Welcome to the 2024 edition of our Complete Guide, Understanding the Gramm-Leach-Bliley (GLBA) Safeguards Rule. In addition, you may also reference two supplemental Complete Guides related to the GLBA:
Introduction
As cyber threats persistently evolve, financial institutions are tasked with staying abreast of regulatory shifts designed to protect consumer data. Originating from the Federal Trade Commission (FTC) in 1999, the Gramm-Leach-Bliley Act (GLBA) underwent substantial updates that took effect on June 9, 2023. In light of these amendments, financial organizations must recalibrate their practices to maintain compliance or risk incurring penalties.
This comprehensive guide from SaltyCloud equips you with essential insights into the GLBA Safeguards Rule, including its most recent updates, to help you successfully navigate regulatory audits.
Understanding the Basics
What is the Gramm-Leach-Bliley Act (GLBA)?
The Gramm-Leach-Bliley Act (GLBA) is federal legislation that mandates financial institutions to be transparent about their information-sharing practices and to take robust measures to secure sensitive consumer data. In the context of GLBA, financial institutions are defined as organizations offering consumer-focused financial products or services, such as loans, investments, financial advice, and insurance.
The GLBA is organized into three core sections:
- The Financial Privacy Rule: This portion outlines the parameters for collecting and disclosing consumer’s private financial information. It obligates financial institutions to inform consumers about their data collection practices and how that information may be shared or used.
- The Safeguards Rule: This section mandates financial institutions to establish comprehensive security and risk assessment programs designed to protect consumer information. These programs are expected to be thorough and tailored to the size and complexity of the organization.
- The Pretexting Provisions: These clauses explicitly prohibit the practice of pretexting, defined as the act of obtaining private information through deceptive or false pretenses.
What is the Safeguards Rule?
The GLBA Safeguards Rule is a regulatory framework that mandates financial institutions to implement comprehensive security measures for protecting customer data. Originally established in 2003 and known formally as the Standards for Safeguarding Customer Information, the rule outlines a multi-layered approach involving administrative, technical, and physical safeguards. Its primary goal is to ensure the security and privacy of customer information. The Federal Trade Commission (FTC) most recently updated these guidelines on December 9, 2021, with the amendments, termed the Final Rule, becoming effective on June 9, 2023.
The GLBA Safeguards Rule is a regulatory framework that mandates financial institutions to implement comprehensive security measures for protecting customer data.
These recent updates include several key changes:
- Enhanced Guidance: The Final Rule offers more detailed guidelines to help financial institutions create and sustain a robust information security program.
- Exemptions: Organizations holding fewer than 5,000 consumer records are now exempt from these requirements, providing some relief for smaller institutions.
- Clarifications and Examples: The amendments include definitions of various terms and furnish practical examples to aid in interpretation and implementation.
Even if the original Safeguards Rule did not apply to your organization, changes in your business operations over recent years could now make it relevant. Therefore, it’s advisable to routinely check the FTC’s definition of a “financial institution” to ascertain whether your organization falls under the scope of this regulation.
Who needs to comply with the GLBA Safeguards Rule?
The term “financial institutions” covers a broad range of organizations, extending beyond traditional banks. According to the Gramm-Leach-Bliley Act (GLBA), a financial institution includes any company offering financial products or services to consumers, like loans, investment advice, or insurance.
The term “financial institutions” covers a broad range of organizations, extending beyond traditional banks.
According to 16 CFR 314.2(h), the following entities are obligated to comply with the GLBA Safeguards Rule:
- Retailers Issuing Credit Cards: Businesses that issue their own credit cards directly to consumers.
- Automobile Dealerships: Dealerships that lease automobiles on a non-operating basis for longer than 90 days.
- Property Appraisers: Personal property and real estate appraisers.
- Career Counselors: Specializing in career services for people in finance-related sectors.
- Check Printing Businesses: Companies that print and sell checks to consumers.
- Money Transfer Services: Businesses that wire money to and from consumers regularly.
- Check Cashing Businesses: Those that cash checks, participating in the exchange of money.
- Tax Preparation Services: Accountants or other services in the business of completing income tax returns.
- Travel Agencies in Financial Services: Operating a travel agency in connection with financial services.
- Real Estate Settlement Services: Entities providing real estate settlement services.
- Mortgage Brokers: Involved in brokering loans, especially for real estate.
- Investment and Credit Counseling Services: Advisory companies in investment or credit counseling.
- Finders: Companies acting as intermediaries in transactions between buyers and sellers.
- Title IV Higher Education Institutions: Schools that are eligible to administer federal student aid programs, which often includes disbursing loans and grants to students.
Importantly, even if your organization aligns with the definition of a financial institution, it may be exempt from certain requirements if it maintains fewer than 5,000 consumer records.
Whom does the GLBA Safeguards Rule protect?
The Safeguards Rule aims to secure “customer information,” which encompasses data collected from consumers while providing financial services, whether they are past or current customers.
For customers, the security and privacy benefits of complying with the GLBA Safeguards Rule are:
- Protection against unauthorized access to their private information.
- The ability to be notified and opt out if their information is being shared between financial institutions and third parties.
- Monitoring of user activity, including any attempts to access their secured records.
For financial institutions, adhering to the GLBA Safeguards Rule isn’t just a regulatory requirement; it’s a business imperative. Compliance reduces the risk of incurring reputational damage or financial penalties that can result from the unauthorized sharing or loss of consumer data. Moreover, it serves to bolster customer trust, as organizations can assure consumers that their sensitive information is being handled with the utmost security and care.
What are the penalties for GLBA noncompliance?
Failure to comply with the GLBA Safeguards Rule has serious financial and legal implications. Financial institutions risk fines up to $100,000 per violation, and officers and directors can be personally fined up to $10,000. Imprisonment for up to five years is also on the table. These financial and legal consequences are further compounded by a loss of customer trust and heightened security vulnerabilities.
Failure to comply with the GLBA Safeguards Rule has serious financial and legal implications.
Examples of notable GLBA noncompliance cases include:
- Ascension Data and Analytics, LLC (2020): Settled with the Federal Trade Commission (FTC) over insecure cloud storage of customer data.
- LightYear Dealer Technologies, LLC (2019): Settled FTC allegations after failing to secure consumer data, leading to a breach affecting millions of customers.
- Equifax, Inc. (2019): Agreed to a settlement ranging between $575 million and $700 million after allegations of network security failures.
- PayPal, Inc. (2018): Fined $175,000 by the state of Texas for GLBA and Federal Trade Act violations related to its Venmo app.
- TaxSlayer (2015): Cited by the FTC for compromised security affecting nearly 9,000 customer records; restricted from violating GLBA rules for 20 years and mandated to undergo biennial third-party assessments for 10 years.
The gravity of these penalties highlights the critical importance of understanding and adhering to the GLBA Safeguards Rule. Compliance is not just a legal requirement but also an imperative for maintaining customer trust and operational integrity.
If a GLBA noncompliance allegation is proven, the ramifications can be business-altering, and in some cases, life-altering.
According to section 523 of the GLBA, noncompliance penalties include:
- Fines of USD$100,000 per violation for financial institutions found in violation
- Fines of USD$10,000 per violation for individuals found in violation
- Criminal penalties including imprisonment for up to 5 years for individuals found in violation
GLBA Safeguards Rule Compliance Checklist
Develop, Implement, and Maintain a Robust Information Security Program
According to 16 CFR 314.3, organizations in the financial sector must develop a written, comprehensive information security program that encapsulates administrative, technical, and physical measures. These measures should be tailored to your organization’s unique characteristics, such as its size, complexity, and the sensitivity of the information it handles. The program’s primary objectives are:
- Ensuring the confidentiality of consumer information,
- Defending against threats to information integrity, and
- Preventing unauthorized access that could harm or inconvenience customers.
Furthermore, according to 16 CFR 314.4, there are nine crucial elements for achieving these objectives:
Element 1: Designate a Security Expert
Appoint a qualified individual to oversee your information security program. While the law isn’t prescriptive, an individual in possession of credentials like the CISSP certification is advisable. Senior staff should supervise this individual’s activities.
Element 2: Conduct Regular Risk Assessments
Perform a formal GLBA Safeguards Rule risk assessment either semi-annually or annually. Start by locating where your protected data resides and identify who is responsible for its security. Then, utilize security frameworks like NIST CSF, NIST 800-171, NIST 800-53, CIS,ISO 27001, and others, to conduct questionnaire-based risk identification. Document identified risks in a centralized risk register for easy tracking and presentation during audits.
Element 3: Put Data Safeguards in Place
Implement controls that are specifically designed to mitigate identified risks. Key safeguards include:
- Access Controls: Regularly verify who has access to customer data and their legitimate business need for it.
- Inventory Management: Familiarize yourself with your company’s data infrastructure. Regular data inventories and understanding the path of data—from collection to storage to transmission—is pivotal.
- Data Encryption: Ensure encryption of customer data, both at rest and in transit. If encryption is unfeasible, alternative robust measures should be in place.
- Application Assessment: Establish procedures for routinely assessing the security of in-house and third-party applications that come into contact with customer data, via an Application Risk Management and Third-Party Security Risk Management program.
- Multi-Factor Authentication (MFA): MFA should be a prerequisite for anyone accessing sensitive data. This requires at least two out of the following: a password, a physical token, biometric verification, or an equally secure method.
- Secure Disposal: After two years from its last use, ensure secure disposal of customer data. Regularly revisiting data retention policies can help avoid unnecessary data storage.
- Change Management: Having policies that anticipate and evaluate shifts in your IT infrastructure is crucial.
- Access Monitoring: Regularly oversee authorized data access and have tools in place to detect any unauthorized intrusions.
Element 4: Regular Testing of Safeguards
Adopt a regimen of both ongoing monitoring and structured tests, such as annual penetration tests and regular vulnerability assessments.
Element 5: Empower Through Training
Provide frequent security awareness training. For those directly involved in your security program, specialized sessions are crucial.
Element 6: Oversee Third-Party Security
Select service providers who can maintain appropriate safeguards and require them to implement those safeguards effectively. Having a Third-Party Security Risk Management program is advisable.
Element 7: Stay Agile and Updated
Your security program needs to be as dynamic as the threats it aims to combat. Make adjustments based on the latest risk assessments and security tests.
Element 8: Prepare for Incidents
Draft a comprehensive incident response plan that defines roles, communication strategies, and post-incident analyses.
Element 9: Keep the Board in the Loop
Present an annual report, at minimum, to the board or governing body. This report should summarize your compliance standing, risk assessment outcomes, and any security incidents, along with recommendations for future action.
The role of GLBA compliance software
GLBA compliance software embodies a suite of features and components designed to facilitate, streamline, and automate the process of complying with the Safeguards Rule under the Gramm-Leach-Bliley Act (GLBA), with a specific focus on information security risk management. This software simplifies complex compliance requirements by offering functionalities such as:
- Risk assessment management and a risk register (314.4(b)): Tools that support the systematic identification, evaluation, and documentation of risks to consumer financial information, aiding in the development and upkeep of a comprehensive risk register.
- IT asset and third-party vendor inventory management (314.4(c)(2)): Capabilities that enable the detailed tracking and categorization of IT assets and third-party vendors, assessing their significance and associated risks to prioritize security efforts effectively.
- Third-party vendor management (314.4(f)): Features focused on the governance and evaluation of third-party service providers, ensuring their security measures meet the organization’s standards and comply with GLBA regulations.
- Compliance and risk reporting to governance bodies (314.4(i)): Mechanisms for crafting and presenting detailed reports on compliance activities and risk assessments to boards of directors or equivalent governing bodies, facilitating informed decision-making and oversight.
GLBA compliance software embodies a suite of features and components designed to facilitate, streamline, and automate the process of complying with the Safeguards Rule under the Gramm-Leach-Bliley Act (GLBA), with a specific focus on information security risk management.
Isora GRC provides the tooling to enable your information security risk management program and meet compliance with the GLBA Safeguards Rule. Isora is a collaborative GRC platform that empowers everyone to own risk together, with user-friendly and flexible tools. With Isora, teams can stay agile and responsive to growing changes, fostering a resilient culture across the organization.
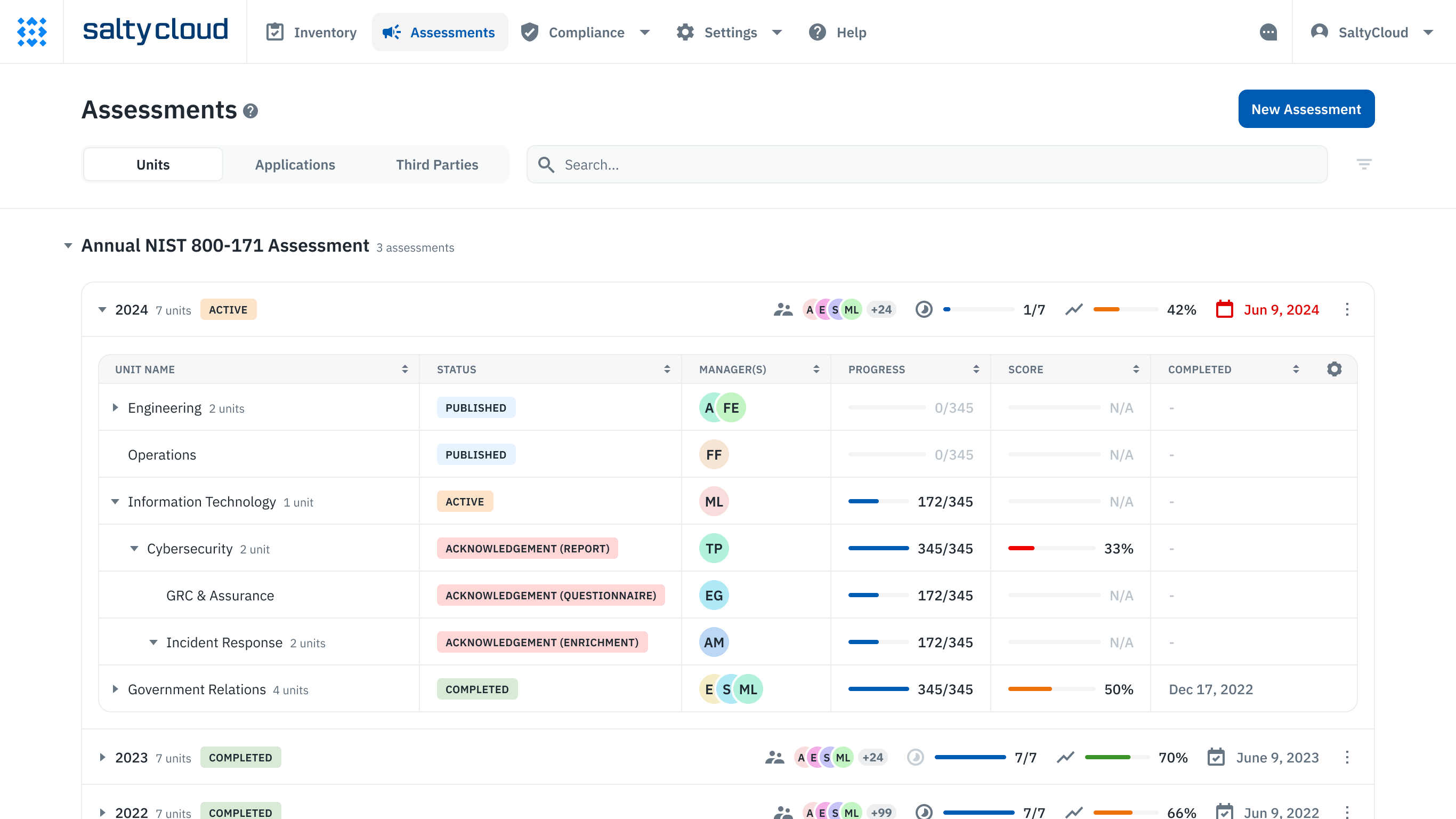
Information security risk assessment management on Isora GRC
Conclusion
In conclusion, the GLBA Safeguards Rule demands that financial institutions conduct risk assessments and establish information security programs to protect consumer data. These steps are crucial for compliance with federal regulations and for strengthening data protection. By adhering to these requirements, organizations ensure the security of consumer information and maintain customer trust.
Enhanced security
Manage GLBA compliance confidently
Work together in Isora to keep customer data safe and build trust
Learn More
 Cyber Resilience in Higher Education, 2024 Guidebook
Cyber Resilience in Higher Education, 2024 Guidebook





 Table of Contents
Table of Contents


 Other Relevant Content
Other Relevant Content 