Table of Contents
Table of Contents
- What is the NIST Cybersecurity Framework (CSF)?
- What’s New in NIST CSF 2.0?
- How Is the NIST CSF 2.0 Structured?
- NIST CSF 2.0 Tools and Resources
- The NIST CSF Core Functions
- Why Is Implementing NIST CSF 2.0 Important?
- How to Implement NIST CSF 2.0 (Step-by-Step Guide)
- NIST CSF Best Practices
- How to Simplify NIST CSF 2.0 with Isora GRC
-
How to Implement NIST CSF FAQs
- What is NIST CSF 2.0?
- Is NIST CSF required by law?
- Who should use NIST CSF?
- How do you implement NIST CSF?
- What are the NIST CSF Functions?
- What are NIST CSF Profiles and how do you use them?
- What are the NIST CSF Implementation Tiers?
- What are Informative References in NIST CSF?
- How do you build a Current and Target Profile for NIST CSF?
- How often should the CSF be updated?
- What tools can simplify NIST CSF implementation?

The NIST Cybersecurity Framework (CSF) is challenging for many organizations to implement. NIST CSF is a set of guidelines and best practices to improve cybersecurity risk management. It offers a structured approach for organizations to identify risks, set goals, and track progress toward cyber resilience.
But NIST CSF implementation can also be challenging for teams. Some simply don’t know where to begin without clear direction. Others struggle with transitioning from NIST CSF Version 1.1 to 2.0, mapping existing practices to CSF outcomes, or translating progress in ways that make sense to non-security stakeholders.
This guide breaks NIST CSF 2.0 implementation into simple, practical steps. It explains how to define scope, assess risk, build CSF Profiles, and act on results. It also explores how NIST CSF tools can help teams simplify assessments, manage inventories, and turn strategy into measurable results.
Let’s start with the basics: What is NIST CSF?
Note: Like NIST, this guide uses the terms ‘cybersecurity,’ ‘information security,’ and ‘IT security’ interchangeably, mainly because they mean the same thing.
Implementing NIST CSF 2.0 helps organizations assess risk, build profiles, and track cybersecurity maturity through six core functions (Govern–Recover). This guide breaks the process into clear steps—from scoping to action planning—using NIST tools and real‑world application.
What is the NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework (CSF) is a voluntary set of guidelines and best practices for organizations to manage cybersecurity risks. It’s a straightforward approach for businesses of all sizes, industries, and maturity levels to identify, assess, and communicate about cyber risks more effectively.
Created by the National Institute of Standards and Technology (NIST), NIST CSF establishes a common language, or taxonomy, that organizations can use to discuss cybersecurity with internal and external parties. Unlike prescriptive standards (e.g., NIST SP 800-53) that give instructions or list technical controls, the CSF framework establishes general outcomes.
Basically, NIST CSF describes what good cybersecurity looks like, but it doesn’t explain how to make that vision a reality. Instead, it points to helpful resources, tools, and guidelines on the NIST CSF website. Here, organizations can find practical guidance on specific practices, controls, and methods to meet their unique needs.
Most organizations use the NIST CSF to:
- Understand and evaluate cybersecurity risks
- Set cybersecurity goals and track progress toward them
- Align cybersecurity practices with legal requirements or industry standards
- Improve communication about cybersecurity issues with customers, partners, and internal teams
- Prepare for, respond to, and recover from cybersecurity incidents
Today, NIST CSF is one of the most widely adopted cybersecurity frameworks worldwide. Versions 1.1 and 1.0 have been translated into 13 languages, and NIST CSF 2.0 is currently being translated into languages all around the globe.
Here’s what’s new in Version 2.0.
What’s New in NIST CSF 2.0?
Finalized in 2024, NIST CSF Version 2.0 is the first major update since the original framework was published in 2014. It was created in response to numerous comments on the draft version asking NIST to make the framework more accessible to non-critical infrastructure organizations.
The biggest changes in NIST CSF 2.0 are:
- A new “Govern” function
- New supply chain guidance
- Updated categories and subcategories
- Faster, simpler implementation
Of these changes, introducing governance, or how organizations make decisions about cybersecurity strategy, stands out the most.
Today, the six core functions of NIST CSF 2.0 are:
- Govern: Cybersecurity risk management strategies, expectations, and policies are established, communicated, and monitored.
- Identify: Cybersecurity risks are understood.
- Protect: Safeguards to manage cybersecurity risks are used.
- Detect: Cybersecurity attacks and compromises are identified and analyzed.
- Respond: Actions are taken regarding a detected cybersecurity incident.
- Recover: Assets and operations affected by a cybersecurity incident are restored.
Together, these updates make the NIST CSF more relevant, easier to use, and valuable for ALL organizations.
Now let’s explore how the NIST CSF is structured.
How Is the NIST CSF 2.0 Structured?
The simple structure of NIST CSF is intentional. It’s designed to help organizations strengthen their information security risk management (ISRM) programs with more flexibility than other frameworks.
NIST CSF 2.0 is organized around three main components:
- The CSF Core (Functions, Categories, Subcategories)
- CSF Profiles and Tiers
- A suite of practical resources (Informative References, Implementation Examples, Quick Start Guides)
Each section of the CSF defines outcomes, outlines steps to achieve them, and explains how to measure progress.
Here’s how each part works.
The NIST CSF Core
The CSF Core is the center of NIST CSF 2.0. It lists cybersecurity outcomes that define successful cybersecurity without explaining how to achieve those results. Instead, NIST links outcomes to supporting resources on the CSF website, where organizations can find more actionable guidance.
The Core has three layers:
- Functions: Six essential cybersecurity risk management activities
- Categories: Groups of related outcomes within each Function
- Subcategories: Specific cybersecurity tasks and activities within each category
Together, these parts help organizations assess current practices, define goals, and build profiles that guide NIST CSF implementations and improvements over time.
Next, let’s look at how Profiles and Tiers support that process.
The NIST CSF Profiles and Tiers
NIST CSF Profiles and Tiers help organizations implement their cybersecurity outcomes. Together, they provide a structured way to assess practices, define goals, and guide improvements.
CSF Profiles
A Profile is a set of cybersecurity outcomes selected from the CSF Core that describes how cybersecurity is managed for a specific part of the organization.
NIST CSF 2.0 has four types of Profiles:
- Organizational Profile: The overall structure that includes one or more Profiles (Current and Target) and supporting context like scope, assumptions, and evaluation methods.
- Current Profile: A snapshot of cybersecurity outcomes the organization is currently achieving. It reflects real-world practices across systems, departments, or the entire organization.
- Target Profile: The set of outcomes the organization wants to achieve based on business goals, risk tolerance, and regulatory requirements. It defines the future state.
- Community Profile: A shared Profile developed for a specific sector, threat, or technology. These can be used as a baseline or starting point for building a Target Profile.
By comparing the Current Profile to the Target Profile, organizations can identify gaps and prioritize improvements based on risk and business context.
CSF Tiers
The NIST CSF Implementation Tiers help organizations describe how well they manage cybersecurity across the scoped environment. Tiers focus on measuring the maturity and consistency of cybersecurity governance and execution.
NIST outlines four CFS Tiers:
- Tier 1 (Partial): Cybersecurity practices are informal or reactive. Risk is managed on a case-by-case basis.
- Tier 2 (Risk-Informed): Risk is considered, but practices are inconsistent organization-wide.
- Tier 3 (Repeatable): Practices are documented, applied consistently, and updated as needed.
- Tier 4 (Adaptive): Risk management is data-informed, agile, and integrated with business strategy.
While useful, these tiers are not scores or ratings. Instead, organizations can use them to benchmark maturity, communicate expectations, and guide planning. Using CSF Profiles and Tiers together is the best way to assess the current state, define objectives, and determine how to get there.
Fortunately, other NIST tools and resources are available to help, too.
NIST CSF 2.0 Tools and Resources
The NIST CSF 2.0 offers a suite of Framework resources to make cybersecurity outcomes practical. These tools are designed to help organizations translate the CSF into real-world implementation.
These resources complement the core guidance of NIST CSF and offer practical ways for organizations to understand, adopt, and operationalize this framework. They range from easy-to-use reference tools and example-driven guidance to detailed mappings that align NIST CSF outcomes with other common frameworks and standards.
Here are the best NIST CSF tools and resources available today.
Official NIST Resources and Tools
NIST maintains and updates an online library of resources for CSF 2.0 implementation. These tools provide detailed guidance, practical examples, and references to other cybersecurity standards. They include:
- CSF 2.0 Reference Tool: A simple online tool that lets users browse, search, and export the CSF Core guidance in human- and machine-readable formats.
- Searchable Catalog of Informative References: A library linking CSF outcomes to 50+ cybersecurity standards, guidelines, frameworks, regulations, and policies.
- Implementation Examples: Examples showing how to achieve cybersecurity outcomes with simple verbs that clarify what actions organizations can take, like “document,” “monitor,” “analyze,” and “assess.”
- Quick Start Guides: Short, targeted guides with actionable starting points for specific audiences and use cases (small businesses, enterprise risk managers, securing supply chains) and to support smoother transitions from earlier CSF versions.
- Community Profiles and Organizational Profile Templates: Pre-made templates and examples for different sectors, threat scenarios, or technology environments to help organizations define, prioritize, and track their security posture against common industry baselines.
- CSF 2.0 Webinar Series: Expert-led webinars that go deeper into specific topics with practical tips, real-world examples, and more detailed guidance for managing cybersecurity risks.
Collectively, these official NIST resources give organizations clear pathways to implementing CSF to meet operational goals and improve risk management strategies.
Additional NIST Publications for NIST CSF Implementation
Beyond the core CSF 2.0 resources, NIST recommends several publications that support implementation. These additional documents can help teams integrate cybersecurity into broader risk management practices to align with overall enterprise goals.
Key publications include:
- NIST IR 8286: A series offering guidance on how cybersecurity risk fits into broader ERM
- NIST SP 800-37 Rev 2: A framework for managing cybersecurity risk at the system and organizational levels
- NIST SP 800-53 Rev 5: A catalog of security controls to manage cybersecurity and privacy risks
Together, these complementary resources can help organizations get the most out of NIST CSF by making sure strategies are actually effective for addressing real-world risks and well-integrated into overall business practices.
NIST CSF 2.0 Mapping
Mappings connect NIST CSF outcomes to specific tasks or controls in other cybersecurity frameworks. They help organizations avoid duplication by showing how existing security activities already meet CSF requirements.
Common NIST CSF mappings include:
- ISO/IEC-27001:2022 to NIST CSF 2.0: Matches each CSF outcome to specific ISO 27001 requirements.
- NIST SP 800-37 Rev 2 to CSF v2.20: Links the steps required under FISMA to CSF outcomes.
- NIST SP 800-53 Rev 5 to Cybersecurity Framework v2.0: Connects security and privacy controls from SP 800-53 to specific CSF outcomes.
- CIS Controls v8.0 to CSF v2.0: Maps CIS recommended security actions to CSF outcomes.
- NIST CSF v1.1 to NIST CSF v2.0: Highlights differences between CSF versions 1.1 and 2.0
The NIST CSF Core Functions
The NIST CSF 2.0 Core organizes cybersecurity outcomes into six primary Functions: Govern, Identify, Protect, Detect, Respond, and Recover. Together, they cover the complete lifecycle of cybersecurity risk management.
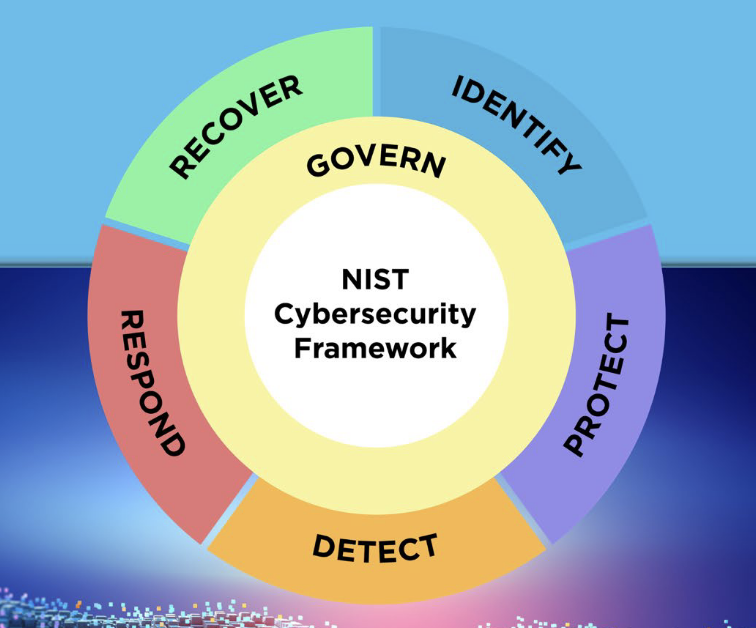
Source: NIST CSF 2.0, pg. 5
NIST illustrates the Core Functions as a wheel to show that they are closely connected and happen simultaneously, not in sequence. Here, Govern sits at the center because it shapes the policies, strategies, and guidelines that determine how well the other five Functions work.
| CSF Functions | Timing | Purpose |
| Govern, Identify, Protect, Detect | Continuous – ongoing process | Prevent incidents and prepare effectively |
| Respond, Recover | Ready at all times; activate as needed | Detect and effectively manage incidents |
Each Function breaks down into smaller Categories and even more specific Subcategories, clearly defining detailed outcomes for cybersecurity tasks and processes. The structure of NIST CSF helps organizations select and implement actions suited to their unique situation and needs.
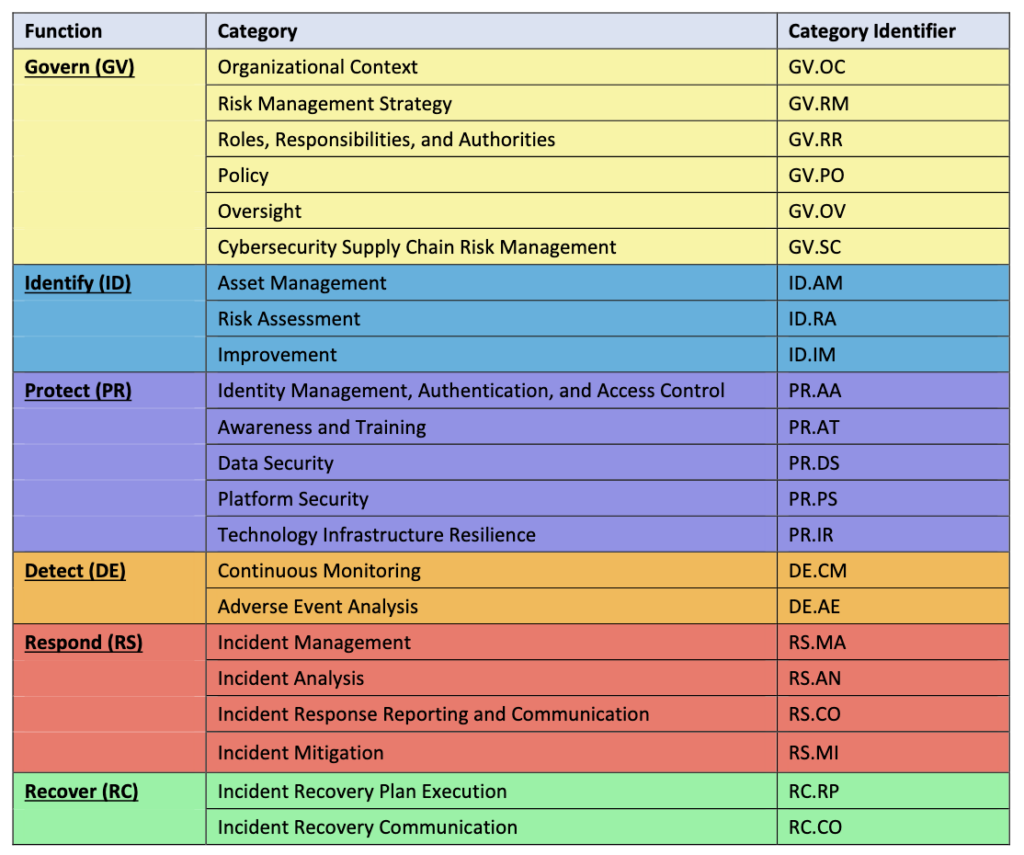
Source: NIST CSF 2.0, pg. 15
However, it’s important to note that the sequence or size of Functions, Categories, and Subcategories doesn’t set their relative importance or order of execution. Instead, organizations choose how to prioritize and operationalize these activities based on their own risk management needs and contexts.
Next, let’s explore each Core Function in more detail.
Govern
The Govern Function of NIST CSF 2.0 involves setting, communicating, and overseeing an organization’s cybersecurity strategy, policies, and expectations. It informs and directs the other Core Functions and helps organizations align cybersecurity efforts with their broader mission, stakeholder priorities, and risk management goals.
More specifically, Govern covers these Categories:
- Organizational Context: Understanding the organization’s mission, stakeholder expectations, key dependencies, and regulatory or contractual requirements that shape cybersecurity decisions.
- Risk Management Strategy: Defining and communicating the organization’s risk priorities, constraints, risk tolerance, and assumptions to guide decision-making.
- Roles, Responsibilities, and Authorities: Establishing roles, responsibilities, and accountability for better performance measurement and continuous improvement.
- Policy: Developing, sharing, and enforcing an organization-wide cybersecurity policy.
- Oversight: Reviewing and using results from cybersecurity activities to refine the risk management strategy over time.
- Cybersecurity Supply Chain Risk Management: Identifying, managing, monitoring, and continually improving processes that manage cybersecurity risks throughout the supply chain.
By introducing the Govern Function, NIST CSF 2.0 emphasizes that cybersecurity should be managed like an enterprise risk and that governance is key to make sure cyber strategies align with overall business objectives.
Identify
The Identify Function in NIST CSF involves understanding an organization’s cybersecurity risks. It helps organizations to know exactly what assets they have (data, hardware, software, systems, services, personnel) and how important each is to their overall goals and risk management strategies.
Identify covers three key activities:
- Asset Management: Cataloging and prioritizing assets based on their criticality to achieving the organization’s mission and managing risk.
- Risk Assessment: Analyzing and understanding cybersecurity risks, including threats to assets, operations, and individuals.
- Improvement: Regularly identify ways to improve cybersecurity processes, policies, and procedures across risk management.
This function helps organizations align cybersecurity efforts with the priorities set under the Govern Function. That way, efforts are focused on the most critical areas and opportunities for improvement first.
Protect
The Protect Function focuses on safeguarding the assets identified as critical to the organization. Once they understand what needs protection, organizations use this function to apply security controls aimed at reducing the likelihood and impact of cybersecurity incidents.
The Categories under Protect include:
- Identity Management, Authentication, and Access Control: Making sure that only authorized people, systems, and devices can access critical resources.
- Awareness and Training: Educating personnel so they understand cybersecurity responsibilities and can recognize and respond to potential threats.
- Data Security: Managing and securing data to protect its confidentiality, integrity, and availability.
- Platform Security: Securing physical and virtual platforms (operating systems, apps, firmware) according to their importance and risk level.
- Technology Infrastructure Resilience: Managing infrastructure security to keep operations continuous and critical assets protected.
Beyond preventing threats, protection helps organizations pursue opportunities and new advantages like customer trust and revenue growth.
Detect
The Detect Function involves monitoring for cybersecurity threats and identifying vulnerabilities. Promptly identifying unusual activity or indicators of compromise can help organizations respond to incidents more effectively and reduce the damage when they do occur.
Key activities under the Detect Function include:
- Continuous Monitoring: Regularly checking assets to spot irregular activities, suspicious events, or early signs of compromise.
- Adverse Event Analysis: Examining unusual events to understand what they mean and quickly identify potential cybersecurity incidents.
Early and accurate detection makes it easier to respond effectively, limiting the scale and severity of cybersecurity events.
Respond
The Respond Function covers how organizations handle cybersecurity incidents once they’re detected. An organized response helps contain the incident quickly, limit damage, and prepare the team for recovery.
Important Respond activities include:
- Incident Management: Coordinating responses after detecting an incident.
- Incident Analysis: Investigating incidents to understand the full impact and support recovery efforts.
- Incident Response Reporting and Communication: Keeping stakeholders informed about incidents, in line with legal and regulatory requirements.
- Incident Mitigation: Taking steps quickly to limit the incident’s spread and reduce its negative effects.
Effective incident response helps organizations control damage quickly to preserve operations and stakeholder confidence.
Recover
The Recover Function helps organizations return to normal operations following cybersecurity incidents. This phase focuses on restoring systems, services, and operations quickly while clearly communicating recovery efforts to internal and external stakeholders.
Recovery involves:
- Incident Recovery Plan Execution: Restoring systems and services affected by the incident to resume normal operations promptly.
- Incident Recovery Communication: Keeping stakeholders updated about recovery activities and status.
Recovery activities reduce downtime, minimize disruptions, and build trust with stakeholders.
Why Is Implementing NIST CSF 2.0 Important?
The NIST CSF offers a straightforward path to improving cybersecurity. It helps organizations assess their current practices, define goals, identify gaps, and measure progress. It can also make cyber risks and decisions easier to understand and communicate internally and externally.
Most organizations use NIST CSF to:
- Understand, assess, and describe a current and target cybersecurity posture
- Identify gaps in current programs and processes
- Identify and prioritize opportunities for improvement with a continuous, repeatable process
- Evaluate progress toward a target cybersecurity posture
- Align with nationally recognized best practices
- Pinpoint current practices that might surpass recommendations
- Communicate about cybersecurity posture in a common language to internal and external stakeholders (customers, regulators, investors, policymakers).
Beyond managing cybersecurity risks internally, the NIST CSF can also help organizations with third party risk management (TPRM) for consistency across vendors, suppliers, and business partners.
Here’s a closer look at some of the benefits of using NIST CSF.
Benefits of Implementing NIST CSF
The benefits of NIST CSF 2.0 are often what drive organizations to implementation. Its two biggest strengths are:
- Flexibility: It can support organizations of every size, industry, and maturity level.
- Adaptability: It can evolve with emerging technologies like artificial intelligence, cloud computing, and IoT-connected devices.
More specifically, the benefits of implementing NIST CSF for organizations include:
- Improved internal communication around cybersecurity risks and goals, so executives, managers, and IT professionals can understand each other.
- Reduced cybersecurity risks across operations, including privacy risks, supply-chain vulnerabilities, and threats posed by emerging technologies.
- Stronger cybersecurity posture with proactive practices, workforce development, and hiring and training strategies.
- Simpler compliance audits with cybersecurity activities aligned directly with widely recognized standards and regulations.
- Faster incident response for quicker, more precise reactions during cyber incidents.
- More visibility into strengths, vulnerabilities, and progress.
- Strategic decision-making to align investments with broader business goals for maximum value.
In other words, adopting NIST CSF today can help organizations improve cybersecurity today and stay flexible enough to face new risks tomorrow.
Challenges with Implementing NIST CSF
NIST CSF offers clear advantages, but implementation can also introduce challenges. Common challenges with NIST CSF are:
- Complexity: The framework’s broad scope and terminology can feell overwhelming when organizations need clear goals to stay focused and avoid confusion.
- Limited Resources: Smaller organizations might struggle with insufficient budget, staff, or experience to use the framework without external support.
- Integration Issues: Companies already using other frameworks or standards may have trouble aligning their practices with NIST CSF, resulting in redundant or duplicated efforts.
- Checklist thinking: Seeing the framework as just another compliance exercise instead of an ongoing, strategic effort minimizes its real-world impact and leads to superficial improvements.
- Communication gaps: Clearly explaining cybersecurity risks in non-technical terms can be challenging, especially to engage executives or non-security teams.
Organizations can manage these challenges by setting realistic priorities, starting small, using helpful resources, and regularly communicating progress to leadership.
Fortunately, this guide is also here to help.
How to Implement NIST CSF 2.0 (Step-by-Step Guide)
Implementing NIST CSF 2.0 takes a structured yet flexible approach. The framework provides detailed guidance, but breaking implementation down into simpler steps can make it more manageable.
The basic steps to implement NIST CSF 2.0 are:
- Prioritize and Scope
- Orient the Organization
- Create a Current Profile
- Conduct a NIST CSF Risk Assessment
- Create a Target Profile
- Identify, Analyze, and Prioritize Gaps
- Implement an Action Plan
The goal is a consistent, repeatable process tailored to each organization’s cybersecurity risks, resources, and objectives. However, before beginning implementation, organizations must create a plan to regularly communicate progress updates to stakeholders, especially senior executives.
Organizations new to NIST CSF can start by applying it to a small, well-defined area or function. This targeted approach lets teams familiarize themselves with the framework before implementing it organization-wide.
With these considerations in mind, here’s a simple, step-by-step guide to implementing NIST CSF 2.0.
Step 1: Prioritize and Scope
Implementing the NIST CSF starts with clearly defining what needs protection and why. Begin by clarifying key business objectives, critical processes, and strategic priorities. Understanding how cybersecurity risks could affect these objectives will provide the context needed to prioritize risk response efforts.
At this stage, teams should:
- Clarify strategic goals and priorities. Identify critical services, functions, and objectives that cyber incidents could disrupt.
- Assess current cybersecurity risks. Describe existing threats and vulnerabilities, evaluating how they align with risk tolerance.
- Identify specific areas for framework application. Determine which business units, processes, or technology environments will use the NIST CSF first.
Initial prioritization helps organizations shape the entire implementation process with clear boundaries for scope and effort. But it can also help them tailor framework applications so implementation aligns with their unique operational requirements and available resources.
Step 2: Orient the Organization
Next, clearly identify the assets, systems, requirements, and risk management practices that fall within scope. This step creates clarity about what exactly needs protection and how the organization currently manages risks related to these assets.
Specifically, organizations should:
- List critical systems and assets. Clearly identify and document resources like data, software, hardware, people, and facilities that directly support key business objectives.
- Understand current requirements. Identify legal, regulatory, contractual, and internal cybersecurity requirements already in place, plus existing organizational policies and best practices.
- Document existing risk management practices. Note current risk management strategies and methods to understand how risks are addressed today.
Focus on the most critical or sensitive areas first and expand implementation to cover other assets over time.
Finally, this step involves choosing how to evaluate the current cybersecurity posture to create a Current Profile. Organizations can do this internally via self-assessment using their own staff and expertise, or externally using third-party specialists. This baseline understanding will inform future steps and help organizations track real progress against well-defined cybersecurity goals.
💚 With Isora GRC’s IT Asset Inventory, organizations can list and categorize assets, vendors, and applications, all in one place. Connect the inventory via API or update information manually and link it directly to assessments and audit evidence, so it’s easy to see which assessments are in scope and how each maps to risk and compliance needs.
Step 3: Create a Current Profile
The next step is to develop a Current Profile to describe the organization’s existing cybersecurity practices. Creating an Organizational Profile involves mapping cybersecurity outcomes to the relevant Categories and Subcategories in the Framework Core.
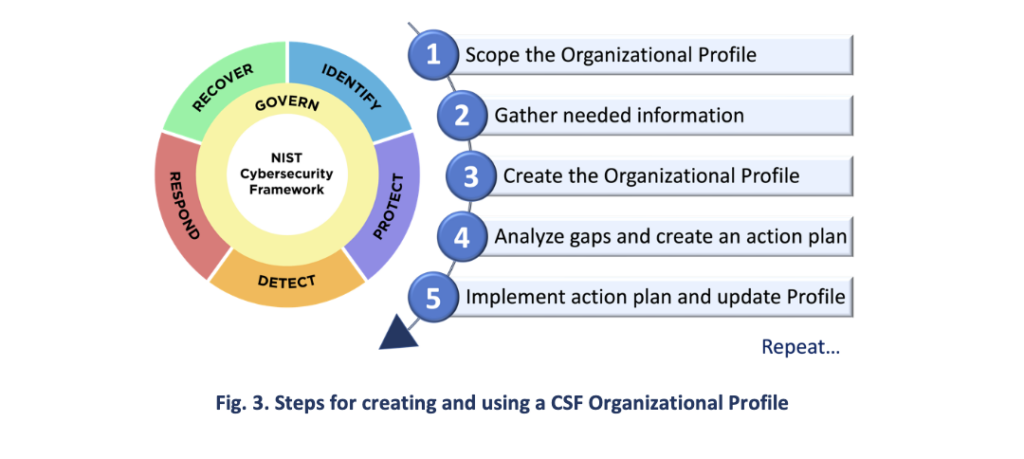
Source: NIST CSF 2.0, pg. 6
Here’s how to create a NIST CSF Current Profile:
- Scope the Organizational Profile. Decide what aspects of the cybersecurity program to include and clearly define the scope (departments, systems, processes).
- Gather needed information. Collect input from executives about priorities, resources, and strategic goals, and work closely with managers and practitioners to align processes.
- Create the Organizational Profile. Use the selected evaluation method (self-evaluation or facilitated assessment) to map current cybersecurity practices to NIST CSF’s Category and Subcategory outcomes. Clearly indicate whether each outcome is achieved fully, partially, or not at all. Adapt the Organizational Profile template to meet business needs, adding and removing columns freely.
- Map to an Implementation Tier. Determine overall cybersecurity maturity by comparing current practices against NIST’s Implementation Tier. These tiers reflect the sophistication and consistency of the entire cybersecurity risk management program, not individual outcomes.
-
- Tier 1 (Partial): Informal or inconsistent cybersecurity practices
- Tier 2 (Risk-Informed): Defined cybersecurity practices, not yet consistently applied
- Tier 3 (Repeatable): Clearly documented, consistently applied cybersecurity practices
- Tier 4 (Adaptive): Continuously evolving cybersecurity practices fully integrated with broader risk management strategies
- Identify alignment with existing standards. Note any cybersecurity tools, standards, or processes already in place and check available mappings from industry and standards organizations to link NIST CSF elements.
With the Current Profile complete, organizations can:
- Conduct a gap analysis. Compare current cybersecurity practices against future goals. Gap analysis results will become key inputs for system-level cybersecurity plans and improvement initiatives.
- Implement action plans. Regularly update the Current Profile as gaps are addressed and target states are reached. Share updates through risk registers, progress reports, and with executive stakeholders.
NIST offers Organizational Profile templates and Community Profiles tailored to specific industries and common challenges to simplify profile creation and help teams better articulate their cybersecurity posture.
Step 4: Conduct a NIST CSF Risk Assessment
With a clear understanding of current practices, the next step is assessing the organization’s cybersecurity risks. This involves identifying, analyzing, and evaluating risks to understand their likelihood and potential impact.
Ideally, a NIST CSF risk assessment will build on an existing risk management process. At this stage, organizations should:
- Identify cybersecurity risks. Pinpoint potential threats, vulnerabilities, and operational dependencies that could disrupt systems, compromise data, or undermine strategic objectives.
- Analyze the likelihood and impact. Evaluate how likely each risk is to occur and how serious the consequences would be if it did. Use real-world data, threat intelligence, and environmental context to make informed decisions.
- Flag risks that exceed tolerance. Identify risks that fall outside accepted risk thresholds and address them first in the Target Profile and action plan.
Risk assessments provide an up-to-date view of the organization’s threat landscape and risk exposure, but they also set the stage for defining what “improved” looks like in the next step. The goal is to go beyond theoretical analysis and build a realistic understanding of how cybersecurity events could actually affect the organization’s mission, operations, and stakeholders.
The results of this risk assessment will inform two things:
- Which CSF outcome to prioritize in the Target Profile
- Which Implementation Tier best reflects the level of maturity needed to manage those risks effectively
For those with mature risk management programs, this step might require simply refining data. For others, it’s a valuable opportunity to establish a repeatable, structured risk assessment process that aligns with broader business goals.
💚Isora GRC’s Self-Assessment Questionnaires speed up this step with pre-built NIST CSF templates and customizable questions tailored to different teams. In Isora, organizations can easily send questions directly to people who manage specific systems or data, and their answers automatically come back organized into clear reports, showing exactly where risks are and how serious they might be.
Step 5: Create a Target Profile
After assessing cybersecurity risks, the next step is to define a Target Profile. The Target Profile represents the cybersecurity outcomes that an organization wants to achieve. It helps prioritize improvements by translating risk findings into a clear set of future goals. At this stage, organizations should:
- Define desired cybersecurity outcomes. Identify which Categories and Subcategories from the Framework Core should be achieved to reduce risk to acceptable levels.
- Account for organizational context. Factor in the organization’s current risk environment, mission-critical objectives, regulatory obligations, and available resources.
- Document supporting tools and strategies. Identify the cybersecurity standards, methods, technologies, and guidelines to meet the desired outcomes.
- Choose a Target Implementation Tier. Based on risk tolerance and priorities, select the Tier (Partial, Risk-Informed, Repeatable, or Adaptive) that best reflects the desired level of cybersecurity maturity across the scoped environment.
Some organizations might evaluate each Subcategory individually, while others might opt for a broader approach, focusing on strategic outcomes across the entire environment. Either option is valid so long as it reflects business needs and risk priorities. Remember, Target Profiles aren’t static, so revisit and revise them regularly to stay aligned with real-world conditions.
Step 6: Identify, Analyze, and Prioritize Gaps
After the Current Profile and the Target Profile are complete, the next step is identifying the gaps between them. These gaps represent the difference between what the organization is doing today and what it wants to achieve in the future. Here, organizations can:
- Compare the Current and Target Profiles. Identify any Category or Subcategory outcomes in the Target Profile that are missing or only partially met in the Current Profile.
- Review the Target Implementation Tier. Determine whether current risk management practices meet the desired Tier level and where they fall short.
- Define each gap. It could mean missing practices or where existing efforts fall short of risk tolerance or quality expectations.
Once gaps are identified, the next step is to prioritize them based on:
- Mission-critical objectives
- Legal and regulatory obligations
- Severity and likelihood of potential consequences
- Available resources and capacity to act
Then, organizations can:
- Assign mitigation priorities. Rank each gap based on its urgency and impact if left unaddressed.
- Identify potential solutions. Consider the controls, process changes, or technology investments needed to close each gap.
- Perform a cost-benefit analysis (CBA). Evaluate the feasibility, effort, and value of each proposed solution
- Build an action plan. Organize selected mitigation actions into a clear, prioritized roadmap based on current resources, business goals, and the risk environment.
Sometimes, the organization may already be close to its Target Environment. In others, there may be several significant gaps to address. Either way, this step is about making sure improvements are realistic, focused, and tied directly to real risk priorities. The goal is not to “close gaps,” but to improve cybersecurity posture to stay aligned with the organization’s real-world risk profile.
Step 7: Implement an Action Plan
The final step is implementing the plan. After identifying and prioritizing gaps, organizations determine which steps to take, how to take them, and how to measure progress over time. The goal is to steadily close the gaps between the Current and Target Profiles while staying aligned with overall strategic objectives.
To implement an action plan, organizations can:
- Address identified gaps. Implement cybersecurity controls and process improvements, prioritizing those related to critical business functions and highest-risk areas first.
- Use Informative References. Consult NIST and sector-specific guidelines to turn strategic objectives into actionable tasks.
- Monitor progress. Regularly track progress via assessments, status checks, and risk reviews, adjusting as necessary.
Remember, implementing NIST CSF is iterative and ongoing. Regularly revisit profiles and implementation tiers to reflect new improvements, new threats, evolving technology, and shifting business goals.
💚Isora GRC’s IT Risk Register helps organizations keep track of each identified risk, who’s responsible for fixing it, and what’s being done to address it. It connects every risk directly to the related systems, making it easy to see which problems have been solved and which ones still need attention.
NIST CSF Best Practices
A few best practices are key to maximizing the NIST CSF’s flexibility. The framework offers a structured approach, but organizations can apply it as they see fit. Whether just getting started or refining an existing program, these CSF tips can help teams stay more focused and effective during implementation.
Here are a few best practices for implementing NIST CSF.
Build on the Govern Function
Cybersecurity governance depends on strong leadership and solid objectives. Executives set high-level goals and risk appetites, which managers and practitioners then carry through the rest of the business.
Organizations can use the Govern Function to:
- Establish clear direction. Executives define the overall cybersecurity goals and expectations that shape how risk is managed across business units, divisions, or departments.
- Translate strategy into action. Managers take that direction and build implementation plans using Target Profiles, risk registers, POA&Ms (Plans of Action and Milestones), and other planning tools.
- Drive operational execution. Practitioners deploy controls, monitor performance, and manage day-to-day cybersecurity operations.
- Support informed decision-making. Practitioners report key risk and performance indicators (KPIs and KRIs) to help managers and executives plan as needed.
- Create a continuous feedback loop. Governance activities are updated as business conditions or priorities change and reflected in revised Profiles and Implementation Tiers.
Effective governance helps prevent cybersecurity from becoming siloed or reactive. Instead, it becomes part of how the organization plans, operates, and evolves, supported by accountability, communication, and alignment at every level.
Start with the CSF Profiles
The CSF Profiles are one of the most practical tools in the NIST CSF 2.0. They help organizations translate abstract framework outcomes into a cybersecurity program that actually fits each organization’s unique goals, risks, and resources.
There are two main types of NIST CSF Profiles:
- A Current Profile reflects the cybersecurity outcomes an organization achieves today.
- A Target Profile defines an organization’s desired state based on its risk appetite, priorities, and business objectives.
Between the two, organizations can see where they are, where they want to go, and what gaps they need to close to meet those goals.
For organizations just getting started with NIST CSF implementation, Community Profiles are a great place to start. These pre-built examples are tailored to specific sectors, threat scenarios, and technologies. CSF Community Profiles are a great way to:
- Establish a realistic starting point
- Save time defining outcomes from scratch
- Align with industry norms and expectations
Organizations can use NIST CSF Profiles to:
- Drive implementation
- Communicate clearly
- Track progress over time
Whether customizing from scratch or adapting a Community Profile, start with Profiles to keep NIST CSF implementations grounded, focused, and strategically aligned.
Use NIST CSF Tiers to Inform Profiles
The NIST CSF Implementation Tiers help organizations describe how well they manage cybersecurity risk. Ranging from Tier 1 (Partial) to Tier 4 (Adaptive), the Tiers give organizations a way to gauge cybersecurity maturity across the entire environment or within a specific scope.
Tiers are optional, but they’re also incredibly useful for setting expectations, communicating with stakeholders, and making decisions about where to invest. It considers not just what organizations do, but how consistently, effectively, and strategically they do it.
Organizations can use the CSF Tiers to:
- Benchmark current maturity. Map risk management practices to the Tier descriptions during the Current Profile phase for a clear picture of how consistent and integrated a program is today.
- Set realistic targets. For the Target Profile, use the Tiers to define where the organization wants to go, whether that means moving from informal practices to formalized processes, or evolving from documented controls to dynamic, enterprise risk-management.
- Support internal alignment. Tiers give leadership, risk managers, and practitioners a common language to discuss cybersecurity maturity, without getting lost in technical details.
Remember, the Tiers are not a score or a pass/fail system. Instead, they’re a means to describe how cybersecurity is managed in practice. So, use them to guide implementation decisions, not to judge performance in isolation.
Select Controls Using Informative References
One of NIST CSF’s most powerful yet often underused features is its built-in network of Informative References. These references link each CSF outcome to detailed, actionable controls from other well-established frameworks like NIST SP 800-53, ISO/IEC 27001, and CIS Controls.
Teams can use the CSF Informative References to see how existing standards already support their CSF goals or to identify which controls to adopt when building a cybersecurity program from scratch.
Organizations can use Informative References to:
- Translate outcomes into action. The CSF tells organizations what to achieve. Informative References help them figure out how by pointing to specific, proven controls that support each Subcategory.
- Bridge the gap between frameworks. The references make it easier to align work with CSF for organizations already using ISO 27001, CIS Controls, or NIST RMF, without duplicating effort.
- Support control selection and documentation. References provide ready-made justification for why a particular control was chosen to meet a given outcome during assessments, planning, or audits.
Review Quick Start Guides Regularly
NIST’s Quick Start Guides are some of the most actionable resources in the CSF 2.0 toolkit. Each guide focuses on a specific audience or implementation challenge, like small business adoption, supply chain risk, or integrating CSF with enterprise risk management, and distills the framework into tactical first steps.
QSGs are ideal for organizations that want to move quickly without getting lost in the details. They’re also helpful for onboarding new stakeholders, aligning internal teams, or kicking off CSF implementation in a specific department or business unit.
Organizations can use Quick Start Guides to:
- Get targeted guidance. Each guide is tailored to a specific use case, making it accessible to risk managers, IT leads, and procurement teams alike.
- Accelerate onboarding. QSGs are perfect for introducing new teams to the CSF because they reduce confusion and build confidence early.
- Stay current. NIST updates these guides regularly to reflect evolving threats, technologies, and best practices.
However, reviewing these guides isn’t a one-and-done task. As organizations evolve, revisiting relevant QSGs can help refine strategy, unlock new efficiencies, and make sure implementations stay aligned with the CSF framework and operational goals.
Take Advantage of Implementation Examples
NIST CSF 2.0 includes Implementation Examples, or short descriptions of how organizations might achieve specific outcomes. While they aren’t required or exhaustive, they are one of the most useful resources for turning high-level goals into real, day-to-day actions.
Each example is tied to a Subcategory and describes an activity using clear, action-oriented language with verbs like ‘document,’ ‘monitor,’ ‘analyze,’ or ‘review.’ Intentionally flexible, these examples are meant to spark ideas, support planning, and reduce ambiguity, especially for teams that are new to cybersecurity frameworks or attempting to align multiple departments.
Organizations can use Implementation Examples to:
- Clarify what outcomes look like in practice. Examples help anchor Subcategories that feel abstract or broad in something tangible.
- Build shared understanding across teams. Use Implementation Examples to align expectations between technical and non-technical stakeholders.
- Accelerate decision-making. Teams can use the examples as starting points for risk mitigation plans, control design, or internal guidance, rather than starting from scratch.
Implementation Examples make the CSF more accessible for small teams, cross-functional groups, and organizations without a dedicated cybersecurity strategist. As with all CSF resources, the goal isn’t to follow every example exactly. Instead, it’s to use them as a bridge from framework to action, to make NIST CSF implementation real.
How to Simplify NIST CSF 2.0 with Isora GRC
Implementing NIST CSF 2.0 takes structured assessments, clear documentation, and ongoing visibility across systems and stakeholders. Fortunately, Isora GRC simplifies every step of the process with workflows built specifically for security teams.
Instead of juggling spreadsheets, emails, and outdated tools, Isora GRC brings everything into one platform. It supports each phase of NIST CSF implementation, from scoping and assessment to reporting and remediation, making it easier to coordinate across departments, vendors, and leadership.
Here’s how Isora GRC helps organizations put NIST CSF 2.0 into action:
- Run structured, repeatable assessments. Use pre-built CSF-aligned questionnaires and dashboards to collect, store, and analyze responses across Functions, Categories, and Subcategories. Quickly identify gaps and track progress over time.
- Build and maintain cyber and supply chain inventories. Link systems, vendors, and applications to assessments, documents, and risk records, all in one place. This supports the Identity and Govern Functions plus end-to-end visibility across internal and third-party assets.
- Log and track risks in a collaborative register. Capture risks uncovered during assessments and link them to relevant assets. Use built-in risk matrices and scorecards to prioritize remediation and communicate clearly.
- Automate reporting and demonstrate compliance. Generate downloadable reports, visual scorecards, and audit-ready exports aligned with CSF structure and terminology. Show progress, support decision-making, and reduce reporting overhead.
With Isora GRC, organizations can turn the NIST CSF from a static framework into a living, collaborative process. The result is a faster, more practical way to operationalize cybersecurity goals, communicate risk, and drive continuous improvement.
Check out the interactive demo of questionnaire and survey management in Isora GRC below — or request a personalized demo.
How to Implement NIST CSF FAQs
What is NIST CSF 2.0?
NIST CSF 2.0 is the most recent update to the NIST Cybersecurity Framework (CSF). It adds guidance beyond critical infrastructure, includes a new Govern Function, updates categories and subcategories, and links to resources like Quick Start Guides and Implementation Examples to make implementation easier for all organizations.
Is NIST CSF required by law?
No, NIST CSF is voluntary, not required by law. However, many organizations use it to meet regulatory requirements, prepare for audits, or align with other standards like NIST SP 800-53, ISO/IEC 27001, or CIS Controls. Today, it’s widely adopted across industries like finance, education, and government.
Who should use NIST CSF?
All organizations that want to manage cybersecurity risk more effectively can use the NIST CSF. It applies to all sectors and sizes, from small institutions to large enterprises, and is useful for both technical and non-technical stakeholders.
How do you implement NIST CSF?
Implementing NIST CSF involves seven steps:
- Prioritize and scope the effort
- Orient the organization
- Create a Current Profile
- Conduct a NIST CSF risk assessment
- Create a Target Profile
- Identify and prioritize gaps
- Implement an action plan
Organizations can use these steps to start small and scale up. NIST provides the tools, templates, and guidance to support each phase.
What are the NIST CSF Functions?
The NIST CSF 2.0 includes six Functions that cover the full cybersecurity lifecycle. They help organize and structure a cybersecurity program from start to finish. They are:
- Govern: Set strategy, roles, policies, and oversight for cybersecurity
- Identify: Understand risks, assets, systems, and dependencies
- Protect: Put safeguards in place to protect critical systems and data
- Detect: Find threats and suspicious activity early
- Respond: Take action during a cybersecurity incident
- Recover: Restore systems and operations after an incident
Together, these Functions help teams plan, manage, and improve cybersecurity to meet business goals.
What are NIST CSF Profiles and how do you use them?
NIST CSF Profiles help organizations describe and manage their cybersecurity posture. Combined, they show what outcomes the organization is achieving today and what goals it wants to meet in the future. There are three types of Profiles in NIST CSF 2.0:
- Current Profile: The outcomes that an organization is already achieving.
- Target Profile: The outcomes an organization wants to achieve based on its goals, risks, and priorities.
- Community Profile: A shared set of outcomes developed by NIST for a specific sector, threat, or technology. Organizations can use these as a starting point to create their own Target Profile.
To use Profiles, start by building a Current Profile based on existing cybersecurity practices. Then, define a Target Profile that reflects business goals. Any differences between the two represent gaps to be addressed by improvement efforts. Beginning with Community Profiles can help organizations save time and align with sector-specific expectations.
What are the NIST CSF Implementation Tiers?
The NIST Cybersecurity Framework Implementation Tiers describe how well an organization manages cybersecurity risk. They help communicate the maturity of risk management practices across the organization. There are four Tiers:
- Tier 1 (Partial): Cybersecurity practices are informal or inconsistent, and risk is managed ad hoc or as a reaction.
- Tier 2 (Risk-Informed): Risk is considered in some decisions, but practices aren’t yet consistent organization-wide.
- Tier 3 (Repeatable): Cybersecurity processes are documented, followed regularly, and updated as needed.
- Tier 4 (Adaptive): Risk management is flexible, data-informed, and fully integrated with business operations.
The CSF Tiers are not scores or ratings. Instead, they help organizations understand their current state and the maturity level needed based on risk, resources, and priorities.
What are Informative References in NIST CSF?
Informative References connect each CSF outcome to detailed controls and guidance from other well-known frameworks like NIST SP 800-53, ISO/IEC 27001, and CIS Controls. These references help organizations:
- Turn high-level outcomes into specific actions
- Make it easier to align CSF implementation with existing standards and regulatory requirements
- Justify control choices and reduce duplication across frameworks
Organizations can use Informative References during assessments, planning, and audits to select controls, support documentation, and stay consistent across teams.
How do you build a Current and Target Profile for NIST CSF?
The NIST CSF Profiles help organizations compare their current cybersecurity posture to a desired future state.
- A Current Profile maps existing practices to the CSF Core.
- A Target Profile outlines the outcomes the organization wants to achieve based on risk, priorities, and resources.
Here’s how to build a Current Profile:
- Define the scope. Decide which departments, systems, or processes to include.
- Document current practices. Map existing activities to the CSF Categories and Subcategories.
- Evaluate each outcome.
- Identify the Implementation Tier.
- Note supporting standards.
Here’s how to build a Target Profile:
- Set desired outcomes. Identify the CSF outcomes needed to meet business and risk objectives.
- Factor in requirements. Consider regulatory obligations, threat landscape, and organizational goals.
- Select a Target Tier. Choose the maturity level needed to manage cybersecurity risk effectively.
- Identify resources and constraints. Note what will be required to reach the target state.
- Document the path forward. Use the gap between Current and Target Profiles to guide planning.
Together, these Profiles create a structured view of where the organization is, where it wants to go, and what actions are needed to get there.
How often should the CSF be updated?
Organizations should review and update their CSF implementation on a regular schedule, such as annually or after significant changes in business operations, technology, threat landscape, or compliance obligations. Frequent updates help keep the CSF Profiles aligned with evolving risks, objectives, and maturity.
What tools can simplify NIST CSF implementation?
Tools like Isora GRC simplify NIST CSF implementation by streamlining assessments, managing system and vendor inventories, logging risks, and automating reporting. NIST also provides free resources for organizations, including the CSF 2.0 Reference Tool, Quick Start Guides, and prebuilt templates. Individually, these tools can support faster adoption, better tracking, and improved cross-team collaboration. Together, they make NIST CSF implementation a breeze.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.