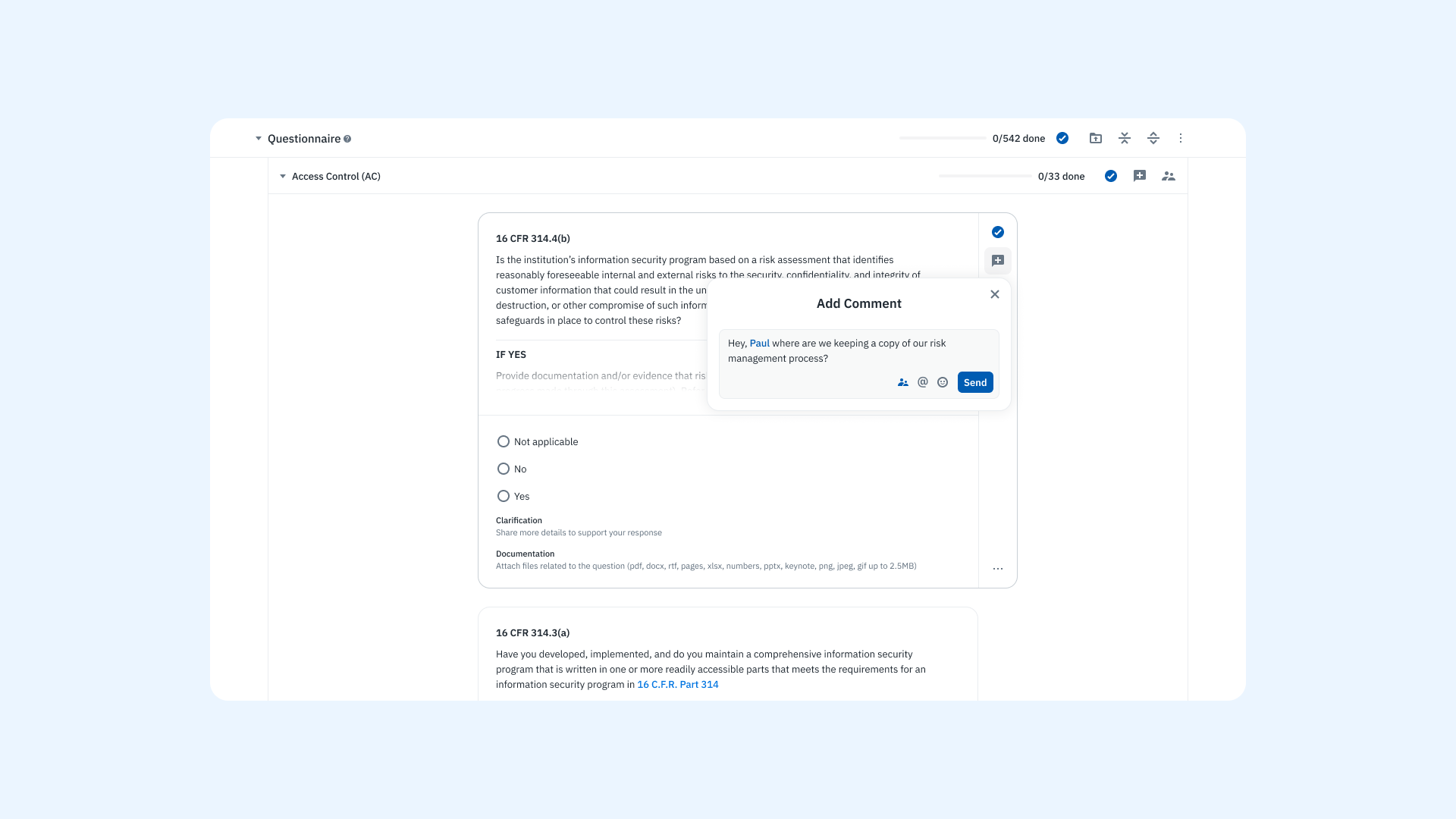
3. Record Risks in the Register
For each risk, fill in standardized fields such as risk ID, description, category, likelihood, impact, risk owner, and risk response. This is where the risk becomes actionable, documented, and tracked in your cybersecurity risk register.
“A risk register is a key tool to document, communicate, and manage cybersecurity risk at each level of the enterprise.” (NISTIR 8286A, p. 11)
“Figure 4 provides an example of a blank risk register. The red box shows fields that are relevant to the processes described in this report.” (NISTIR 8286A, Fig. 4)
4. Assess Likelihood and Impact
Evaluate the likelihood of each risk materializing and assess the potential impact if the risk occurs. Use established scales to gauge severity, considering both inherent and residual risk, before and after applying controls.
“As risks are identified (including calculation of likelihood and impact), the risk register will be populated with relevant information once decisions have been made.” (NISTIR 8286A, p. 11)
5. Calculate Exposure and Prioritize
Combine likelihood and impact to determine exposure or risk scores. Prioritize risks based on their potential effect on organizational objectives, ensuring that resources go toward mitigating the most pressing risks first.
Isora can help visualize and simplify risk aggregation and prioritization across your organization, strengthening operational and strategic risk management.
“Current Assessment – Exposure Rating: A calculation of the probability of risk exposure based on the likelihood estimate and the determined benefits or consequences of the risk. Other common frameworks use different terms for this combination, such as level of risk (e.g., ISO 31000, NIST SP 800-30 Rev. 1).” (NISTIR 8286A, Fig. 4)
6. Assign Risk Owners
Assign a risk owner to each item. This individual will oversee the risk mitigation strategy, track progress, and ensure the response aligns with organizational objectives. Clear ownership ensures accountability.
“The Risk Owner may work with a designated Risk Manager who is responsible for managing and monitoring the selected risk response.” (NISTIR 8286A, Fig. 4)
7. Determine and Document Responses
Choose a proper risk response—accept, mitigate, transfer, or avoid—and document the planned mitigation strategies. This step directly impacts how you deal with each risk.
“The risk response (sometimes referred to as the risk treatment) for handling the identified risk.” (NISTIR 8286A, Fig. 4)
8. Track Risk Status and Mitigation Progress
Keep a record of the risk status (open, in-progress, closed) and monitor the effectiveness of mitigation efforts. Continuous risk monitoring is key to ensuring that risks remain within acceptable levels.
“A field for tracking the current condition of the risk.” (NISTIR 8286A, Fig. 4)
“The risk register should be updated regularly as risks are identified, assessed, and responded to.” (NISTIR 8286A, p. 11)
9. Aggregate and Report Risks to Leadership
As risks evolve, aggregate data from various business units or systems and generate risk reports for leadership. Use visualizations like risk matrices to provide a clear overview of risk exposure.
“CSRRs [Cybersecurity Risk Registers] are aggregated at appropriate levels, then used to create an enterprise cybersecurity risk register, which provides input into the broader Enterprise Risk Register (ERR).” (NISTIR 8286A, p. 12)
10. Continuously Monitor and Refresh the Register
Risk management is a continuous process. Regularly review and update your risk register as new risks surface, old risks evolve, or mitigation measures finish. Ensure real-time risk updates so the register remains relevant.
“It is important for the enterprise to ensure that the model is used in a consistent and iterative way. As risks are identified … the risk register will be populated with relevant information once decisions have been made. As risk responses are applied to each item in the risk register, the updated state of that risk will become the new current state in the next assessment cycle.” (NISTIR 8286A, p. 11)
How Isora GRC Streamlines IT Risk Register Management
Managing IT risk with spreadsheets or static tools is slow, error-prone, and hard to scale. Isora GRC replaces those outdated processes with a modern platform built for security teams to track, prioritize, and respond to risk in real time.
Here’s how Isora GRC supports effective risk register operations.
Identify Risks Through Structured Assessments
Use built-in, customizable questionnaires aligned to standards like NIST and CIS to uncover security gaps across systems, units, or vendors. Responses are automatically mapped to potential risks, reducing manual effort.
Track and Prioritize Risks in One Platform
Move from fragmented spreadsheets to a centralized risk register with fields for likelihood, impact, risk owner, response strategy, and mitigation status. Capture residual risk and link directly to assessment data for full traceability.
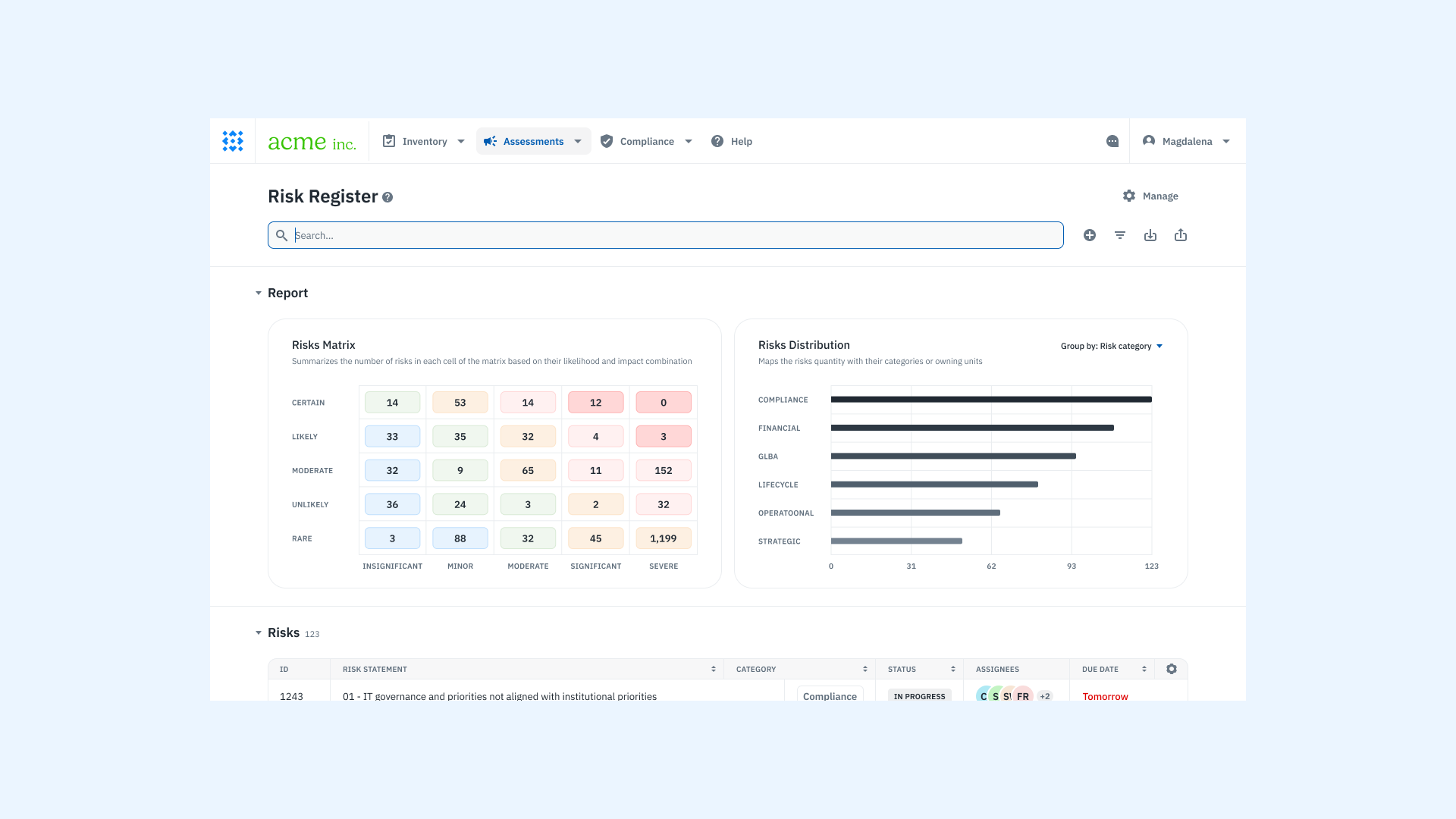
Visualize and Act on Risk Insights
Use built-in risk matrices and dashboards to prioritize the most critical risks. Understand where risks exist, how they’re changing, and what actions are in progress—all in real time.
Enable Cross-Team Accountability
Assign risks to departments or units, collaborate on mitigation steps, and keep leadership aligned with transparent tracking and reporting.
With Isora GRC, information security risk management becomes part of your daily operations, not a once-a-year exercise in a spreadsheet. You get structured data, simplified workflows, and full visibility into how risks are being identified, evaluated, and resolved.
Final Tips on Managing Your IT Risk Register Successfully
To wrap things up, managing your IT risk register is crucial for staying ahead of cybersecurity risks and ensuring your organization is well-prepared. Let’s close this out with a few simple tips to help you get more value from your risk register:
- Regular updates: Risks change over time. Update your risk register regularly to track new risks and see how your mitigation strategies perform. Tools like Isora GRC make it easy to get real-time risk updates.
- Use a standard format: Consistency helps. Make sure all teams use the same format for risk descriptions, categories, and scoring. This simplifies communication and reporting. A centralized risk-tracking system can help keep things uniform.
- Monitor risks continuously: Continuous risk monitoring is key to staying ahead. Regular updates help you stay aware of shifting risks and vulnerabilities, ensuring quick action.
- Make data-driven decisions: Use your risk register data to guide decisions. By combining likelihood and impact to prioritize risks, you can focus on the most important risks first, helping protect your business better.
- Work together across teams: Cybersecurity risk management involves everyone. Collaboration between departments helps improve how you manage and respond to risks. With Isora GRC, you can easily assign risk owners, track updates across teams, and grow a strong information security culture.
- Use visual tools for clarity: Risk matrices and dashboards help you see priorities quickly. These visual tools make it easier to understand complex risks and take action when needed.
- Engage stakeholders: Keep leaders and key stakeholders informed with easy-to-read reports from your risk register. Regular communication ensures that your risk management aligns with the organization’s goals.
By following these tips, you can improve how you manage cybersecurity risks and protect your organization. Whether using manual methods or software like Isora GRC, a regularly updated and well-maintained IT risk register helps you stay prepared and reduce potential damage from risks.
IT Security Risk Register FAQs
What is the IT security risk management process?
IT security risk management involves identifying threats and vulnerabilities, assessing their likelihood and impact, planning risk responses, and monitoring risk over time. This process includes risk identification, assessment, mitigation, and continuous tracking.
A GRC Assessment Platform™ like Isora GRC helps streamline this by providing structured workflows, real-time risk updates, and support for risk-based decision making.
What is a risk register in information security?
A risk register in information security is a centralized system for tracking identified risks, including their descriptions, likelihood, impact, owners, and response plans. It helps teams prioritize and manage risk over time.
Isora GRC supports this process with structured templates, ownership tracking, and real-time updates.
How do I create an IT risk register template?
Start by aligning with a risk assessment framework such as NIST SP 800-30, then structure your risk register using guidance from NIST IR 8286.
A good risk register template includes columns for risk ID, description, likelihood, impact, response strategy, owner, and mitigation status. Some teams expand it to include threat likelihood, risk aggregation, or links to specific security controls.
Who is responsible for managing risks in the register?
Each risk in the register should be assigned a risk owner—typically the individual or team responsible for the affected asset or process. Risk owner assignment ensures accountability throughout the risk management process, from mitigation planning to continuous risk monitoring and real-time updates.
How does a risk register support cybersecurity risk management?
An effective cybersecurity risk register turns assessments into action. It enables operational risk management by making risks visible, trackable, and owned. It also supports strategic risk management by linking individual IT risks to enterprise goals and supporting enterprise risk management (ERM) reporting.
What is the difference between a risk register and a risk assessment?
A risk assessment identifies and evaluates potential threats and vulnerabilities, using factors like threat likelihood and impact assessment. A risk register documents and tracks those risks after they’ve been assessed, serving as a living record of decisions, ownership, mitigation status, and prioritization.
How often should an IT risk register be updated?
Risk registers should be reviewed and updated regularly, at least quarterly or in alignment with major assessments or control testing cycles. Continuous risk monitoring and real-time updates help ensure the register reflects current conditions and supports a timely response.
How does a risk register support compliance?
Many security control frameworks and regulations expect organizations to document and manage risks. A compliance risk register demonstrates that risks have been identified, prioritized, and linked to security risk documentation, controls, and remediation plans.
Can I use the same register for third-party and internal risks?
Yes. A unified risk register can include both internal and third-party risks as long as each entry clearly identifies the affected asset, owner, and risk source. Risk categorization helps distinguish between internal control failures, vendor-related risks, and broader business risks.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.



















 Other Relevant Content
Other Relevant Content