Table of Contents
Table of Contents
- What is a Bank IT Security Risk Assessment?
- Why are IT Security Risk Assessments Important in the Financial Sector?
- Regulatory Compliance and Bank IT Security Risk Assessments
- How Do Financial Institutions Assess IT Security Risks?
- How to Conduct a Bank IT Risk Assessment
- Simplify IT Security Risk Assessments with Isora GRC

Banks have used IT security risk assessments to protect customer data for decades. But today’s assessments tend to look much different, and they matter more than ever.
Modern banks rely on technology for almost everything: transactions, customer data, and daily operations. But the more they depend on IT systems, the more vulnerable they become to cyber threats like data breaches. That’s why financial regulators require IT security risk assessments. But it’s also why assessments are important for managing real-world risk.
Because even though all banks regularly conduct risk assessments, their processes often have problems. For example, many banks still use email surveys and spreadsheets to collect risk data. While familiar, these manual methods can also cause inconsistent answers and lost details. Here, teams waste time chasing down information instead of fixing actual security issues. Over time, risk data becomes less reliable and decisions become less informed.
Banks need a simpler way to manage IT security risk assessments. That means using clear templates for every team, tracking exactly who’s responsible for fixing each issue, and storing all assessment data in a single, organized place. With a more structured approach, institutions can get more trustworthy data about risks, and banking leaders can get more clarity on the issues that matter most and why.
This guide explains how banks can conduct IT security risk assessments in a risk-informed and regulator-friendly way. It follows the NIST SP 800-30 framework, a structured process widely accepted by financial regulators. It lays out how to identify risks, rank their importance, and create actionable plans to fix them. Whether your bank wants to improve an existing process or develop a new approach, this guide explains what steps to take.
Note: Terms like “information security,” “cybersecurity,” and “IT security” show up in this guide a lot. We often use them to mean the same thing because they pretty much do. They all refer to the policies, systems and teams that protect technology and sensitive data.
What is a Bank IT Security Risk Assessment?
A bank IT security risk assessment is a structured process financial institutions use to find and evaluate weaknesses across their technology systems. The goal is risk-informed decision-making. They help banks prioritize where and how to respond based on clear data about threats and their potential impacts.
Every assessment answers three key questions:
- What could go wrong?
- How likely is it?
- What would happen if it did?
Banks have been conducting IT risk assessments for decades. After the Bank Service Company Act (BSCA) of 1962 made computerized accounting widely available to banks, concerns about data security spread with them. By 1970, the Federal Deposit Insurance Corporation (FDIC) introduced formal Electronic Data Processing (EDP) exams. These assessments would lay the groundwork for the processes banks still use today.
Modern bank IT risk assessments cover everything from online banking platforms and payment networks to cloud services and third-party vendors. They look at technical safeguards (like encryption and firewall settings) and other common issues like overly broad system access, slow software updates, or unclear accountability.
Done well, information security risk assessments help banks clearly identify what’s secure, what’s vulnerable, and where the biggest risks lie. They also help security teams prioritize urgent fixes and help leaders make informed decisions about resource allocation, regulatory compliance, and customer protection.
Next, we’ll explore why IT security risk assessments are particularly important for financial institutions.
What is an IT Security Risk Assessment?
Information security risk assessments measure how organizations use, manage, and protect their information technology (IT) systems from risk.
Read our complete guide on conducting an IT security risk assessment.
Why are IT Security Risk Assessments Important in the Financial Sector?
Financial institutions have always faced security risks. Managing money makes banks constant victims of crime. The earliest attacks were often physical and often involved direct theft (think cowboy robbers of the wild west). Banking evolved with the industrial revolution, of course. But the rise of digital banking was by far the most dramatic recent change to the threat landscape.
The first successful cyberattack on the U.S. financial sector was in 1994. When corporate customers at Citibank discovered $400,000 missing from their accounts, the FBI investigated what it calls “the first online bank robbery.” Even though the attack didn’t involve today’s internet, it did mark the beginning of a new era. For many in the industry, this attack made digital vulnerabilities very real.
Digital banking was by far the most dramatic change to the threat landscape.
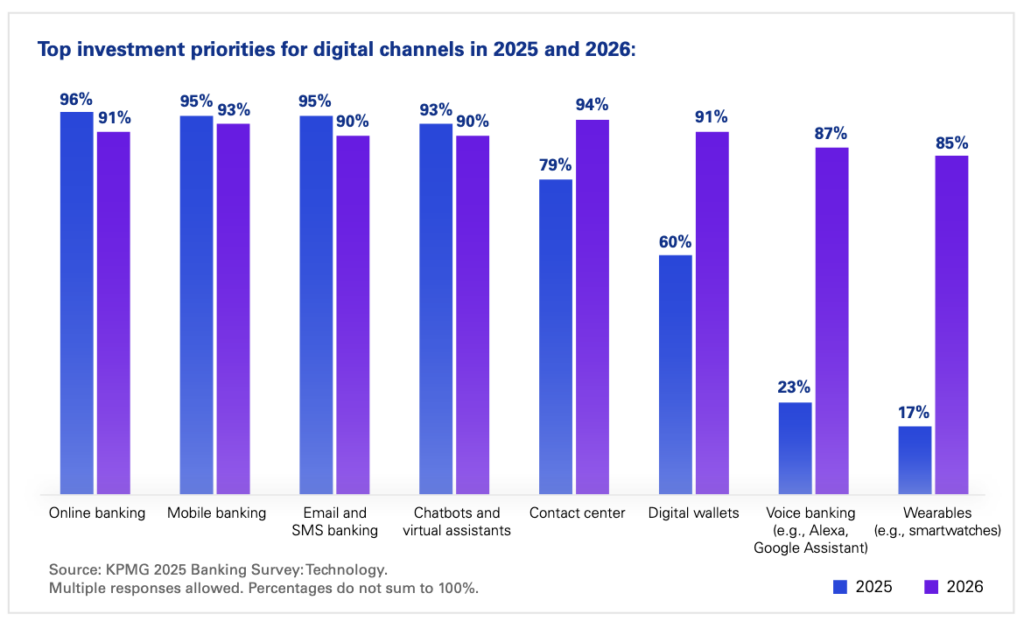
Now, modern banking is almost entirely digital. Most money exists purely as data, and consumers expect 24/7 access. In fact, online banking is now the primary feature customers seek when choosing a bank (57%), followed by mobile apps (54%). And many banks are listening. Most banks say online and mobile banking are top priorities for them, too. Many even plan to explore the future of banking (like voice banking and wearables) in 2026.
But convenience also comes with risk. Every new digital service, mobile app, or outside vendor grows a bank’s digital footprint. Each connection adds another door attackers could open. Banks now operate technology ecosystems that often grow faster than security teams can keep up.
Artificial intelligence and autonomous systems are ready to transform the sector again, making things even more complicated. Automated attacks can spread quickly, turning small mistakes into big problems. Old ways of doing security assessments (like emailing surveys or using spreadsheets) can’t keep up anymore. Modern banks need an easier way to manage cybersecurity risk assessments, spot their security gaps quickly, and focus resources where it matters most.
IT security risk assessments help banks do exactly that. Good assessments clearly show what’s broken, how serious it is, and exactly who should fix it. They turn technical problems into clear, practical decisions, so:
- Business leaders easily see where they need to invest.
- Security teams spend less time sorting through paperwork and more time solving problems.
- Compliance teams get clear proof to show regulators.
Before examining common challenges, let’s look more closely at how banks benefit from well-executed IT security risk assessments.
Benefits of Cybersecurity Risk Assessments for Banks
IT security risk assessments help banks identify vulnerabilities, evaluate their severity, and determine the impacts. But cyber risk assessments are more than reports. They’re clear action plans banks can actually use to improve security.
Information security risk assessments can help banks with:
- Clarity: Risk assessments clearly highlight vulnerabilities, helping institutions understand exactly where they’re exposed and what the impacts could be.
- Prioritization: By evaluating risks consistently, banks can effectively direct resources to their most critical vulnerabilities first.
- Accountability: Documented risks ensure visibility, making it more likely that issues get addressed promptly.
- Coordination: Assessments unify security, IT, compliance, and business teams around a shared understanding of risks and responses.
- Preparedness: Clearly defined risks enable quicker, more effective responses when security incidents occur.
Next, let’s examine the common challenges banks face when conducting assessments.
Challenges and Risks in Banking IT Risk Management
The core components of risk assessments (collecting information, verifying controls, and assigning ownership) haven’t changed, but the environment around them has evolved significantly. Threats are more sophisticated, IT environments more decentralized, and regulatory oversight more rigorous.
Risk now extends beyond internal networks, reaching into cloud services, third-party partnerships, and distributed teams. Processes that once involved clearly defined checks now require greater coordination, deeper technical expertise, and real-time awareness, and traditional risk assessment methods often struggle to keep pace. Without updating how assessments are structured and integrated with overall governance, banks risk missing critical insights, even if individual items on their assessment appear complete.
Here are the top challenges shaping how financial institutions manage IT risk in 2025.
Cyber threats and vulnerabilities
Financial institutions face more cyber threats and vulnerabilities than ever today. Since 2020, financial services has been second only to healthcare in the number of data violation cases due to cyberattacks in the U.S. As banks become more connected, these cybersecurity risks will only become more persistent, more expensive, and more difficult to manage.
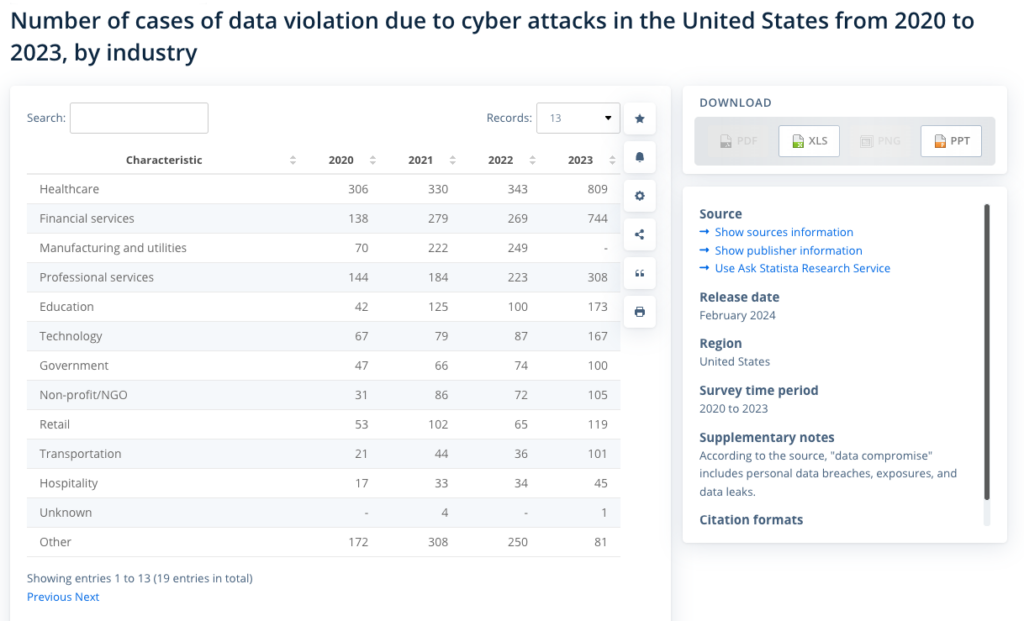
(Source: Statista)
Many cyber risks grow significantly year over year. According to the 2025 Verizon Data Breach Investigations Report, there was a 34% increase in attackers exploiting vulnerabilities to gain initial access and cause security breaches compared to 2024’s report. With bank managers ranking cybersecurity as the top near-term risk, it seems most banks are at least aware of the problem. And according to most banks, they’re on top of it, with 91% saying they invest enough in cybersecurity. Less comforting is the fact that only 78% feel prepared to protect customer data, privacy, and assets in the event of an actual attack.

(Source: KPMG 2025 Banking Survey: Technology)
Unfortunately, threats like ransomware, credential theft, and software exploits are no longer isolated events at modern financial institutions. They often emerge through routine systems and spread through overlooked dependencies instead. When the Federal Reserve Bank of New York modeled the effects of a cyberattack on the U.S. financial system in 2020, the results were disturbing: a compromise at just one of the five largest U.S. banks could negatively impact nearly 40 percent of the financial network.
The warning from financial regulators is clear: the risk conditions are rising. Now, what counted as secure a year ago may no longer be enough. Next on the horizon? The Federal Reserve says AI-facilitated cybercrime and deepfakes.
Insider risks and misconfigurations
External threats like hackers might get more attention, but internal missteps are still a leading cause of security incidents. Sixty-percent of breaches involved human error in 2024, says Verizon, a figure that includes everything from like misconfigurations, unclear ownership, and routine decisions made without full visibility.
However, most of these issues aren’t the result of malicious intent. More often, they show up as small process failures that slip through the cracks. These risks can be especially challenging to manage because they’re often embedded in routine workflows. A disabled MFA setting, a policy that hasn’t been updated, a shared password left in place for convenience – none of these raise alarms on their own. Instead, each one slowly introduces exposures that are hard to detect and even harder to trace.
Risk assessments are one of the best opportunities for banks to catch these problems before they spiral out of control. Above all, they can help surface the quiet risks that perimeter defenses tend to miss. But they can also help clarify ownership. That way, when something isn’t working, it’s immediately clear who needs to fix it and when.
Third-party and cloud ecosystem risks
Most banks now operate within a layered network of cloud platforms, fintech partners, service providers, and managed vendors. Each relationship grows the institution’s operational footprint, but it also introduces risk. And, as these systems becomes more interconnected, the consequences of a single weak link are often harder to contain.
Today, a misconfigured S3 bucked, a compromised API, or an unpatched dependency buried in vendor code can have immediate and widespread impacts. The Log4Shell vulnerability first made that clear in 2021 when it exposed just how deeply risk can spread beyond the systems an institution directly manages. For many, the infamous CrowdStrike outage of 2024 will go down in history as the ultimate example of just how widespread this type of IT outage can be.
According to the 2025 Verizon report, third-party involvement in breaches doubled last year from 15% to 30%. This figure includes technical compromises and failures in monitoring, change control, and escalation that left organizations exposed. Overall, the trend reflects a broader shift toward shared infrastructure, shared responsibilities, and shared consequences – one which regulators have taken note.
The FFIEC’s recent guidance on cloud risk, for instance, urges institutions to evaluate vendor controls, define contractual obligations for security and availability, and maintain continuity plans that account for provider failure. The U.S. Treasury has raised similar concerns, pointing to concentration risk, resilience gaps, and the need for stronger oversight as cloud adoption accelerates across the sector.
For risk assessments to be effective in this environment, they must account for external dependencies as thoroughly as internal ones. That means identifying how vendors access data, what controls they’re responsible for, and how those controls are tested. It also means knowing what happens when those controls fail and whether your institution is prepared to respond.
What is Third Party Risk Management (TPRM)?
Third-party risk management is the process of finding, assessing, fixing, and monitoring third-party risks introduced by suppliers, vendors, service providers, and contractors.
Check out our TPRM guide to learn more.
Resource and alignment gaps
The depth and breadth of participation across an organization often determines a risk assessment’s success rate. Controls don’t live in one department at most organizations, and neither does risk. But getting the right input at the right time is a constant challenge, especially when capacity is thin.
Most banks and especially smaller ones struggle to dedicate enough staff time or expertise to do the work well. According to the World Economic Forum Global Cybersecurity Outlook 2023 report, just 14% of banking business leaders felt confident about talent.
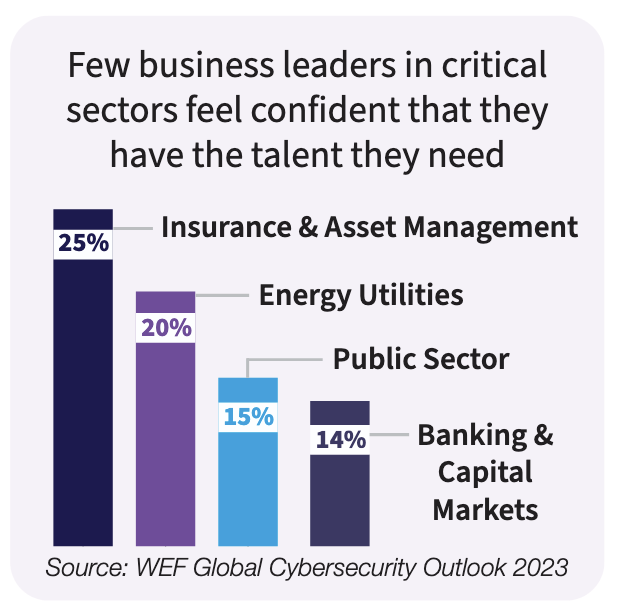
(Source: National Institute of Standards and Technology [NIST])
Larger institutions also cite persistent gaps in alignment between security teams, business units, and IT. This often shows up as ‘assessment fatigue’, in questionnaires that feel disconnected from day-to-day work, requests that go unanswered, and results that are difficult to interpret or act on.
For institutions making progress in this area, the shift tends to be cultural as much as procedural. Here, risk is something that’s understood across teams as part of how the organization operates, makes decisions, and stays accountable. That shift might be gradual, but it’s essential. Because without it, even the best frameworks can fall flat.
Next, let’s take a closer look at the one risk that didn’t make this risk: regulatory compliance.
Regulatory Compliance and Bank IT Security Risk Assessments
Most banks already understand that cybersecurity oversight doesn’t come from a single authority. It comes from many – federal and state regulators, examiners, enforcement bodies – each with their own priorities, timelines, and documentation requirements. Today, navigating that complexity has become one of the defining challenges of modern risk management.
Nearly every regulation starts with the shared expectation that every financial institution must have a formal information security program grounded in risk. But what “good” looks like often depends on who’s asking. Because even if the standards overlap, they don’t always align.
First, let’s take a closer look at that shared regulatory foundation. Then, we’ll explain how individual regulators interpret, extend, or enforce it.
The GLBA & the FFIEC IT Examination Handbook
The Gramm-Leach-Bliley Act (GLBA) is the starting point for cybersecurity oversight for most U.S. financial institutions. Under the GLBA’s Safeguards Rule, banks and credit unions must implement an information security program that fits their size, complexity, and risk profile. GLBA requirements include regular risk assessments, written policies, technical controls, and limits on who can access sensitive data and systems.
The Federal Financial Institutions Examination Council (FFIEC) was established by Congress in 1979 to bring consistency to the way federal regulators oversee financial institutions. Its members include the FDIC, OCC, FRB, NCUA, and CFPB, as well as a liaison committee that represents state regulators. But the council does not regulate directly. Instead, it publishes handbooks and statements that member agencies use to guide their examinations.
So, when financial institutions say they are “FFIEC compliant,” what they really mean is that their programs align with the council’s IT Examination Handbook. While not a regulation itself, it is the most commonly referenced guide across federal agencies.
The FFIEC IT Examination Handbook covers every aspect of information security risk management, from governance and staffing to technical controls and vendor oversight. It outlines what examiners look for during reviews: how risk is identified, how controls are selected and tested, how third-party relationships are managed, and how institutions plan for disruption and recovery. For most institutions, it servers as a framework and a roadmap.
But that shared foundation doesn’t mean all examiners interpret it the same way. For instance:
- The FDIC expects evidence that institutions are actively monitoring cyber threats and preparing for potential incidents.
- The OCC puts greater emphasis on operational resilience.
- The NCUA requires cyber incident reporting within 72 hours.
- NYDFS requiring annual certifications, detailed governance documentation, and mandatory incident reporting for institutions operating in the state of NY.
For institutions regulated by more than one agency or operating across jurisdictions, the greatest challenge is mapping risk assessments to multiple frameworks without duplicating effort or losing clarity. But that doesn’t mean less rigor is acceptable. If anything, it raises the stakes for internal consistency.
Next, let’s take a closer look at who exactly regulates what.
Want more on GLBA? Check out our complete GLBA guide for financial institutions and our GLBA Safeguards Rule risk assessment guide for 2025.
Who Regulates What in Banking?
The FFIEC handbook might provide the shared point of reference, but each regulator approaches cybersecurity through a slightly different lens. Priorities differ and reporting timelines vary. How they evaluate assessments can even change depending on which risks they focus. For many banks, understanding who regulates what and how can help clarify where alignment is possible and extra interpretation is required.
Here’s how major federal and state regulators approach information security, and what they expect from the assessment process in particular.
FFIEC IT Examination Handbook
The FFIEC doesn’t regulate directly, but does provide the structural backbone for most federal cybersecurity oversight. Its IT Examination Handbook (Information Security Booklet) outlines examiner expectations across governance, technical controls, risk assessments, and response planning. Because it’s framework-neutral, institutions can use NIST, ISO, or other models as long as their programs are well-documented, risk-informed, and maintained over time.
FDIC: Appendix B to Part 364
The Federal Deposit Insurance Corporation (FDIC) expects insured institutions to actively monitor cyber threats and maintain programs that address their specific risk profile. Appendix B to Part 364 points directly to the FFIEC Cybersecurity Resource Guide for establishing security controls and incident response capabilities. Under this requirement, institutions are expected to demonstrate the presence of controls, the ability to respond to failures, and the agility to adapt to new threats.
FRB: Interagency Guidelines
The Federal Reserve Board (FRB) reinforces the need for measurable cybersecurity maturity. The FRB’s Interagency Guidelines include policies for third-party oversight, regular vulnerability scans (including mobile platforms), and annual testing of incident response plans. Institutions supervised by the Fed are also expected to track the effectiveness of their controls over time, not just report that they exist.
OCC: 12 CFR Part 30
The Office of the Comptroller of the Currency (OCC) aligns closely with FFIEC standards, but 12 CFR Part 30 puts more focus on internal controls, vendor risk management, and operational resilience. More recent guidance also emphasizes scenario-based testing and control validation to make sure what’s written in policy is being applied in practice.
NCUA: 12 CFR Part 748
The National Credit Union Administration (NCUA) requires federally insured credit unions to report cyber incidents within 72 hours of reasonable belief that one has occurred. Backed by guidance grounded in FFIEC principles, 12 CFR Part 748 encourages institutions to report quickly using secure channels to protect sensitive information.
CFPB: Section 1033 Rule
The Consumer Financial Protection Bureau (CFPB) focuses more on data access and consumer protection. Under Section 1033, institutions must implement and test access controls, monitor for unauthorized data use, and make sure services remain available to customers. For banks offering open banking or API-based services, these requirements also have direct implications for risk assessment scope.
FTC: GLBA Safeguards Rule
The Federal Trade Commission (FTC) enforces the GLBA Safeguards Rule for non-bank financial institutions. The rule requires these institutions to develop, implement, and maintain an information security program that includes regular risk assessments, employee training, access control, and oversight of service providers. Though intended for a different segment, the rule’s core requirements often mirror those in banking compliance.
NYDFS: 23 NYCRR 500
The New York Department of Financial Services (NYDFS) maintains one of the most detailed cybersecurity regulations in the U.S. financial sector. Under 23 NYCRR 500, a broad range of entities – including state-chartered banks and certain national institutions operating in New York – must certify compliance annually, conduct formal risk assessments, maintain defined governance structures, and report qualifying cyber incidents within 72 hours.
FINRA
The Financial Industry Regulatory Authority (FINRA) evaluates cybersecurity as part of broader technology governance. While not prescriptive, FINRA expects that firms have a repeatable risk assessment process in place and that findings lead to tangible improvement. Its reviews typically focus on access control, insider threat mitigation, data loss prevention, and documented incident response planning.
SEC: 2023 Cyber Disclosure Rules
The Securities and Exchange Commission (SEC) requires publicly traded companies to disclose material cybersecurity incidents within four business days of determining materiality. Under the 2023 Cyber Disclosure Rules, annual filings must include detailed information about cyber risk governance, board oversight, and risk management processes. Institutions must maintain accurate, up-to-date assessments that support external transparency as well as internal planning to meet these requirements.
How Do Financial Institutions Assess IT Security Risks?
IT security risk assessments help banks and credit unions understand where they’re most exposed and decide what to do about it. The process involves evaluating systems, processes, and third-party dependencies to identify where failure is most likely, how severe the impact could be, and whether existing protections are working as intended.
Both internal and external factors shape how institutions approach this work. Assessments must support real decisions, but also meet regulatory expectations and stand up to audit. Here, structure matters – a well-scoped, repeatable process allows teams to produce consistent results across business units and demonstrate control over how risk is managed and monitored.
To meet these expectations, many institutions follow established frameworks. When used well, these frameworks help clarify scope, reduce duplication, and connect assessment results to strategy, remediation, and compliance.
Here are some of the most common IT security risk assessment frameworks for banks today.
IT Security Risk Assessment Frameworks for Banks
Banks and credit unions can use several frameworks to guide their IT security risk assessments. While some are designed specifically for financial institutions, others are broader but more widely accepted by regulators. Each offers a different way to organize, measure, and improve cybersecurity risk management.
FFIEC CAT
Introduced in 2015, the FFIEC Cybersecurity Assessment Tool (CAT) is a voluntary framework designed to help financial institutions measure cybersecurity maturity and align with supervisory expectations. The tool includes five domains and a structured set of declarative statements designed to map directly to examiner criteria.
For years, the CAT gave institutions a familiar format for annual assessments and reporting. Its structure aligned well with board-level oversight, and its terminology made it easy to show alignment with FFIEC guidance. But over time, the tool fell behind. It proved difficult to tailor, rarely updated, and increasingly out of touch with risks tied to cloud architecture, third-party code, and digital operations.
In 2024, the FFIEC announced plans to retire the CAT by August 2025. The council now encourages institutions to adopt more adaptable frameworks that better support evolving risk environments and more complex system landscapes.
NIST CSF
The National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) is a widely accepted foundation for risk assessments across industries today. First released in 2014 and most recently updated in 2024, the CSF organizes cybersecurity into five core functions (Identify, Protect, Detect, Respond, and Recover), each supported by categories that help structure analysis and guide planning.
This framework’s strength lies in its flexibility. Institutions can tailor NIST CSF assessments to fit their systems, maturity level, and regulatory footprint. Today, many banks use CSF to evaluate areas ranging from core banking platforms to vendor ecosystems, and often combine it with detailed control libraries like NIST SP 800-53, ISO 27001, or CIS Controls.
That same flexibility, however, also means CSF isn’t prescriptive – it provides a structure for thinking about cybersecurity but leaves implementation details up to the institution. Banks that rely on it typically pair it with additional frameworks or use it as the backbone of an internally developed methodology. Many also map it to regulatory requirements to make sure their assessments meet examiner expectations.
CRI Profile
Developed by the financial sector and maintained by the Cyber Risk Institute (CRI), the Financial Services Cybersecurity Profile builds on the NIST CSF by tailoring it to the operational and regulatory realities of banks and credit unions. The CRI Profile integrates over 300 diagnostic statements that align with expectations from the FFIEC, GLBA, NYDFS, and global regulators so it’s easier for banks to perform one assessment that meets multiple compliance obligations at once.
The CRI Profile also adds specificity where banks often need it most. It offers more detailed guidance on vendor risk, cloud governance, and board-level oversight: areas where examiners tend to focus and institutions often lack clarity. Its structure mirrors the CSF’s five functions but layers in control depth and diagnostic rigor to support scale and structure.
As the FFIEC sunsets the CAT, regulators increasingly recognize the CRI Profile as a preferred alternative. Smaller institutions can use streamlined versions focused on essential controls, while larger banks apply the full model across teams and business lines to assess maturity and track improvement over time. Many institutions are already adopting it to consolidate risk, compliance, and maturity assessments into one process that uses a common language with examiners.
The Risk Assessment Process at Financial Institutions
Risk assessments are how banks and credit unions decide where to focus their security efforts. They create structure around complex decisions, turning a long list of assets, vendors, and obligations into a clearer understanding of what’s at stake and what to do next.
NIST SP 800-30 and the Financial Sector
Some institutions use NIST SP 800-30 as the foundation for their security risk management process. Originally developed for federal agencies, the framework has become a trusted reference across industries because of its clarity and adaptability. Instead of prescribing specific technologies or controls, it outlines a method for evaluating risk that institutions can tailor to fit their systems, governance structure, and risk appetite.
NIST SP 800-30 organizes the risk assessment process into four key phases:
- Prepare: Define the purpose and scope of the assessment, identify stakeholders, and select an approach for gathering and evaluating information. This step helps focus the effort and ensure it reflects institutional priorities.
- Conduct: Identify systems and data, map potential threats and vulnerabilities, evaluate existing controls, and assess the likelihood and impact of different failure scenarios. This is the core of the analysis.
- Communicate: Summarize the findings, document how risk was evaluated, and share results with stakeholders. Reports typically include risk ratings, recommended actions, and areas where follow-up is required.
- Maintain: Revisit and update the assessment regularly. That includes reviewing assumptions, refreshing data, and adjusting for changes in infrastructure, policy, staffing, or the broader threat environment.
For banks and credit unions, this process helps satisfy a range of regulatory expectations (like GLBA). By offering a shared method for evaluating risk across teams with different priorities and technical knowledge, it can support internal alignment, too.
Most institutions pair NIST SP 800-30 with other frameworks to meet specific requirements or add detail. Banks can map results to the FFIEC Handbook, NIST CSF, or the CRI Profile for full coverage during exams and internal audits, or embed the process into broader enterprise risk programs to support board-level reporting.
How to Conduct a Bank IT Risk Assessment
The basic structure of a risk assessment might be similar across industries, but the stakes are higher and the oversight stricter in banking. To stay on track, many institutions use the NIST SP 800-30 framework as a guide, adapting it to reflect their specific internal workflows, regulatory mappings, and resource constraints.
So, that’s exactly what we’ll do next.
What is NIST SP 800-30?
NIST Special Publication 800-30 is one of the most widely used risk management frameworks for information security risk assessments today.
Check out our thorough, step-by-step guide to conducting an IT security risk assessment with NIST SP 800-30.
Cybersecurity Risk Assessment Checklist for Banks
Use this checklist to structure a defensible, regulator-ready IT security risk assessment based on NIST SP 800-30 and tailored to the realities of banks.
Note: For a more detailed, step-by-step walkthrough of each phase, see our comprehensive guide to conducting an IT security risk assessment.
Prepare
Set the foundation by defining the purpose, scope, and roles before the work begins.
- Define the objective. Clarify whether the assessment supports a GLBA audit, FFIEC exam, vendor review, or internal planning.
- Set the scope. Identify which systems, business units, or third parties are in focus.
- Assign roles. Designate assessment leads, subject matter experts, approvers, and coordinators.
- Develop questionnaires. Align questions to your selected framework (e.g., NIST CSF, FFIEC Handbook, CRI Profile) and specify what counts as sufficient evidence.
- Communicate expectations. Share the timeline, responsibilities, and purpose with all participants before launch.
Collect Responses & Evidence
Distribute questions, gather documentation, and confirm how controls are implemented.
- Distribute tailored questionnaires. Match questions to each team’s systems and responsibilities to avoid one-size-fits-all.
- Request supporting evidence. Ask for documentation that shows how each control is implemented and managed.
- Follow up as needed. Clarify vague responses, resolve inconsistencies, and confirm control operation with SMEs.
Analyze the Findings
Review responses to identify gaps in documentation, implementation, or consistency.
- Review responses by control area. Look for missing evidence, inconsistent practices, or policy-to-practice drift.
- Document control gaps. Record what’s missing, which system or team it affects, and why it matters.
Score and Categorize Risks
Evaluate each gap by likelihood and impact, and record results in a central risk register.
- Estimate likelihood and impact. Use a consistent scoring model that reflects both business and regulatory risk.
- Prioritize based on exposure. Focus on issues involving sensitive systems, recurring gaps, or compliance dependencies.
- Record risks in a central register. Include scores, ownership, system metadata, and mapped control references.
Assign Ownership & Plan Remediation
Make sure every risk has a defined owner and a clear remediation path.
- Assign a responsible owner. Make sure every risk has someone accountable for follow-through.
- Define the remediation plan. Include next steps, current status, due dates, and blockers.
- Track remediation centrally. Use a single system to monitor updates across teams.
Report the Results
Deliver findings in a way that supports decision-making and regulatory review.
- Tailor reports to stakeholders. Provide executives with summaries, control owners with actions, and auditors with evidence.
- Use structured formats. Risk dashboards, annotated registers, and mapped reports help translate findings into decisions.
- Keep reporting consistent. Align outputs with board and examiner expectations.
Maintain the Process
Revisit the assessment regularly to reflect changes and track progress.
- Update assessments regularly. Trigger reviews based on system changes, vendor shifts, or incidents.
- Re-score and reassign as needed. Refresh findings to reflect your current environment.
- Track long-term progress. Keep the risk register current, revisit open items, and treat assessment as ongoing work.
Information Security Risk Assessment Best Practices for Banks
IT security risk assessment best practices are evolving in response to growing complexity, shifting regulatory expectations, and internal demands for better visibility. As risk programs mature, leaders are looking for ways to make assessments more useful across the institution during planning, remediation, audit time, and board reporting.
The best programs tend to share a few key traits. They link assessment results to governance. They track and update risk between formal review cycles. They include operational realities like response and recovery, not just preventive controls. And they use tools that help standardize how assessments are conducted, scored, and maintained over time.
Here’s a closer look at some of the IT security risk assessment best practices for banks.
Connect Maturity Frameworks to Governance
Many banks have adopted maturity models like NIST CSF or the CRI Profile to evaluate cybersecurity posture. But the value of those assessments often gets lost when results stay isolated within security teams. The most effective programs use maturity data to support broader risk governance. This helps institutions move from assessment as documentation to assessment as input for strategic planning.
How to connect frameworks to governance:
- Map results to board-level metrics and reporting cycles.
- Use one process to satisfy multiple regulatory frameworks.
- Assign accountability for specific maturity targets across teams.
Track Key Risk Indicators in Real Time
Annual assessments can establish a baseline, but they rarely reflect what happens between cycles. Teams that treat risk as static can miss meaningful changes in posture, often only discovering issues when audit deadlines approach. Adding lightweight, ongoing monitoring helps maintain a current view of risk and makes the formal assessment more accurate and relevant.
How to track KRIs in real time:
- Track indicators like patch status, access controls, or vendor service levels.
- Use monitoring results to update assessments or prompt follow-up reviews.
- Align monitoring to existing controls to reduce overhead.
Make Risk Assessment Results Visible to Leadership
Risk assessments often contain useful data, but that value gets diluted when findings don’t reach decision-makers. Bringing assessments into management conversations reinforces accountability and helps align risk mitigation efforts with institutional priorities. Teams may be addressing issues, but if leadership can’t see progress or exposure, those efforts are harder to prioritize and fund.
How to make risk more visible to leaders:
- Share summaries of key risks and open issues with executives and boards.
- Link assessment results to risk appetite statements or investment plans.
- Include assessment metrics in regular reporting alongside operational and financial indicators.
Include Response and Recovery in Scope
Most assessments focus on preventive controls, which are important but not sufficient. But a complete view of security risk also requires evaluating how well the institution can detect, respond to, and recover from disruption. Including these elements helps demonstrate operational resilience and aligns with regulatory guidance on recovery and continuity planning.
How to put response and recovery in scope:
- Review incident response plans, recovery time objectives, and testing frequency.
- Include results from simulations or tabletop exercises in the assessment.
- Add any identified response gaps to the risk register for tracking.
Use GRC Tools to Standardize and Scale
Manual assessments tend to be slow, inconsistent, and difficult to repeat. As risk programs grow, many institutions are adopting GRC tools to reduce friction, improve traceability, and simplify coordination across teams. Integrated platforms also help maintain a clear system of record, making it easier to revisit, update, and reuse assessment data over time.
How to use GRC tools:
- Automate data collection, scoring, and report generation.
- Standardize assessment templates and workflows across business units.
- Link findings to frameworks like FFIEC, NIST, or CRI to support audits and reviews.
Simplify IT Security Risk Assessments with Isora GRC
IT security risk assessments are becoming harder to manage with spreadsheets and scattered inputs alone. The scope is broader, expectations are higher, and the need for consistency is greater than ever. For many institutions, the challenge isn’t whether assessments are happening—it’s whether the process produces results that support decisions, satisfy auditors, and scale across teams.
Isora GRC gives banks and credit unions a structured way to manage IT security risk assessments. It supports the full process from data collection to reporting, using a framework-aligned approach that meets internal needs and regulatory expectations.
Institutions can use Isora to conduct assessments based on NIST SP 800-30 and align them with FFIEC guidance, GLBA requirements, and other common frameworks. It also offers customizable questionnaires, centralized risk tracking, and audit-ready reports with mapped controls and attached evidence.
In Isora, assessment results are recorded in a centralized risk register. Each entry includes scoring, assigned ownership, remediation plans, and due dates. Here, teams can automate recurring workflows, standardize how risks are scored, and reduce the time spent chasing inputs across departments.
- Examiners can use Isora outputs to review how institutions identify and manage risk.
- Leadership can use the platform to understand what risks exist and how they are being addressed.
- Security and compliance teams can use it to reduce administrative effort and focus on resolving issues fast.
For banks that want a more consistent, transparent, and repeatable way to manage IT risk assessments, Isora can help you keep pace – without rebuilding your program from scratch.
Check out the interactive demo of assessment management in Isora GRC below — or request a personalized demo.
Bank IT Security Risk Assessments FAQs
Why are IT security risk assessments important for banks?
IT security risk assessments help banks understand where they’re most vulnerable to cyber threats, system failures, or internal control breakdowns. They are a regulatory expectation and a practical tool for identifying high-risk areas, prioritizing remediation, and protecting customer data, financial systems, and operational continuity.
What are the benefits of IT security risk assessments for banks?
Risk assessments give banks a structured way to evaluate cybersecurity posture, track improvements over time, and meet compliance requirements. They help prioritize security investments, uncover gaps before regulators or attackers do, and build trust with internal stakeholders, auditors, and customers.
How do you do risk assessments at banks?
Most banks follow a structured process based on NIST SP 800-30. The steps include defining scope and purpose, collecting data through questionnaires or interviews, evaluating existing controls, identifying risks, scoring their likelihood and impact, and tracking remediation through a centralized risk register. Results are shared with leadership and used to support audits, regulatory exams, and security planning.
What are the key elements of an IT security risk assessment for banks?
The key elements of a bank IT security risk assessment include a clear scope, stakeholder involvement, control evaluation, evidence collection, risk scoring, a centralized risk register, and actionable reporting. These components help banks identify threats, assess vulnerabilities, and prioritize remediation in alignment with regulatory expectations and business needs.
How often should banks conduct IT security risk assessments?
Banks should conduct IT security risk assessments at least annually, or more frequently in response to system changes, vendor onboarding, regulatory updates, or emerging threats. Many institutions now supplement annual reviews with continuous monitoring or quarterly check-ins to maintain current risk visibility and support agile decision-making.
How can banks improve their IT security risk assessment processes?
Banks can improve risk assessments by using standardized frameworks, automating data collection and scoring, maintaining a centralized risk register, and aligning results with business goals. Clear ownership, consistent methodology, and regular updates help turn assessments into reliable tools for prioritization, compliance, and strategic planning.
What is the NIST SP 800-30 guidance for banks?
NIST SP 800-30 outlines a four-phase process for assessing information security risk: prepare, conduct, communicate, and maintain. It helps banks identify threats, evaluate controls, and prioritize risk response based on likelihood and impact. The framework supports GLBA, FFIEC, and other financial regulatory requirements.
How can banks simplify the risk assessment process?
Banks can simplify risk assessments by automating workflows, standardizing questionnaires, and using GRC tools to manage scoring, reporting, and remediation tracking. Platforms like Isora make it easy to run repeatable, audit-ready assessments without the overhead of manual tracking or scattered documentation.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.