Table of Contents
Table of Contents
- What is the FFIEC CAT?
- Why is the FFIEC CAT Being Retired?
- What will replace the FFIEC CAT?
- How to Transition Smoothly from FFIEC CAT
- How Isora GRC Helps with the FFIEC CAT Transition
-
Replacing the FFIEC Cybersecurity Assessment Tool FAQs
- What will replace the FFIEC CAT?
- What is the NIST Cybersecurity Framework (CSF) 2.0?
- What is the CRI Profile?
- How should our institution choose between NIST CSF 2.0 and the CRI Profile?
- Can we still use the FFIEC CAT before the deadline?
- How can we transition off the FFIEC CAT without disrupting compliance?
- How does this transition affect regulatory audits and oversight?
- What happens if we don’t replace the FFIEC CAT by the sunset date?
- Does the FFIEC endorse any specific replacement for the CAT?
- Is the NCUA ACET still supported after the FFIEC CAT sunset?
- Can we use an IT Security Risk Management platform to manage the transition?

For nearly a decade, the FFIEC Cybersecurity Assessment Tool (CAT) has helped banks, credit unions, and other regulated institutions measure their cybersecurity maturity and identify gaps in their control environments. First introduced in 2015, the CAT offered a standardized way to evaluate risk posture in an increasingly complex threat landscape.
The FFIEC will sunset its Cybersecurity Assessment Tool (CAT) on August 31, 2025. Institutions should prepare to replace it with frameworks like NIST CSF 2.0 or the CRI Profile. The CAT will no longer be maintained. Its rigid, manual structure no longer meets regulatory expectations or the demands of modern cyber risk management.
This change reflects more than the removal of a tool. It marks a shift toward integrated, outcome-driven cybersecurity frameworks such as NIST CSF 2.0, CISA’s Cybersecurity Performance Goals, and the CRI Profile. Regulators now expect institutions to adopt flexible, risk-informed approaches that align cybersecurity oversight with operational risk and business priorities.
The FFIEC will sunset its Cybersecurity Assessment Tool (CAT) on August 31, 2025.
This guide explains what the FFIEC CAT sunset means for your organization. It outlines which frameworks are replacing the CAT and how to make a smooth, strategic transition that improves oversight, audit readiness, and long-term resilience.
What is the FFIEC CAT?
The FFIEC Cybersecurity Assessment Tool (CAT) is a voluntary self-assessment that helps financial institutions evaluate cyber risk and maturity. It was introduced in June 2015 by the Federal Financial Institutions Examination Council (FFIEC).
It combined a set of fundamental security controls with a structured framework to measure how much a given institution is exposed to cyber threats and how prepared it is to respond.
The CAT consists of two main components:
- Inherent risk profile: This helps institutions determine their risk exposure based on factors like technologies used, delivery channels, and third-party relationships.
- Cybersecurity maturity: Measures the institution’s implementation of cybersecurity controls across five domains: Cyber Risk Management and Oversight, Threat Intelligence and Collaboration, Cybersecurity Controls, External Dependency Management, and Incident Management and Resilience.
Over time, the FFIEC CAT became widely adopted across community banks, credit unions, and other regulated financial institutions, offering a consistent way to assess and document cybersecurity posture. While the tool was never mandatory, the structure made it a useful benchmark, especially during regulatory examinations.
However, as the cyber threat landscape grew more complex, the CAT’s limitations became more apparent. The static format, lack of automation, and limited alignment with newer frameworks like NIST CSF 2.0 prompted many institutions to seek more modern approaches.
Why is the FFIEC CAT Being Retired?
The decision to retire the FFIEC CAT, outlined in the official FFIEC CAT Sunset Statement, signals a shift away from static self-assessments toward more dynamic, performance-based cybersecurity tools.
According to the FFIEC, several newer and more effective tools are now available. Rather than updating the CAT, the Council states that institutions should instead refer directly to “new government resources, including the National Institute of Standards and Technology (NIST) Cybersecurity Framework 2.0 and the Cybersecurity and Infrastructure Security Agency’s (CISA) Cybersecurity Performance Goals.”
Key Reasons for Retirement
1. Modern Frameworks Have Superseded the CAT
The FFIEC acknowledged that while the CAT’s core controls remain sound, resources like NIST CSF 2.0, CISA’s Cross-Sector and Sector-Specific Cybersecurity Performance Goals, and the Cyber Risk Institute (CRI) Cyber Profile now offer more advanced, outcome-focused approaches to managing cyber risk.
2. The CAT Will Not Be Updated
The FFIEC explicitly stated it will not revise the CAT to align with newer frameworks. This means the tool will become increasingly disconnected from current standards for cybersecurity risk management and measurement.
3. Outcome-Based Expectations Have Replaced Maturity-Level Assessments
Modern regulatory guidance focuses on demonstrable cybersecurity outcomes. The CAT’s descriptive maturity levels are no longer sufficient to meet these expectations. Frameworks like NIST CSF 2.0 emphasize performance goals and risk-informed decision-making, helping institutions prioritize cybersecurity efforts that reduce actual risk.
4. Lack of Automation and Integration
The FFIEC notes that institutions should use self-assessment tools that are “commensurate with their risk” and that support an effective control environment. The CAT, built as a manual, standalone worksheet, lacks the automation, integrations, and workflow capabilities needed for today’s risk programs.
What will replace the FFIEC CAT?
The FFIEC has not endorsed a single replacement but has named several well-established frameworks and tools as suitable alternatives.
According to the official FFIEC CAT Sunset Statement, institutions should look to “new and updated government and industry resources” that align better with today’s cybersecurity priorities. These include the following.
NIST Cybersecurity Framework (CSF) 2.0
The NIST CSF 2.0 is the most widely recommended replacement for the FFIEC Cybersecurity Assessment Tool. Updated to reflect current threats and industry needs, NIST CSF 2.0 provides a flexible, risk-based framework that helps organizations:
- Identify, assess, and manage cyber risks across the organization
- Align security efforts with business objectives
- Implement and measure progress toward Cybersecurity Performance Goals (CPGs)
Unlike the FFIEC CAT, which focuses on control maturity in a fixed model, NIST CSF 2.0 encourages continuous improvement and adaptability. It also provides stronger alignment with federal guidance, including CISA’s CPGs, making it more relevant for today’s threat landscape.
CISA Cybersecurity Performance Goals (CPGs)
Published by the Cybersecurity and Infrastructure Security Agency (CISA), the CPGs are a set of prioritized, measurable practices based on the NIST CSF. The FFIEC calls attention to both the Cross-Sector Goals and the upcoming Financial Sector-specific CPGs, stating these are “developed to help organizations of all sizes and sectors manage and reduce their cybersecurity risk.”
Institutions can use CPGs to:
- Benchmark current practices against federal standards
- Prioritize controls based on risk reduction potential
- Align with NIST CSF 2.0 and demonstrate measurable security outcomes
Cyber Risk Institute (CRI) Profile
The CRI Profile, developed by the Cyber Risk Institute in collaboration with the financial sector and regulatory agencies, is another major alternative. Built specifically for financial institutions, it translates NIST CSF and other global standards into a structured profile tailored for compliance and operational risk management.
Key benefits of the CRI Profile include:
- Clear mappings to regulations and supervisory expectations
- Strong focus on financial sector-specific risks
- Support for scalable implementation across different institution sizes
The CRI Profile is gaining traction as a formalized, regulator-endorsed method for assessing cybersecurity readiness while maintaining compliance with frameworks like NIST, ISO, and FFIEC guidelines.
Center for Internet Security (CIS) Controls
Also recommended in the FFIEC statement, CIS Controls are a prioritized list of defensive actions that provide practical guidance on reducing cybersecurity risk. While not a full framework, they can be used alongside NIST CSF and CRI to:
- Implement tactical safeguards quickly
- Support control design and gap analysis
- Complement broader assessments with technical depth
How to Transition Smoothly from FFIEC CAT
The upcoming FFIEC CAT sunset is not just a regulatory shift, but a chance to evolve. Rather than viewing this as a one-for-one tool replacement, financial institutions should use this moment to modernize and strengthen their entire information security risk management (ISRM) program.
Here’s how to make the transition purposeful and effective.
Use the Sunset as a Strategic Inflection Point
Moving away from the FFIEC CAT allows you to step back and rethink your cybersecurity and risk management approach from the ground up. This is your chance to:
- Reassess current tools and workflows
- Reevaluate the identification, tracking, and remediating of cyber risks
- Build a future-proof ISRM program grounded in continuous improvement and real-time insight
Rather than replicating a legacy framework, adopt a more adaptive, integrated model, aligned to NIST CSF 2.0, CISA’s Cybersecurity Performance Goals, and your institution’s actual risk profile.
Automate and Centralize Cybersecurity Workflows
The FFIEC CAT tool was dependent on manual spreadsheets, emails, and siloed processes. A successful transition means replacing these fragmented tasks with:
- Automated assessment delivery and scoring
- Centralized risk registers, tied to assets and vendors
- Real-time dashboards that track maturity and control performance
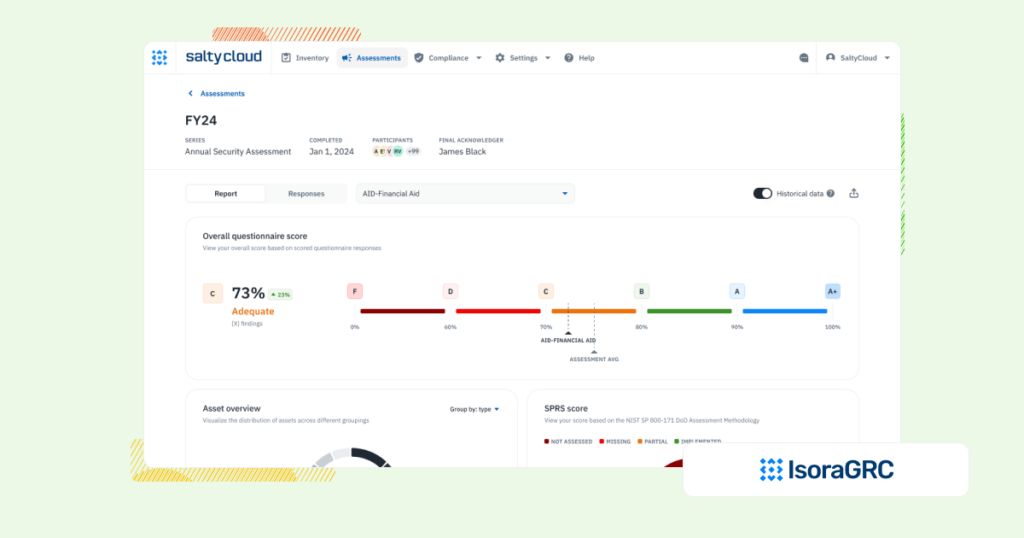
NIST CSF compliance software, such as Isora GRC, offer a perfect path forward, combining assessment management, asset/vendor inventories, and risk tracking into a single, collaborative platform that’s designed for security teams.
Align Security With Business Objectives
Modern cybersecurity frameworks like NIST CSF 2.0 emphasize the need for alignment between information security strategy and organizational goals. That requires more than just control checklists. It requires clarity on:
- Where cyber risks intersect with critical business functions
- How to prioritize remediation based on impact
- What cybersecurity maturity looks like in practical, measurable terms
Making this shift will position your institution not only to meet evolving compliance expectations but also to improve resilience, governance, and operational decision-making.
How Isora GRC Helps with the FFIEC CAT Transition
As the FFIEC retires the Cybersecurity Assessment Tool (CAT), financial institutions need more than a new template—they need a complete system for managing cyber risk in line with modern frameworks and regulatory expectations.
Isora GRC provides that system. Built specifically for cybersecurity teams, Isora helps institutions transition from the static, manual structure of the CAT to a dynamic, risk-aligned approach that supports frameworks like NIST CSF 2.0, the CRI Profile, and CISA CPGs.
Structured, Repeatable Assessments Aligned to Modern Frameworks
Isora GRC replaces static templates with customizable, logic-driven assessments. Institutions can map their assessments directly to NIST CSF, CRI Profile, or internal security objectives, allowing them to:
- Run structured cybersecurity assessments across departments or business units
- Track responses, participation, and scoring in real time
- Identify maturity gaps using built-in models and customizable scoring logic
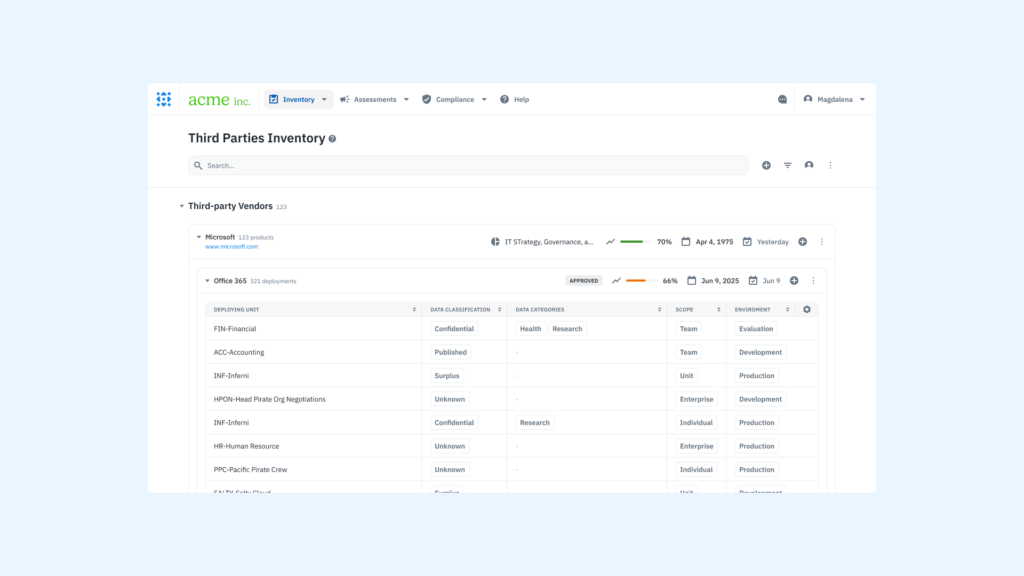
Centralized Risk, Asset, and Vendor Visibility
With Isora, institutions no longer need to manage cybersecurity data in isolation. Assessment results, risk items, and inventory data all live in one platform:
- Risk Register: Track risks from identification to remediation, with full traceability back to assessments
- Inventory Management: Maintain up-to-date inventories of assets, applications, and vendors, linking each to their associated risks and assessments
- Third-party Risk Management: Automate vendor security questionnaires and map responses to cybersecurity performance goals
Automation That Replaces Manual Workflows
Isora eliminates the administrative drag of traditional assessment and reporting processes:
- Send recurring assessments and reminders on a defined schedule
- Route responses for review and signoff with built-in approval workflows
- Instantly generate scorecards and reports aligned to NIST CSF or institutional benchmarks
Built for Adoption Across the Organization
Legacy GRC platforms are often too bloated or complex to roll out effectively. Isora is different—intuitive for users, fast to deploy, and flexible enough to scale:
- Intuitive UX: Easy for both technical and non-technical users to participate
- Cross-functional: Supports internal departments and external vendors
Fast deployment: Launch in weeks with prebuilt templates mapped to FFIEC and NIST expectations

Replacing the FFIEC Cybersecurity Assessment Tool FAQs
What will replace the FFIEC CAT?
The FFIEC CAT will be retired on August 31, 2025. Financial institutions should prepare to adopt either the NIST Cybersecurity Framework (CSF) 2.0 or the Cyber Risk Institute (CRI) Profile. These modern frameworks provide more flexibility, align better with regulatory expectations, and support improved cybersecurity risk management.
What is the NIST Cybersecurity Framework (CSF) 2.0?
NIST CSF 2.0 is the updated version of the NIST Cybersecurity Framework. It offers a flexible, risk-based approach to managing cyber risk using five core functions: Identify, Protect, Detect, Respond, and Recover. Version 2.0 adds performance goals and expanded guidance, making it ideal for institutions replacing the FFIEC CAT and improving resilience.
What is the CRI Profile?
The CRI Profile is a cybersecurity assessment framework tailored to the financial sector. Built on the NIST CSF, it helps institutions assess cyber preparedness while aligning with regulatory expectations. It enables structured assessments, clear documentation, and actionable insights—making it a strong, sector-specific alternative to the FFIEC CAT.
How should our institution choose between NIST CSF 2.0 and the CRI Profile?
Choose NIST CSF 2.0 for broad, scalable cybersecurity management across your organization. Opt for the CRI Profile if you need sector-specific alignment with financial regulatory expectations. Many institutions use both—leveraging NIST CSF 2.0 for internal strategy and the CRI Profile for compliance and supervisory reporting.
Can we still use the FFIEC CAT before the deadline?
Yes, financial institutions can use the FFIEC Cybersecurity Assessment Tool until it is retired on August 31, 2025. However, since it won’t be updated, continued use may lead to risk visibility gaps and misalignment with evolving cybersecurity regulations.
How can we transition off the FFIEC CAT without disrupting compliance?
Start by mapping your current assessment to NIST CSF 2.0 or the CRI Profile. Use tools with automated workflows, centralized reporting, and continuous monitoring. A structured, forward-looking approach ensures a smooth transition while strengthening your cybersecurity posture and compliance maturity.
How does this transition affect regulatory audits and oversight?
Regulators recognize NIST CSF and the CRI Profile. Transitioning off the FFIEC CAT helps improve audit readiness, documentation quality, and alignment with supervisory expectations—especially if your process shows measurable cybersecurity maturity and continuous improvement.
What happens if we don’t replace the FFIEC CAT by the sunset date?
Continuing to use the FFIEC CAT after August 31, 2025, increases risk exposure. The tool won’t be maintained, and regulators may flag gaps in cybersecurity maturity and documentation. Transitioning to NIST CSF 2.0 or the CRI Profile ensures ongoing compliance and resilience.
Does the FFIEC endorse any specific replacement for the CAT?
No, the FFIEC does not endorse a specific tool but recommends frameworks like NIST CSF 2.0, CRI Profile, CIS Controls, and CISA’s CPGs. Institutions are expected to choose cybersecurity tools suited to their size, complexity, and risk profile.
Is the NCUA ACET still supported after the FFIEC CAT sunset?
Yes, the NCUA will continue to support the ACET for credit unions. While based on the FFIEC CAT, ACET is independently managed and remains available as a voluntary self-assessment tool through the NCUA website.
Can we use an IT Security Risk Management platform to manage the transition?
Yes. Platforms like Isora GRC simplify the transition from FFIEC CAT by supporting NIST CSF 2.0 and CRI Profile, automating workflows, and offering real-time risk reporting. This approach reduces disruption and improves visibility into cyber risk and compliance readiness.
This content is for informational purposes only and does not constitute legal or compliance advice. See our full disclaimer.