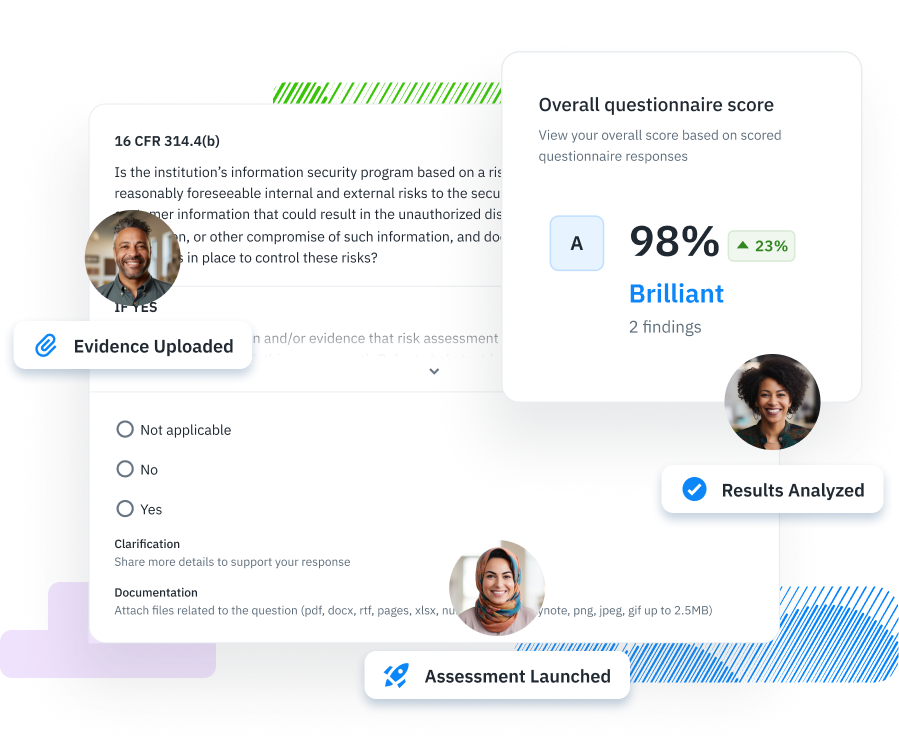
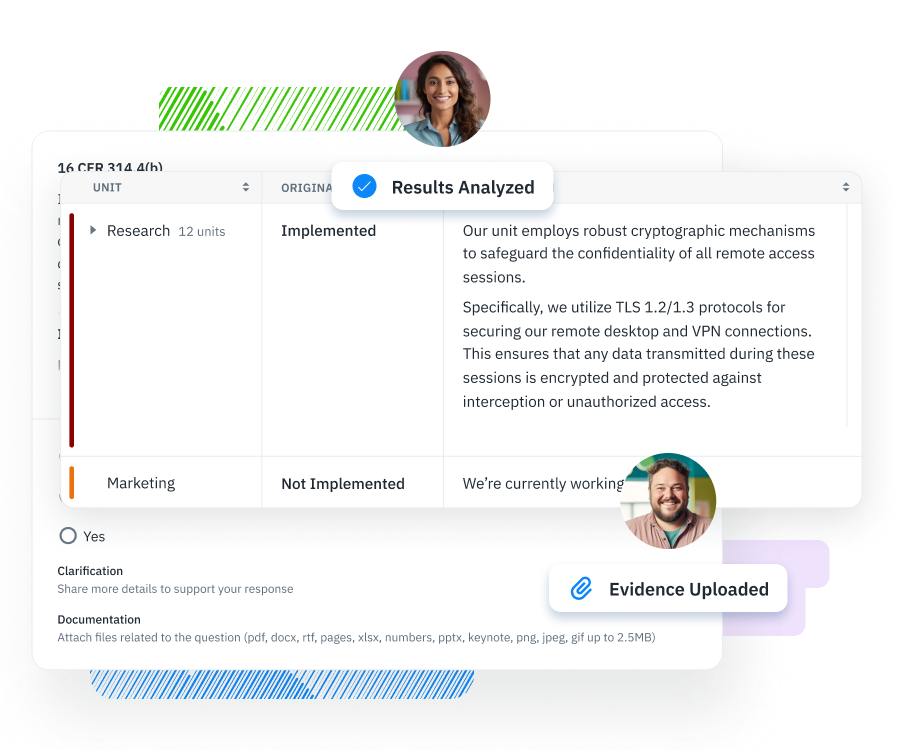
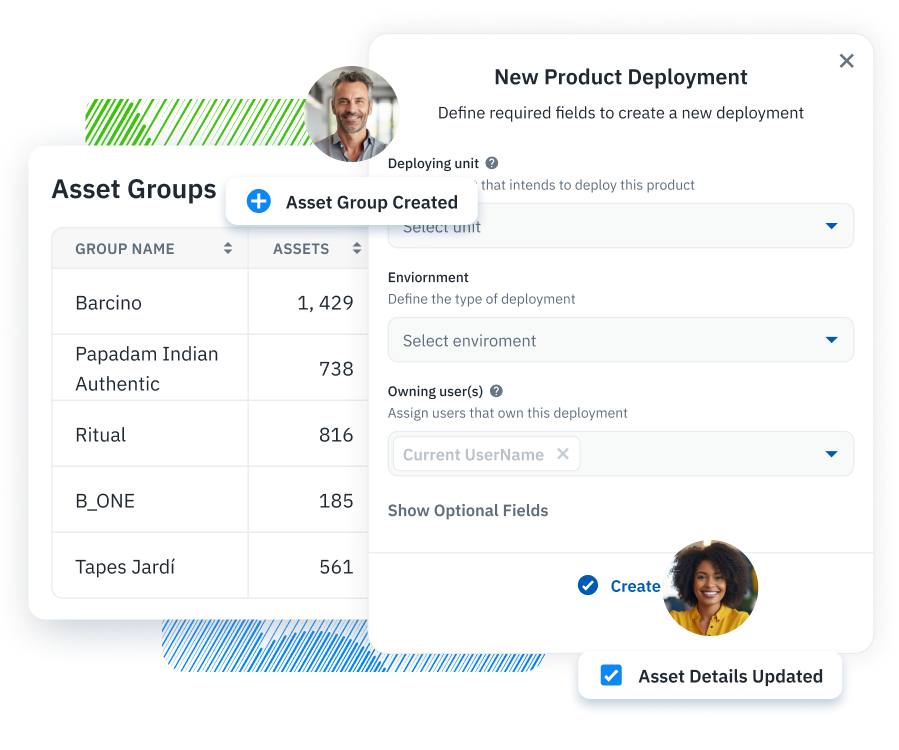
The GLBA Safeguards Rule mandates financial institutions to protect the confidentiality and integrity of consumer financial information. It requires these institutions to conduct thorough information security risk self-assessments, implement specified safeguards to address identified risks, and ensure the security of consumer information when dealing with third-party vendors. The rule emphasizes developing, implementing, and maintaining a comprehensive information security program, tailored to the size and complexity of the institution, to manage risks effectively and safeguard sensitive consumer information against unauthorized access or threats.
 Cyber Resilience in Higher Education, 2024 Guidebook
Cyber Resilience in Higher Education, 2024 Guidebook